PayPal Inc Bug Bounty 2015 - Stored Cross Site Vulnerability disclosed by Researcher
PayPal Inc Bug Bounty 2015 - Stored Cross Site Vulnerability disclosed by Researcher
Today one of the core team lab members discovered finally a paypal zero-day vulnerability to the public. The issue is about an application-side input validation vulnerability that allows to comprimise account credentials by manipulation of the secure payment procedure. The issue requires a low level of user interaction. The bug was finally rewarded by paypal with an amount of 750$.
Technical Details
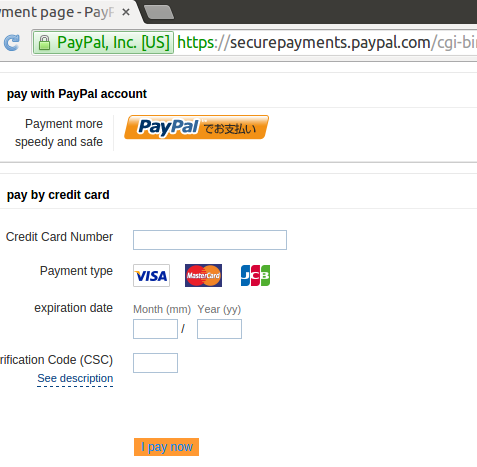
Paypal SecurePayments domain is used by paypal users to do secure payments when purchasing from any shopping site, this secure payments page require Paypal users to fill some forms that include their Credit Card number, CVV2, Expiry date and more to finalize the payment and purchase the products via their Paypal account,
The submitted data is processed through encrypted channel(HTTPS) so attackers wont be able to sniff/steal such data.
I’ve found a Stored XSS vulnerability that affects the SecurePayment page directly which allowed me to alter the page HTML and rewrite the page content, An attacker can provide his own HTML forms to the user to fullfill and send the users data back to attacker’s server in clear text format, and then use this information to purchase anything in behave of users or even transfere the users fund to his own account!
Proof of Concept
Manual steps to reproduce the vulnerability ...
1. Attacker setup shopping site or Hack into any shopping site, alter the “CheckOut” button with the Paypal Vulnerability,
2. Paypal user browse the malformed shopping site, choose some products, click on “CheckOut” button to Pay with his Paypal account,
3. User get’s redirected to https://Securepayments.Paypal.com/ to fill the required Credit Card information to complete the purchasing order, In the same page, the products price that will be paid is included inside the same page, and as we know the attacker now control this page!
4. Now when you (Paypal user) click on Submit Payment button, instead of paying let’s say “100$” YOU WILL PAY TO THE ATTACKER WHATEVER AMOUNT THE ATTACKER’S DECIDE!!
Video: PayPal Inc Bug Bounty Program 2015 - Stored Cross Site Scripting Vulnerability (Money Steal)
Video: http://www.vulnerability-lab.com/get_content.php?id=1587
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1588



Add new comment