Apple iOS v9.2.1 - (Application Update Loop) Pass Code Bypass
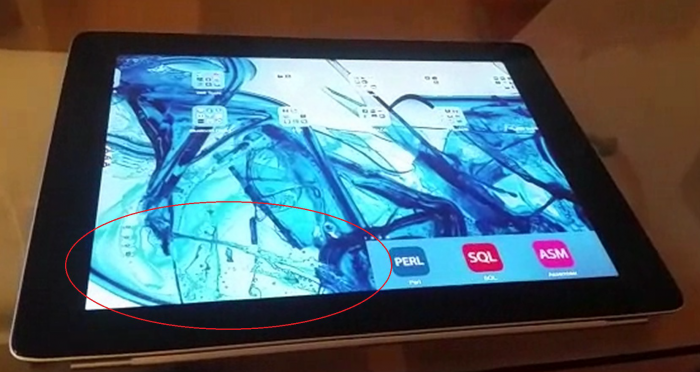
Application Update Loop allows to bypass Pass Code Protection Mechanism
The upcoming week the security researcher and ceo of the vulnerability laboratory "Benjamin Kunz Mejri" disclosed the first details about a new method to bypass the pass code protection mechanism of apple iOS devices. The pass code protects the mobile of unauthorized physical device access. The pass code is in use to secure verify the regular account pin but also the sim card pin. In 2013 and 2014 the researcher already discovered 3 different ways on how to evade the controls of the protected apple device. Today in the morning the researcher and pentester disclosed the final details on how the issue could be exploited by local and remote attackers.
The vulnerability is located in the iPad 2 & iPhone 5 & 6 hardware configuration with iOS v8.2, v9.1 - v9.2.1 when processing an update which results in a interface loop by the application slides. Local attacker can trick the iOS device into a mode were a runtime issue with unlimited loop occurs. This finally results in a temporarily deactivate of the pass code lock screen. By loading the loop with remote app interaction we was able to stable bypass the auth of an iphone after the reactivation via shutdown button. The settings of the device was permanently requesting the pass code lock on interaction. Normally the pass code lock is being activated during the shutdown button interaction. In case of the loop the request shuts the display down but does not activate the pass code lock like demonstrated in the attached poc security video.
In case of exploitation the attack could be performed time-based by a manipulated iOS application or by physical device access and interaction with restricted system user account. In earlier cases of exploitation these type of loops were able to be used as jailbreak against iOS. The vulnerability can be exploited in non-jailbroken unlocked apple iphone mobiles.
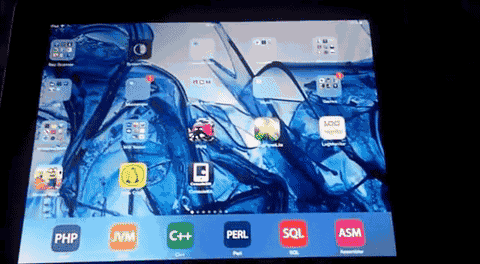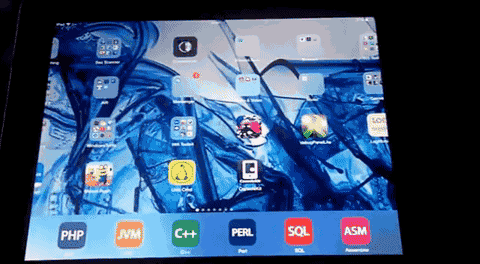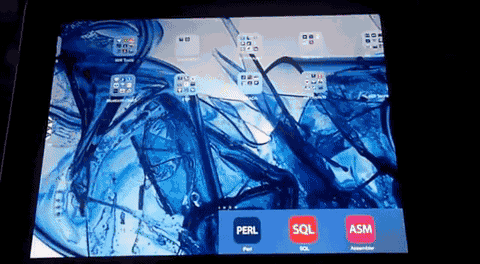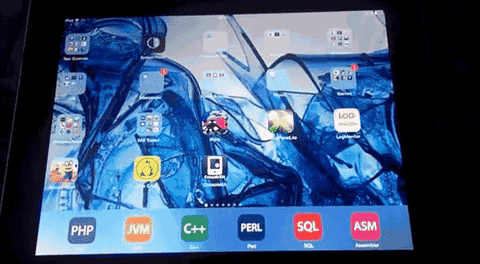
Manual steps to reproduce the vulnerability ...
1. First fill up about some % of the free memory in the iOS device with random data
2. Now, you open the app-store choose to update all applications (update all push button)
3. Switch fast via home button to the slide index and perform iOS update at the same time
Note: The interaction to switch needs to be performed very fast to successfully exploit. In the first load of the update you can still use the home button. Press it go back to index
4. Now, press the home button again to review the open runnings slides
5. Switch to the left menu after the last slide which is new and perform to open siri in the same moment. Now the slide hangs and runs all time in a loop
6. Turn of via power button the ipad or iphone ....
7. Reactivate via power button and like you can see the session still runs in the loop and can be requested without any pass code
Note: Normally the pass code becomes available after the power off button interaction to stand-by mode
8. Successful reproduce of the local security vulnerability!
Apple Followup ID: 631627909
Apple iOS v8.x & v9.x - (Application Update Loop Session) Pass Code Auth Bypass Vulnerability
In a video we demonstrate how to bypass with a unlimited loop in the interface the pass code lock settings of the iOS v9 iPad2. The issue is not limited to the device and can be exploited with iPhone as well. The power button on top activates with the stand-by mode the pass code lock for the iOS device. In case of the loop we tricked the device into a mode were we was able to bypass the pass code.
Video: http://www.vulnerability-lab.com/get_content.php?id=1711
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1710
Press Reference(s):
http://www.zdnet.com/article/most-iphone-ipad-unlocked-with-new-passcode-bypass-trick/
http://www.ubergizmo.com/2016/02/new-iphone-and-ipad-lock-screen-passcode-bypass-flaw-discovered/
https://www.grahamcluley.com/2016/02/bypass-passcode-lock-screen-ios-8-9/
http://justinsniche.com/2016/02/04/iphones-ipads-at-risk-of-new-lock-screen-passcode-bypass-flaw/
http://www.hackbusters.com/news/stories/528702-how-to-bypass-the-passcode-lock-screen-on-ios-8-and-9



Comments
Well done mate
This is really great! I faced some issues with this version while installing vsp app Well done research on the bugs in latest ios version.
Really it is very helpful for
Really it is very helpful for me. Thanks a ton and sharing. Research credits by your post.
Following Java Forum
Being a software programmer, I have to be an active member of java forum, as it helps seeking tips and suggestions from experts.
Add new comment