LizardSquad DDoS Stresser - Multiple Vulnerabilities revealed to takeover DDoS Application
LizardSquad DDoS Stresser - Multiple Vulnerabilities revealed
The core team of the vulnerability laboratory is daily watching for new web-application in the it-security sector. This week we have tested the new software of the lizard squad to discover some web-vulnerabilities. In the last days was several public announcements about the SQL Database leak of the DDoS Stresser online-service. For sure you need some 0day vulnerabilities in the application that has been revealed by the evolution security gmbh team. We did not report the issue to provoke any kind of cyberwar. We demonstrated the issues without the full proof of concepts to prevent target user damage.
1.1
The 1st vulnerability is located in `username` value of the registration module. A user can register a script code as payload to the name values. The ddos web-service of the input on registration uses the wrong conditions to encode and parse. Thus allows to execute the injected script code in the `./ref` module of the service. The request method to inject is POST and the vulnerability is located on the application-side of the ddos stresser service. The main administrators are able to see the user passwords, by watching the logs of an compromised server you see that they can switch by login in through the registered user accounts. This is possible because of plain transfered passwords in the ddos application. The known event can be used to prepare malicious code that executes function in connection with application-side injected script codes. The vulnerable file to inject the code is the register.php file. Another execution of the injected script code occurs in the main dashboard (left sidebar) were the username is getting visible.
Vulnerable Module(s):
[+] Registration (./ref)
Vulnerable Parameter(s):
[+] username
Affected Module(s):
[+] Dashboard (Username in Left Sidebar)
1.2
The 2nd vulnerability is located in the Ticket Title & Ticket Content input fields of the `Tickets` (tickets) module. A fresh registered user account is able to inject own malicious persistent script code to the ticket input fields to exploit a backend administrator account. After an attacker registers and inject own script code to the ticket system he is able to get the ip of the backend users or can compromise the session data of moderators/administrators. The inject occurs in the `./tickets` module. The execution takes place locally in the listed open ticket items of the backend. Remote attackers are also able to access other tickets and stored information by intercepting the session of the add Ticket POST method request.
Vulnerable Module(s):
[+] Tickets (./tickets)
Vulnerable Parameter(s):
[+] name (servername)
1.3
The 3rd vulnerability is located in the target server `name` value. The attacker uses the device or servername to send malicious data to the ddos application control panel. A remote attacker can change the server or device name value to a script code payload that executes in the panel (server target list). The service syncs the the device/server name value after the infection but also if the attacker syncs the data manually. In case of usage macOS to attack it is possible to change the servername easily to a malicious script code payload that affects the ddos control panel.
Vulnerable Module(s):
[+] server list
Vulnerable Parameter(s):
[+] name (servername)
1.4
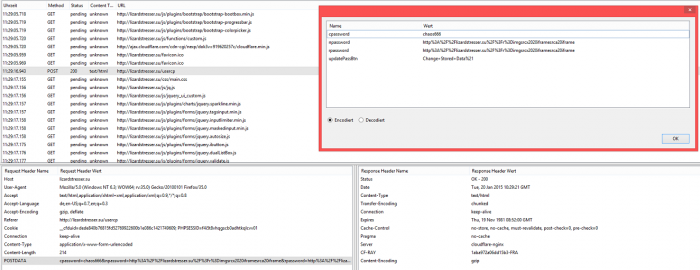
The 4th vulnerability is located in the `dasboard > user settings > change password` module. The data in the POST method to change the own account password is send in plain-text. Thus allows remote attackers and network administors to capture compromised accounts. The service can also be observed by man-in-the-middle attacks in the local network.
Vulnerable Module(s):
[+] dasboard > user settings > change password
1.5
The 5th vulnerability is also located in the `dasboard > user settings > change password` module. The POST method request of the change function in the ddos application can be intercepted by attackers to compromise the service. The remote attacker logs in as user and intercepts the session information by changing to an existing user account. Successul exploitation of the session tampering issues results in account system compromise (administrators/customers).
Vulnerable Module(s):
[+] dasboard > user settings > change password
Vulnerable Parameter(s):
[+] id
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1417



Add new comment