Barracuda Networks patched BNSEC-2398 Bulletin in Firewall Appliance Application
Barracuda Networks patched BNSEC-2398 Bulletin in Firewall
The Barracuda Networks firewall moves beyond traditional network security appliances and firewalls or UTMs by providing powerful network security, granular layer 7 application controls, user awareness and secure VPN connectivity combined with cloud-based malware protection, content filtering and reporting. Barracuda Networks is part of the APL (Approved Product List) and provides the newst security filter service and firewalls to public and private customers.
The vulnerability laboratory released in the morning a new zero-day vulnerability in the Barracuda Networks Firewall appliance web-application. The issue has been discovered to the Barracuda Networks Security Team during the pentests in the official bug bounty program. The vulnerability has been reported by Benjamin Kunz Mejri the CEO of the vulnerability laboratory and owner of the evolution security company. The issue was coordinated disclosed to the public with an official security bulletin of the barracuda labs team in the knowledgbase for all clients/customers.
2013-09-26: Researcher Notification & Coordination (Benjamin Kunz Mejri)
2013-09-27: Vendor Notification (Barracuda Networks Security Team - Bug Bounty Program)
2013-09-30: Vendor Response/Feedback (Barracuda Networks Security Team - Bug Bounty Program)
2014-06-30: Vendor Fix/Patch (Barracuda Networks Developer Team) [Coordination: Dave Farrow] (Fixed in all Appliances!)
2014-07-23: Public Disclosure (Vulnerability Laboratory)
Technical Details of the Vulnerability:
The vulnerability was located in the `VPN > Certificates` module when processing to request via POST to GET method manipulated `cert_error` values through the secure appliance application exception-handling. The script code execution occurs in the main header on top of the error message (exception-handling). The issue impact a persistent and non-persistent attack vector because of the values can be exploited in the regular service GET method request in the referer on the client-side. The second technique is to exploit by inject via POST method request to provoke an error (exception) with specific manipulated context.
The attacker moves to the certificates area and uploads even in the restricted mode 2 pem certs, he tampers the request and exchange the upload path but drops also an invalid value to the name. The application will respond via GET and drops an unknown error message in the exception-handling of the module. The attacker is able to change the referer and includes his own code to the affected parameters. The result is a client-side execution in the first exception message body context.
Now the links in the main website will change to the error link with referer through application-side. The attacker is now able to click the link or request the url to execute the code inside of the exception-handling contents`>Error message with persistent attack vector.
The security risk of the persistent and non-persistent input validation vulnerability and fitler bypass is estimated as medium with a cvss (common vulnerability scoring system) count of 5.7. Exploitation of the persistent web vulnerability requires low user interaction and a local low privileged (restricted) web-application account. Successful exploitation of the vulnerability results in application-side session hijacking (customers), account theft via persistent web attacks, persistent phishing, persistent external redirects and persistent manipulation of affected or connected module context.
Request Method(s):
[+] POST & GET
Vulnerable Module(s):
[+] VPN > Certificates
Vulnerable Parameter(s):
[+] cert_error (contents:error)
Affected Module(s):
[+] Exception Handling - Error Message
Proof of Concept (PoC):
The input validation vulnerability in the exception-handling can be exploited by remote attackers with low privileged web-application user account and low user interaction. For security demonstration or to reproduce the vulnerability follow the provided steps and information below to continue.
1. You need to request the regular module ...
https://firewall.localhost:8080/cgi-bin/index.cgi?&et=1380384291&locale=...
2. Provoke an error inside of the regular protected exception-handling via upload pem:
https://firewall.localhost:8080/cgi-bin/index.cgi?&et=1380384291&locale=...
3. After the redirect with the url to the error happened the attacker is able to change the exception input variable to execute own codes
https://firewall.localhost:8080/cgi-bin/index.cgi?&et=1380384291&locale=...
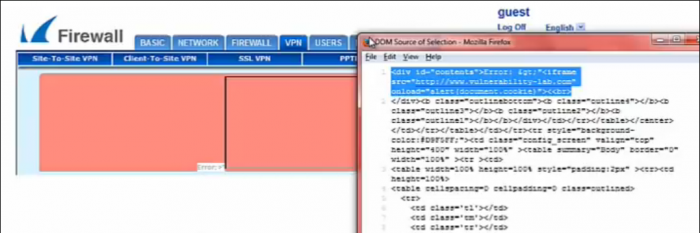
PoC: Exception Handling - Error Message
<tr><td><table id="status_screen" class="status_screen"><tbody><tr><td><center><table class="status_module"
cellpadding="0" cellspacing="0"><tbody><tr><td><div id="error"><b class="outlinetop"><b class="outline1"></b>
<b class="outline2"></b><b class="outline3"></b><b class="outline4"></b></b><div
id="contents">Error: >"<[MALICIOUS INJECTED SCRIPT CODE!])"><<br>
</div><b class="outlinebottom"><b class="outline4"></b><b class="outline3"></b><b class="outline2"></b>
<b class="outline1"></b></b></div></td></tr></table></center></td></tr></table></td></tr><tr style="background-color:#D9F5FF;">
<td class="config_screen" valign="top" height="400" width="100%" ><table summary="Body" border="0" width="100%" ><tr ><td>
<table width=100% height=100% style="padding:2px" ><tr><td height=100%>
<table cellspacing=0 cellpadding=0 class=outlined>
<tr>
<td class='tl'></td>
<td class='tm'></td>
<td class='tr'></td>
</tr>
Live Security Demonstration to Barracuda Networks in cooperation with the managers eric and the well known dave farrow.
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1102
Video: http://www.vulnerability-lab.com/get_content.php?id=1210
Bulletin: https://www.barracuda.com/support/knowledgebase/501600000013m1P



Add new comment