Researcher discovers Zero-Day Vulnerability in Wordpress Plugin of Exploit DB
Researcher discovers Zero-Day Vulnerability in Wordpress Plugin of Exploit DB
The young security researcher paulos yibleo discovered a remote vulnerability in the offensive security exploit-db community.
The vulnerability occured in the blog service of the community. The offensive security team installed an application plugin for wordpress called "wp-rocket". The "wp-rocket" (wp-rocket.me) plugin is well known for unsecure programming mythology.
The security vulnerability that is remotly exploitable was located in the /wp-content/wprocketfolder/inc/front/process.php application file. The process.php file allows to request without authorization (pre-auth) $host controlled inputs.
include ($rocket_config_path . $host . '.php');
Theoretical all inputs like ../../anyfile.txt%00 would include that file from the website after manipulating the headers of $host. Those vars are predefined ...
$rocket_config_path = WP_CONTENT_DIR . '/wp-rocket-config/';
44: $host = trim(strtolower($_SERVER['HTTP_HOST']), '.');
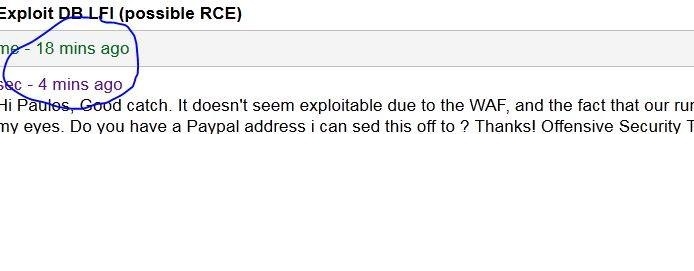
The offensive security team was already monitoring the system for active attacks. Paulos informed the exploit-db team about the issue next to that he got tracked by the monitoring service. The offensive security team acknowledged the discovered vulnerability and will pay a bounty to the researchers paypal account. The vulnerability has been patched within some hours after the researcher disclosed the information to the owner of the exploit website.



Add new comment