Hacker Injects Arbitrary Codes to Main Lead Database of Adobe Systems
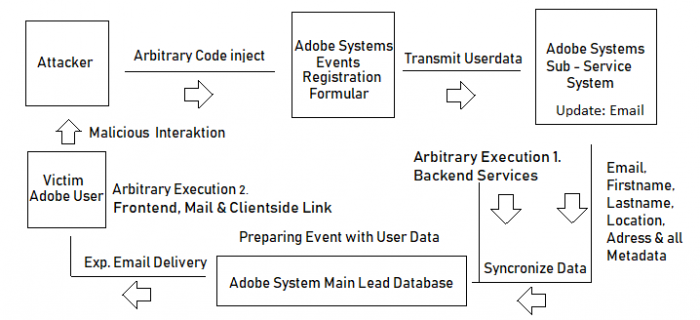
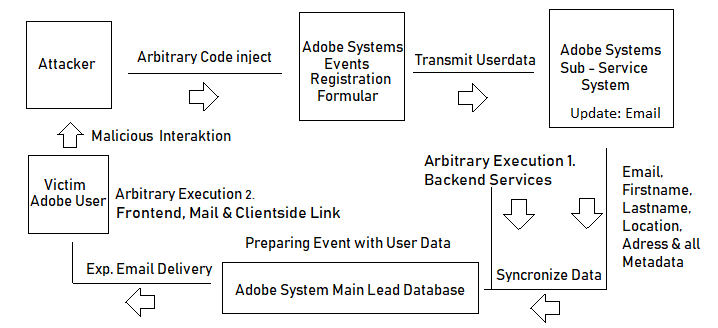
Vulnerability Affecting Main Lead Database of Adobe Systems
Within the last years the vulnerability lab core research team and individuals around the lab infrastructure discovered a lot of zero-day vulnerabilities to the psirt team of adobe system. More and more issues was resolved during the time from 2012 since 2018. The uncovered vulnerabilities in the web infrastructure was mainly focusing on sub services but as well on main entry points of the company itself. During the last week a new method of infiltration became public with a reported issue by the lab core team researcher Benjamin Kunz Mejri.
The security researcher and founder of the vulnerability lab has started to test about how executable codes can be delivered partly from database to database in the system until they do arrive in the main lead database of adobe systems. Reason for for the research was a reported unresolved issue after a longer period of time. The core team researcher continued to not smash down the ticket and began the start the communication a 2nd and 3rd time to followup. After numeros requests the root cause of the final problematic was figured out and it posed a major risk for the hole digital company infrastructure of adobe systems.
His attack began by profiling all the possible databases which are syncronised (exchange) to the main database management system of adobe systems. Then he tested with several entries who responds on which email after the registration process for events and other sub services.
After the system entry points was identified the researcher watched for a vulnerability in connection with a validation mechanism with a persistent attack vector. Thus interaction took place to bring the code inside the first event dbms by a method request. After the code was injected the theory was that the code of the users is taken from the event service to enter into the sub database of adobe systems. Then the system should take with several database syncs the user information to deliver the account holder followup information. The followup information should use the information of the basic registration process of for example the event. After some time shortly ahead to the internal exchange the content should be backuped by the adobe system databases to save to the lead database for mailings, stats and advertise purpose. Finally the code should be deeply placed inside the adobe system without triggering any fraud correlation systems or security engines.
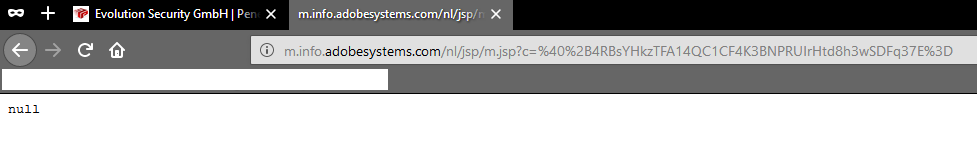
The researcher injected his code through the esmet event formular of adobe. Was waiting until the first sync and backup was done. Then he registered for the main service and replaced the name contents with payload variables. The adobe system did not recognize the wrong validated content and saved it into the sub database of the info.adobe service. From there it was taken after some time to the adobe systems main lead database. The main lead database was used by some applications to deliver with the transmitted information other data like emails for the community. At this location the final execution of the malformed code of benjamin took place.
The researcher not only bypassed several layers of security, he as well demonstrated that the contents inside the adobe system database are transmit without any protection mechanisms. The urls and the content was delivered by email and executed from the main adobe email postbox the content. The content attack is not restricted to the delivery of for example emails, the attaclk could be used in a larger range. Attacker could start client-side email phishing attempts, inject persistent phishing pages, arbitrary executions in the lead dbms or subsystems, redirect to malware or scam.
The following graphic explains complexity of the attack against adobe system in 2018 ...
The vulnerability was reported in November 2017. The 2nd and 3rd subsequent communications took place in February to April 2018. The final cause of the zero-day vulnerability was identified in May 2018 by an engineer from psirt. The engineers described the problem as critical and prepared to solve it in the 2nd to 3rd quarters of 2018. While the end users and the company were in danger, the matter was still open. The cert team prevented the attack vector temporarily by modification of a specific configuration for the malformed arbitrary requests.
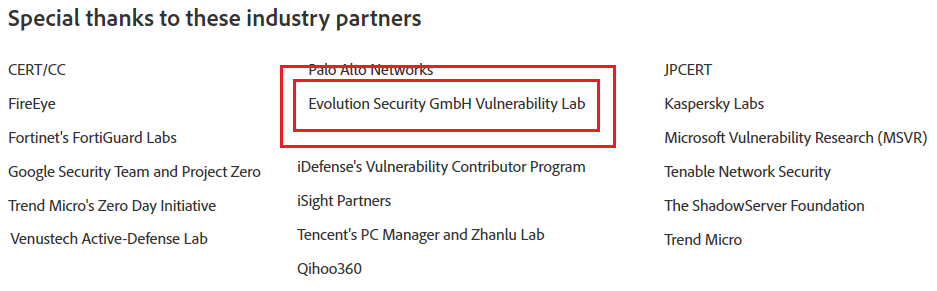
In the end, the vulnerability laboratory and evolution security gmbh team was recognized as an industry partner by adobe systems after the coordinate by the psirt engineers. We would like to take this opportunity to say thanks to adobe systems for your continued trusting cooperation and special acknowledgements.



Comments
L'attaque
Add new comment