PayPal Inc published "Out of Scope Vulnerabilities" List
PayPal Inc - New "Out of Scope Vulnerabilities" List
PayPal Inc has updated the bug bounty program rules in case of the official scope and testings conditions. The upgrade impacts a list of excluded attack vectors of the official PayPal/Ebay Bug Bounty Program. The new public "out of scope" list allows researchers, exploiters and hackers to coordinate the pentests by only getting acknowledgment for real 0day vulnerability disclosure.
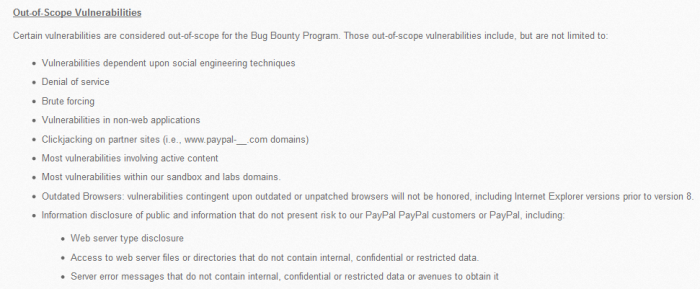
- Vulnerabilities dependent upon social engineering techniques
- Denial of service
- Brute forcing
- Vulnerabilities in non-web applications
- Clickjacking on partner sites (i.e., www.paypal-__.com domains)
- Most vulnerabilities involving active content
- Most vulnerabilities within our sandbox and labs domains.
- Outdated Browsers: vulnerabilities contingent upon outdated or unpatched browsers will not be honored, including Internet Explorer versions prior to version 8.
- Information disclosure of public and information that do not present risk to our PayPal PayPal customers or PayPal, including:
-- Web server type disclosure
-- Access to web server files or directories that do not contain internal, confidential or restricted data.
-- Server error messages that do not contain internal, confidential or restricted data or avenues to obtain it
In the last quarters the paypal inc bug bounty program had an internal overflow because of a wave of unprofessional hackers, money consultants and evil forcing blackhats which send obviously invalid/bad-detailed reports. The result was the official exclude of the minor priority problems to focus on bugs with severity medium to critical. The program cleaned the situation by going the same way like the german telekom.
URL: https://www.paypal.com/us/webapps/mpp/security-tools/reporting-security-... (Out-of-Scope Vulnerabilities)



Add new comment