Local Command Inject Vulnerability discovered in iScan Online Mobile v2.0.1 (iOS)
Local Command Inject Vulnerability discovered in iScan Online Mobile v2.0.1 (iOS - Apple)
Yesterday the Vulnerability Laboratory Research Team discovered a local command inject web vulnerability in the official IScan Online Mobile v2.0.1 iOS web-application.
The iscan software checks if your iOS device has been jailbroken, scans standard apps for manipulation, misconfigurations, makes a proof of the firmware version.
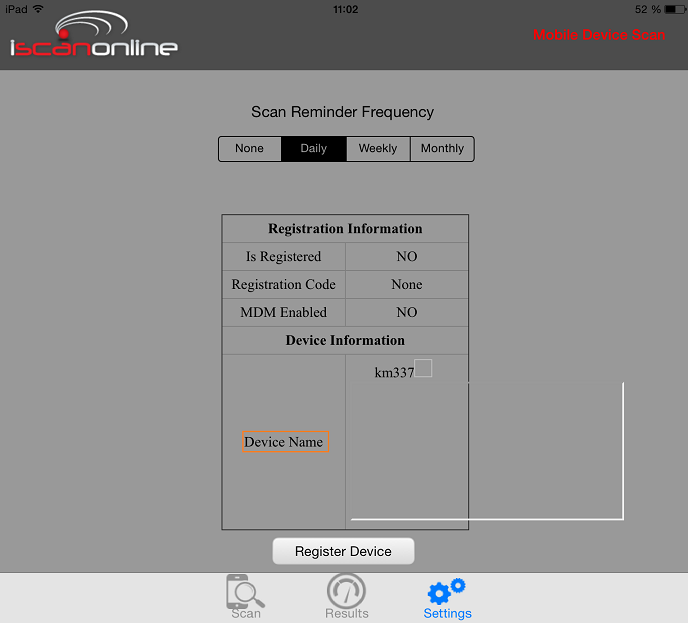
The vulnerability is located in the vulnerable `devicename` value of the `Settings` module. Local attackers are able to inject own malicious system specific commands or path value requests in the vulnerable `devicename` value. The execution of the local command inject occurs in the `Device Settings` module of the iscan online mobile application.
The attacker is able to manipulate the settings module of the application by preparing to change the local devicename. The encoding of the vulnerable values in the settings > registration information module is broken. The attack vector is on the application-side and the injection requires physical device access or a local low privileged user account. Local attackers are also able to exploit the filename validation issue in combination with persistent injected script codes to execute different local malicious attacks requests.
The security risk of the local command/path inject vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 6.2. Exploitation of the command/path inject vulnerability requires a low privileged iOS device account with restricted access and no user interaction. Successful exploitation of the vulnerability results in unauthorized execution of system specific commands and unauthorized path value requests to compromise the mobile iOS application or the connected device components.
The advisory document also impact a manual steps description to reproduce the local software bug.
- Login to your iOS device and download+install the mobile application ( Link )
- Change the iOS devicename (device information > settings) to the local command inject payload and save the details after the update Note: Request mobile var path or application files with local command
- Open the iscan online mobile application and click the settings button on the buttom of the app navigation
- The local command execution occurs in the `Device Name` output context of the registration information
- Successful reproduce of the local command inject web vulnerability!
At the end a manual patch information for the developer team of iscanonline has been attached by the laboratory researcher benjamin kunz mejri to prevent local exploitation.
Solution: The local command inject web vulnerability can be patched by a secure parse and encode of vulnerable "devicename" output context in the registration information (settings) module.
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1271
Reference(s): https://www.iscanonline.com



Add new comment