BMW Core Web Portal & ConnectedDrive - Exploitation of Car Configurations
BMW Core Web Portal & ConnectedDrive vulnerable
Today we will talk about two vulnerabilities that was discovered by Vulnerability Laboratory core team member "Benjamin Kunz Mejri", the vulnerabilities which are not patched yet! There are two main bugs both related to the BMW online service and web app for ConnectedDrive .
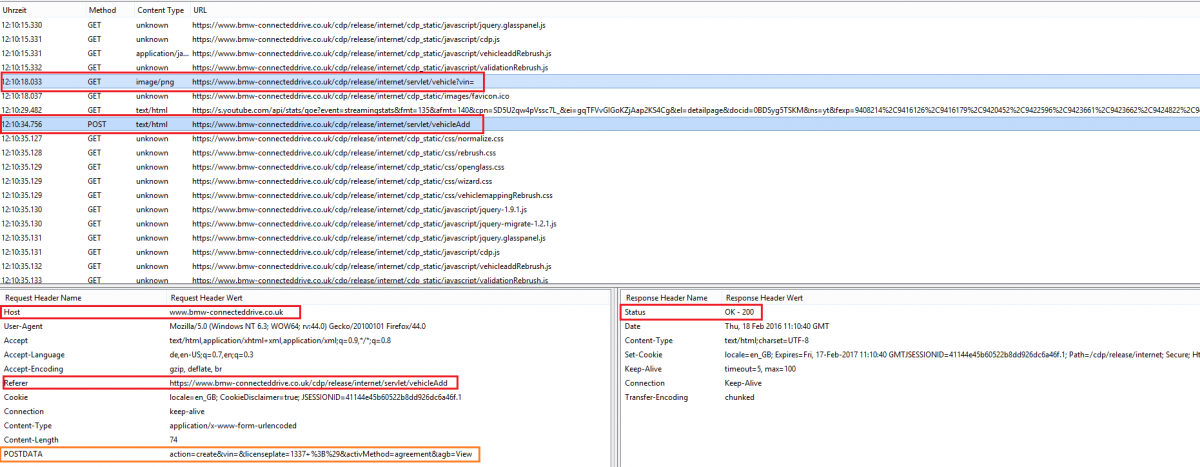
The first vulnerability found in the BMW ConnectedDrive web-application. The vulnerability allows remote attackers to manipulate specific configured parameters to compromise the affected web-application service. A vehicle identification number,commonly abbreviated to VIN, or chassis number, is a unique code including a serial number, used by the automotive industry to identify individual motor vehicles, towed vehicles, motorcycles, scooters and mopeds as defined in ISO 3833.
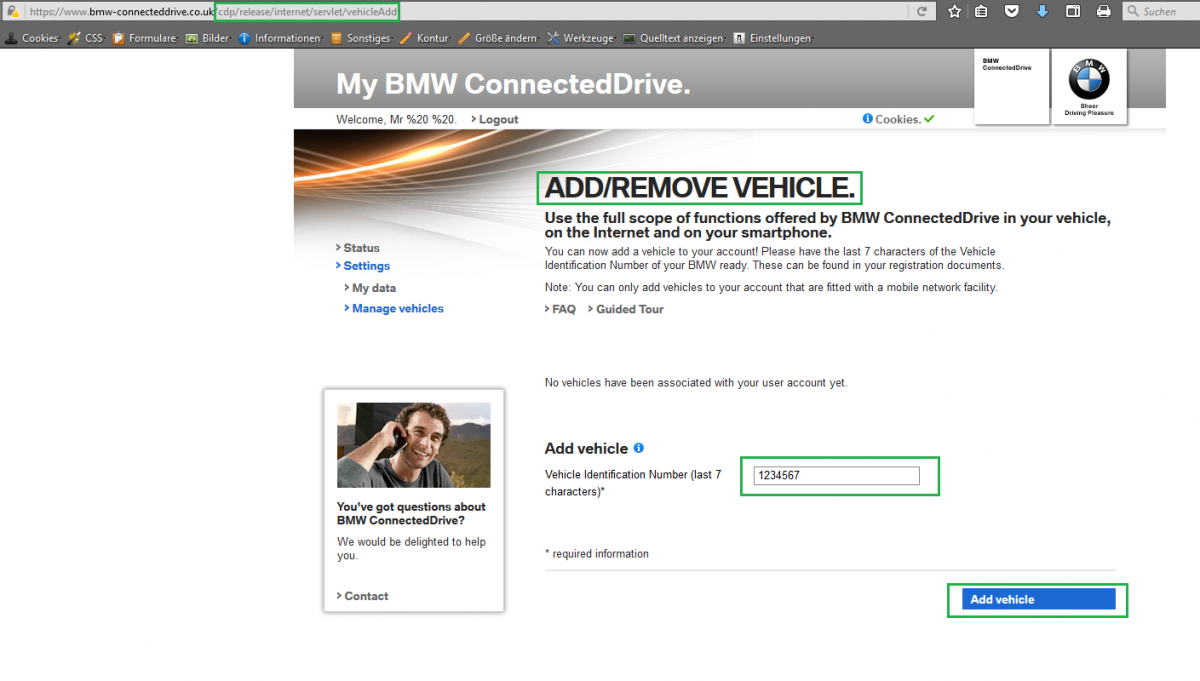
The vulnerability is located in the session management of the VIN adding procedure. Remote attackers are able to bypass the secure validation approval of the VIN when processing to create it. Remote attackers are able to change with a live session tamper the action information to create or update. Thus allows an attacker to bypass the invalid VIN exception to add a new configuration finally. Thus interaction results in the takeover of other vehicle identification numbers to view or manipulate the configuration. The session validation flaw can be exploited with a low-privilege user account, leading to manipulation of VIN numbers and configuration settings such as compromising registered and valid VIN numbers through the ConnectedDrive portal. The settings available through the ConnectedDrive portal include the ability to lock/unlock the vehicle, manage song playlists, access email accounts, manage routes, get real-time traffic information, and so on.
After the successful exploitation to integrate the vin in the portal the attacker can login with the connectedrive ios application. The attacker includes the illegal vin to his account via portal and can access the configuration via mobile application or portal. Thus way an attacker is able to unauthorized access the info-tainment-system of bmw cars to interact without hardware manipulation or cable access.
Affected Module(s)
VIN - Konfiguration to Add/remove Vehicle
Proof of Concept
Manual steps to reproduce the vulnerability ...
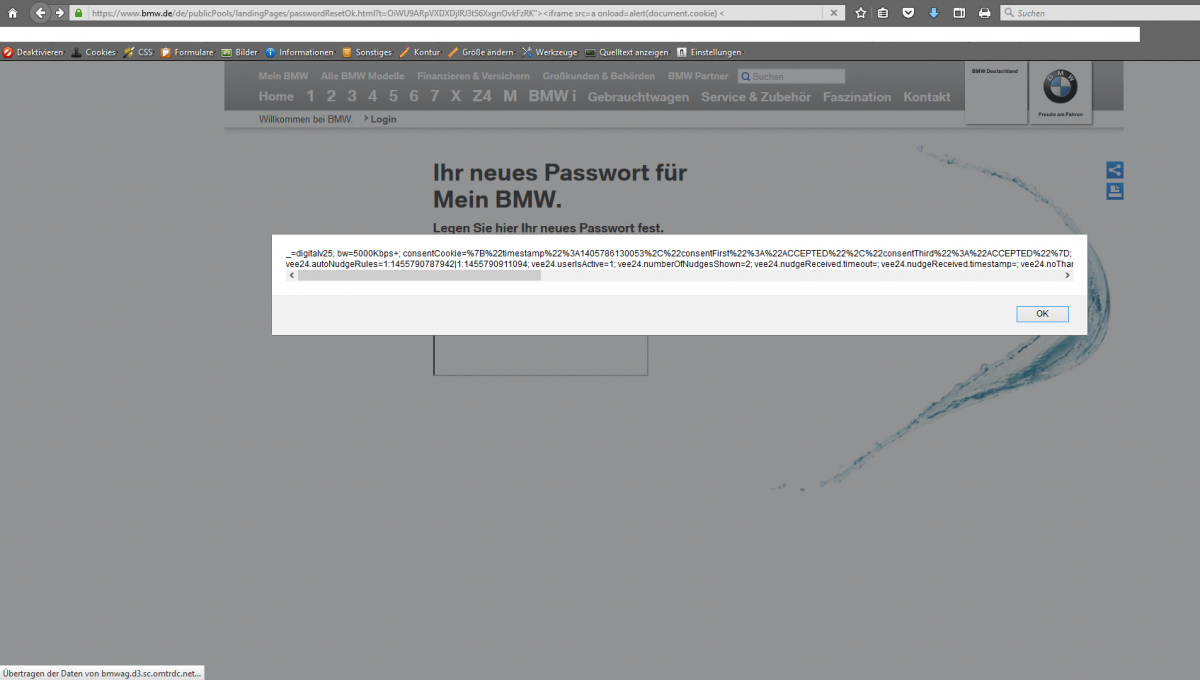
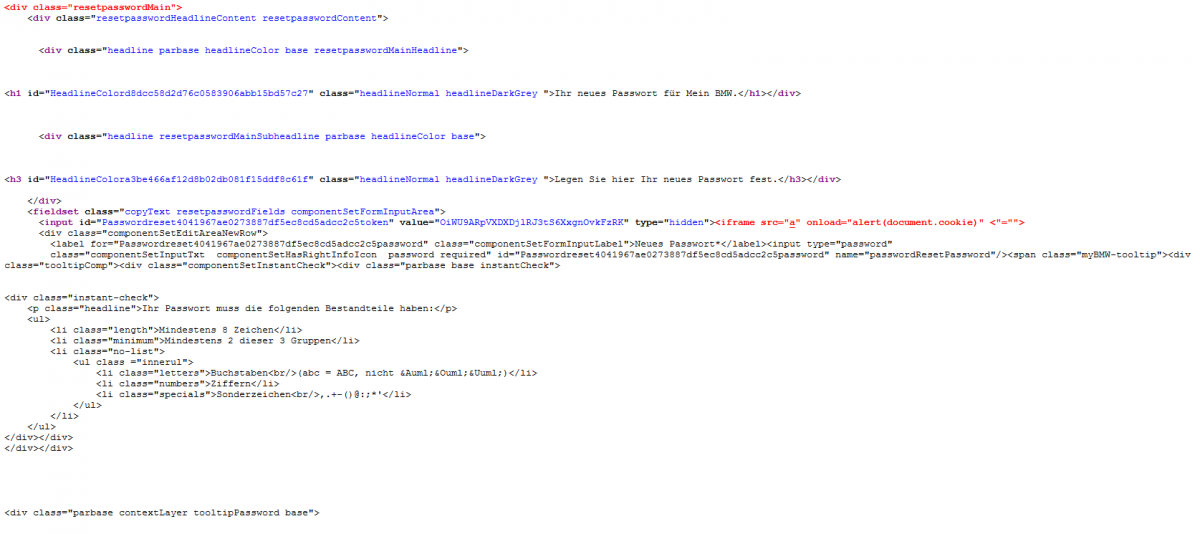
The second vulnerability is a cross-site scripting vulnerability the researchers discovered client-side on the BMW web domain in the password reset token system. The researchers call the problem a "classic" cross-site scripting vulnerability, as the security flaw does not need privileged user accounts to be exploited; instead, "low user interaction" is needed through only a payload injection into the vulnerable module.[ ./de/publicPools/landingPages/ ]
The vulnerability is located in the `t` value (token) of the `passwordResetOk.html` web-application file. Remote attackers are able to inject own client-side script codes to the `passwordResetOk.html` file. the request method to inject is GET and the vulnerability is located on the client-side of the affected bmw web-service. The attacker injects the payload after the secure token to execute the context in the passwordResetOk.html file.



Comments
Ali
hello I realy like this post thank you very much for sharing us.Ali
I love BMW car, but my mom
I love BMW car, but my mom gives me another car as gift. I like that as well. but thanks remind me BMWs configurations and features.
BMW is one of the most iconic
BMW is one of the most iconic cars in the world.
Add new comment