Sony PlayStation3 FW 4.31 – Code Execution Vulnerability
Sony PlayStation3 FW 4.31 – Code Execution Vulnerability
An amazing and historical important issue in the sony playstation 3 firmware v4.31 has been disclosed by Benjamin Kunz Mejri leader of the core research team. In 2012 Benjamin was multiple times trying to inform sony about several issues in the firmware and online ps network. After no response came back he didn't gave up to try it and contacted silently a very smart moderator and admin of the playstation3 community. The moderator (MUC) has began to read and verify the details and directly send a letter as email with the resource files to sony japan. After waiting a longer period of time the issue has been closed with the version 4.40 in may.
"There are 3 types of save games for the sony ps3. The report is only bound to the .sfo save games of the Playstation3. The ps3 save games sometimes use a PARAM.SFO file in the folder (USB or PS3 HD) to display movable text like marquees, in combination with a video, sound and the (path) background picture. Normally the ps3 firmware parse the redisplayed save game values & detail information text when processing to load it via usb/ps3-hd. The import ps3 preview filtering can be bypassed via a splitted char by char injection of script code or system (ps3 firmware) specific commands."
In the next step Benjamin explained how he was able to execute the code from the usb device in the preview listing ...
"The attacker syncronize his computer (to change the usb context) with USB (Save Game) and connects to the network (USB, COMPUTER, PS3), updates the save game via computer and can execute the context directly out of the ps3 savegame preview listing menu (SUB/HD). The exploitation requires local system access, a manipulated .sfo file, an usb device. The attacker can only use the given byte size of the saved string (attribute values) to inject his own commands or script code."
He also extended the issue with a little passage regarding the filter bypass method used to evade the filter.
"The ps3 filter system of the SpeicherDaten (DienstProgramm) module does not recognize special chars and does not provide any kind of input restrictions. Attackers can manipulate the .sfo file of a save game to execute system specific commands or inject malicious persistent script code."
Vulnerable Section(s): [+] PS Menu > Game (Spiel) Vulnerable Module(s): [+] SpeicherDaten (DienstProgramm) PS3 > USB Gerät Affected Section(s): [+] Title - Save Game Preview Resource (Detail Listing)
For security reason the poc is only restricted available to prevent sony ps3 jailbreaks, evil exploitation and manipulation of the local firmware. In the poc is the marked place of the vulnerable value were the code execution will occur.
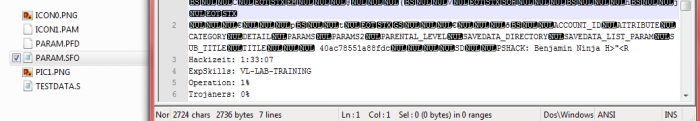
PoC: PARAM.SFO
PSF Ä @ h % , 4 $ C @ ( V h j € p t € ð ACCOUNT_ID ATTRIBUTE CATEGORY DETAIL PARAMS PARAMS2 PARENTAL_LEVEL SAVEDATA_DIRECTORY SAVEDATA_LIST_PARAM SUB_TITLE TITLE 40ac78551a88fdc SD PSHACK: Benjamin Ninja H%20'>"<[PERSISTENT INJECTED SYSTEM COMMAND TO CODE EXECUTION!] Hackizeit: 1:33:07 ExpSkills: VL-LAB-TRAINING Operation: 1% Trojaners: 0% ... Õõ~\˜òíA×éú;óç 40ac78551a88fdc ... BLES00371-NARUTO_STORM-0 HACKINGBKM 1 PSHACK: Benjamin Ninja H%20'>"<[PERSISTENT INJECTED SYSTEM COMMAND TO CODE EXECUTION!];
A tricky solution for the issue has also been provided by the laboratory researcher to make sure sony totally understand what is the problem with the embed system of ps3.
Restrict the savegame name input and disallow special chars. Encode the sfo save-game values and redisplaying in the menu preview of the game. Parse the strings and values from the savegames even if included string by string via sync. There is no proof in what way the issue has been patched but the details has been earlier included to the reported issue.
The security risk of the high exploitable but local vulnerability is estimated as critical and needs to be fixed soon. Sony addressed the issue silently around may 2013.
2012-10-26: Researcher Notification & Coordination
2012-11-18: Vendor Notification 1
2012-12-14: Vendor Notification 2
2013-01-18: Vendor Notification 3
2013-**-**: Vendor Response/Feedback
2013-05-01: Vendor Fix/Patch by Check
2013-05-13: Public Disclosure
After the issue has been patched Benjamin discovered the details at vulnerability laboratory with a lot of technical details about the vulnerability. 24h after the disclosure several news website like the register uk, daily news and softpedia realized the heavy release and published own articles about the security problem in the embed system of the sony ps3.
Advisory (Original): http://www.vulnerability-lab.com/get_content.php?id=767
Marc Ruef Scip.ch (Thx!): http://www.scip.ch/?vuldb.8811
Disclosure Mailing-List: http://seclists.org/fulldisclosure/2013/May/113
Reference(s): http://www.theregister.co.uk/2013/05/29/ps3_firmware_flaw/ http://news.softpedia.com/news/Experts-Find-Code-Execution-Flaw-in-PS3-Password-Reset-Bug-in-Sony-Entertainment-Network-356623.shtml http://playstation-techzone.com/2013/06/experts-find-code-execution-flaw-in-ps3-password-reset-bug-in-sony-entertainment-network/2



Add new comment