Facebook patched flaw within 9hours - XML Cross Domain Vulnerability
Facebook patched flaw within 9hours - XML Cross Domain
On March 25, 2014, Facebook announced that it had agreed to buy Oculus VR for $400 million in cash, $1.6 billion in Facebook stock, and an additional $300 million subject to Oculus VR meeting certain financial targets in a transaction expected to close in the second quarter of 2014.
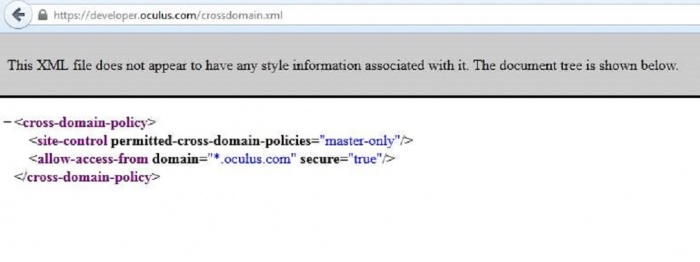
Since 2012, Oculus website has been in the bug bounty scope for Facebook Bug Bounty at facebook.com/whitehat. The security researcher, Paulos Yibelo discovered a sever flaw in the developers portal of the website (developers.oculus.com), the site was using incorrectly configured crossdomain file that could allow cross domain reads. In a less technical term, that means the ability to read the contents of any HTML file using the victim’s sessions by a simple CSRF exploit.
This is considered critical as this can be used to issue actions, read messages, read antiCSRF tokens… basically anything that is good. The technical blog article is out at BLOGPOST URL. Facebook Fixed the bug after ~1Hours of their initial reply, timeline follows as
Jan 21, 2015 6:59am - Initial Report
Jan 27, 2015 9:09am - Facebook Initial Confirmation
Jan 27, 2015 6:55pm - Fix & Bounty!
The exploit Scenario follows as:
5. Now we navigate our victim to attacker.com and as soon as the flash files runs, Boom! We get everything we need.
Reference(s):
http://www.paulosyibelo.com/2015/01/facebooks-oculus-exploiting.html



Add new comment