Cross Site Request Forgery Vulnerability in Avira License Web-Application
Cross Site Request Forgery Vulnerability in Avira Application
Yesterday morning the independet researcher Mazen Gamal discovered a vulnerability inside of the well know avira company license web-application. The issue has been reported by the vulnerability laboratory to the avira company. The avira developer team patched the vulnerability by an easly solution within 6hours after the report has been arrived. In the last year the core team researcher ebrahim hegazy discovered multiple vulnerabilities in the avira license web-application infrastructure.
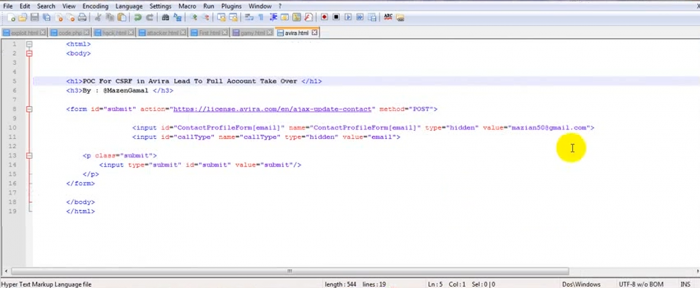
The license account system web server of avira uses unvalidted tokens without protection against cross site request forgery attacks. The researcher discovered an exploit with a POST method request to unauthorized capture session information of an avira user account on interaction. The target user with the non expired session can be redirected to a malicious webpage to steal the account information. After the account information has been captured the attacker can silently login by usage of the compromised session information. The problem is located in the `ajax-update-contact` module of the avira license web-application request.
The security risk of the csrf vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.4. Exploitation of the cross site request forgery vulnerability requires no privileged application user account but medium or high user interaction. Successful exploitation of the cross site request forgery issue results in account theft.
Request Method(s):
[+] POST
Vulnerable Service(s):
[+] Avira - Web Application
Vulnerable Function(s):
[+] ajax-update-contact
Affected Module(s):
[+] License Account System - Update
During the end of the little account tests he revealed a video that explains the issue to officials of the avira company.
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1302
Video: http://www.vulnerability-lab.com/get_content.php?id=1301



Add new comment