Apple iOS v8.0.2 - Silent Contact 0Day Vulnerability (Denial of Service)
Denial of Service Vulnerability in Apple iOS v8.0.2
Normally "Denial of Service" is a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. With Apple´s iOS v8.0.2 your iPhone or iPad can be the next target of the attack.
The discovered vulnerability allows an attacker to crash the mobile device and force a system reboot. Not really cool as an average blackhat hacker attack because this will shut down the mobile device.
But if the attacker is a regime, agency or even the police that uses a denial of service attack on mobile phones this would be a serious critical issue. In a real world scenario the mobile phones in a specific area or user group could be targeted and forced to crash/reboot. This could have a strong impact on how to communicate.
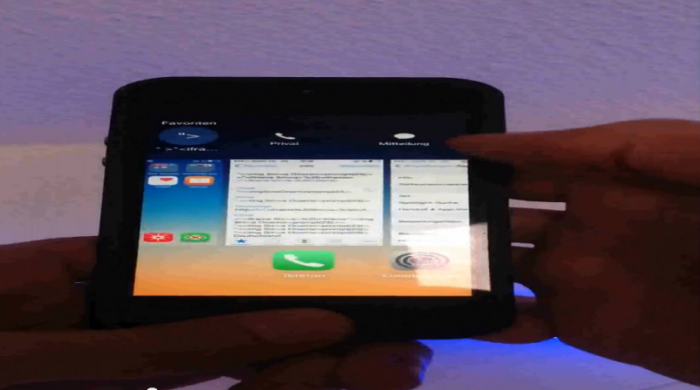
A local denial of service vulnerability has been discovered in the Apple iOS v8.0 (12A365) mobile application device system. The issue allows a local attacker to shutdown the mobile application system by a corrupt interaction with a default function. The local denial of service vulnerability is located in the favorite contact preview slideshow message button. During the tests of the new feature we included several script codes and string to evade the validation. After the manipulation of a .vcf file the researcher was able to catch a critical unhandled NSRangeException (__NSArrayI objectAtIndex).
The injected strings in the contact file (.vcf) crashs the internal message application only when processing to open the malicious contact in the favorite or history through the new preview slidebar. The bug appears to confuse the the mechanism that parses the context of the contact thats gets converted to the message and executes the code invisible like we can see in the error exception logs of the analysis tools. Even if the array shows an empty value the injected script code with the frame will return and executes. As result to prevent a deeper corruption the mobile restarts after 10 seconds during to the invalid process loop continues.
 The security risk of the local denial of service vulnerability is estimated aslow with a cvss (common vulnerability scoring system) count of 3.1. Exploitation of the local denial of service vulnerability requires a physical device access without interaction. Successful exploitation of the local denial of service vulnerability results in device shutdown and ui application crash by a corruption that causes through an unhandled (uncaught) exception.
The security risk of the local denial of service vulnerability is estimated aslow with a cvss (common vulnerability scoring system) count of 3.1. Exploitation of the local denial of service vulnerability requires a physical device access without interaction. Successful exploitation of the local denial of service vulnerability results in device shutdown and ui application crash by a corruption that causes through an unhandled (uncaught) exception.
Affected Device(s):
[+] Apple > iPhone 5 & 6
Affected OS Version(s):
[+] iOS v8.0 (12A365)
Tested Device(s):
[+] Apple iPad2, iPhone 5s & 6 > iOS v8.0 (12A365)
Proof of Concept (PoC):
The denial of service vulnerability can be exploited by local attackers with physical device access without user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manually steps to reproduce the security vulnerability ...
1. Start the mobile iOS device (ipad2, iphone 5s or iphone 6) with the new iOS v8.0
2. Import the file to the local ios contacts service
3. Call the new service one time without paying anything because the call is invalid
Note: After the call the contact becomes visible to the `history` in the task slide preview module!
It`s also possible to interact by an include to the `favority contacts` module to exploit
4. Go to the home screen of ios & press two times the home button to review the new iOS 8.0 feature with the favorites or history
5. Press the include test contact and open the message/imessage symbole
6. The application crashs with an unknown exception and the mobile shutsdown
Note: The contact can be send by imessage, email or via sms to compromise another apple ios device
7. Successful exploitation and reproduce of the local apple device denial of service vulnerability!
Video PoC: Apple iOS v8.0 - v8.0.2 - Denial of Service Vulnerability (UIAlertControlview & Invalidationhandler)
Reference(s):



Comments
Hello!
Add new comment