Apple iOS v10.2 & v10.3 - SMS Reply Access Permission Vulnerability
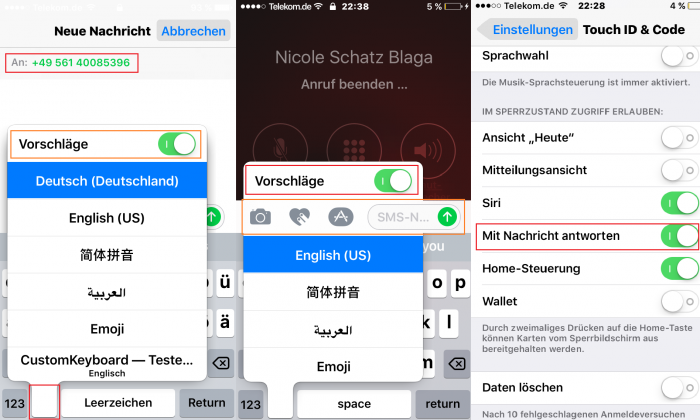
Apple iOS v10.2 & v10.3 - SMS Reply & Answer Function
During the last months we had setup a mobile forensic laboratory in our office to reproduce and uncover more new mobile zero-day vulnerabilities. Our first investigation was in a code lock functions of the settings - passcode module and the keyboard suggestion option. To explain the full impact we need to demonstrate the functionalities ago.
The "Answer with Message / Reply with message" allows a local idevice user to answer only to the caller with a customized or automated SMS one time. The function is available in the settings - touch id & code module. After activation of the setting, the idevice owner is able to answer directly to the caller by one sms.The answer as reply runs by the basic sms function over the provider and can generate costs.
The second function we would like to mention is the keyboard quicktype & suggestion function. The option is available for activation and deactivation in the settings - keyboard module. QuickType is Apple's predictive keyboard that gets smarter as you use it. Since QuickType is contextually aware of your conversation, it can even present you with an answers to common questions. And depending on who you're corresponding with, QuickType can even pick up on your conversation style. All you have to do is start using it! The quicktype with the suggestions uses apps like sms, imessage, facetime and the note app on input. Means in case of a writing the names "Frank Boldewin" or "Mark Miller" to a friend by a default iOS app (using the keyboard), the characters "Mar" or "Bol" will fully complete the name.
Both of the functions are not available by an unauthenticated idevice user for security reason. In our we previewed in our ongoing tests the security mechanisms around the two modules to uncover an access permission vulnerability at the end.
The issue allows a local attacker to bypass the code lock function to "Answer with Message / Reply with message" and limited the idevice authentication mechanism. The SMS response menu appears on the screen when it has been deactivated physically by the apple idevice user.
The first picture shows the glitch merged to the emergency call phone app without authentication or check of the access permission rights. The functional option to reply with a sms is deactivated at that time. The picture is taken of the security demonstration video located at the buttom of the page.
The second picture shows the sms mask ahead to any phone call that arrives on the idevice version 10.3. The glitch can not be removed and occurs on each call of any contact. The reply is ever delivered to the caller, even if the permission of usage is in the id touch and code module of the settings deactivated.
The keyboard suggestion module allows to glitch the mask ahead to any interaction that can be performed by the user. The mask comes up on calls, sms, imessages, facetime and co.
The function itself can not be reached from outside without authentication by the passcode. The following screens show the restricted mode in siri and on calls. Only the answer sms function allows to exploit via interaction by a local attacker because in all other modules the function is deactivated for the menu.
In siri the option is deactivated by default.
On basic sms to reply the function is as well removed or not activated of the keyboard without authentication by apple for securtiy reason.
In a video the researcher we deactivated the settings for sms on active incoming calls. Then we glitched the service with the request. However the sms menu was still available on the display screen and allows the attacker to perform several interactions like using the words to get contacts of the users like names and to unauthenticated followup with sms on active incoming calls. The events are tracked by the apple ios with several reports and unknown errors in the analysis module. The security risk of the access permission vulnerability is estimated as high with a common vulnerability scoring system count of 4.3.
Requirement(s):
- Siri activated by default
- Deactivated keyboard suggestions or tips
- Activate/Deactivate of code lock module with "Answer with Message / Reply with message" function
- Activated lock to disallow app usage from outside in locked idevice mode (Sperrbildschirm/LockScreen)
Manual steps to reproduce the vulnerability ...
1. Reset the idevice to default settings
2. Install the newest apple ios 10.2 or 10.3 version
3. Deactivate in the Settings > Keyboard > Suggestions
4. Check that siri is activated by default
5. Activate the lock to disallow app usage from outside in locked idevice mode
6. Activate the "Answer with Message / Reply with message" function
Note: After preparing and checking that the idevice is correctly setup we move into the exploitation phase
7. Call your idevice with another phone
8. Click the Message button and choose to answer with a customized message
9. Push the keyboard element and move up to the english or german keyboard
Note: At that point the incoming call can already be canceled
10. Now activate from outside without authentication the Suggestions by a push and hold ahead two seconds the home button to activate via siri api call
Note: Now a glitch occurs and shows a keyboard ahead to the lock screen
11. Cancel the sms and move into the idevice settings by authentication
12. Deactivate the "Answer with Message / Reply with message" function in the code lock module
13. Move back outside the idevice and call yourself again with another phone line
14. The sms menu comes ahead to the active incoming call and allows to unauthenticated send sms to the receiver or another mobile
15. In case of using siri again during the incoming accepted call that is accepted a sync issue occurs
Note: The sync issue allows to followup with the call even if the caller has already closed the phone line (unlimited loop - side channel)
Note: On each call the sms menu comes ahead and allows the attacker to directly send sms to anybody or the caller without permission
16. Successful reproduce of the vulnerability!
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2078
Video: https://www.vulnerability-lab.com/get_content.php?id=2079



Comments
It is always a pleasure to
permission
Add new comment