Microsoft Online Service Bug Bounty Program Live - Startup 23. September!
During the last year we was waiting for the new public release that was silent announced by microsoft officials in the tech center. In several mails and conversations they announced silently between the lines that there will be a bug bounty program for online services in the future.
Microsoft published the new conditions, scope and rules of the program that starts today (23. September). An anonymous microsoft official notified the vulnerability laboratory in the morning as one of the first community to announce the exclusive new program to the publicly.
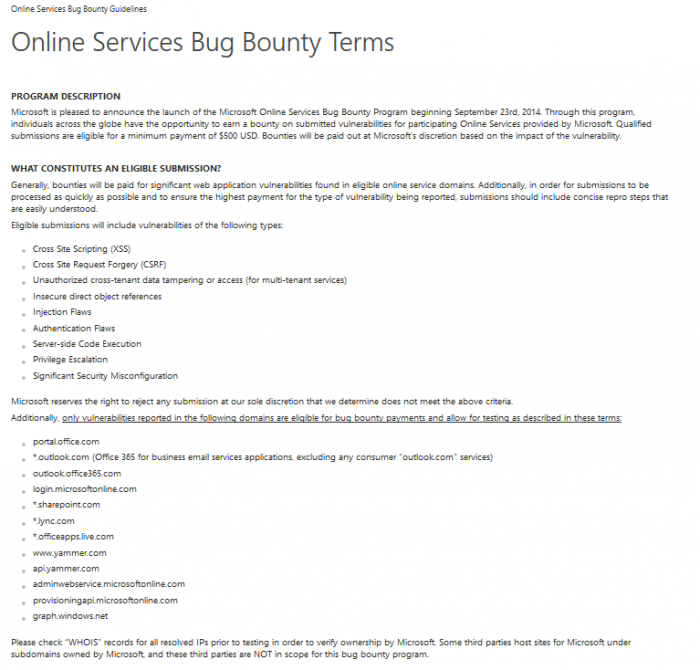
The program scope allows to submit vulnerabilities in the following online service applications and software
- portal.office.com
- *.outlook.com (Office 365 for business email services applications, excluding any consumer “outlook.com” services)
- outlook.office365.com
- login.microsoftonline.com
- *.sharepoint.com
- *.lync.com
- *.officeapps.live.com
- www.yammer.com
- api.yammer.com
- adminwebservice.microsoftonline.com
- provisioningapi.microsoftonline.com
- graph.windows.net
Eligible submissions will include vulnerabilities of the following types:
- Cross Site Scripting (XSS)
- Cross Site Request Forgery (CSRF)
- Unauthorized cross-tenant data tampering or access (for multi-tenant services)
- Insecure direct object references
- Injection Flaws
- Authentication Flaws
- Server-side Code Execution
- Privilege Escalation
- Significant Security Misconfiguration
The following are examples of vulnerabilities that will not earn a bounty reward:
- Missing HTTP Security Headers (such as X-FRAME-OPTIONS) or cookie security flags (such as “httponly”)
- Server-side information disclosure such as IPs, server names and most stack traces
- Bugs in the web application that only affect unsupported browsers and plugins
- Bugs used to enumerate or confirm the existence of users or tenants
- Bugs requiring unlikely user actions
- URL Redirects (unless combined with another flaw to produce a more severe vulnerability)
- Vulnerabilities in platform technologies that are not unique to the online services in question (Apache or IIS vulnerabilities, for example.)
- ”Cross Site Scripting” bugs in SharePoint that require “Designer” or higher privileges in the target’s tenant.
- Low impact CSRF bugs (such as logoff)
- Denial of Service issues
- Cookie replay vulnerabilities
Researchers that participate in the program get a minimum reward of about 500$. Critical issues will result in high reward payments that will be set by the jury team itself. We say thanks to the microsoft bug bounty program team and support to announce the new program with one of the first articles.
Last week microsoft corporation destroyed the own security team (trustworthy computing) and it looks like they balanced the buffer with an expansion through the new public bug bounty programs for the online services.
Note: 2012/2013 Ateeq ur Rehman Khan, Ibrahim Mosaad El Sayed and Benjamin Mejro reported around 20 vulnerabilities in sharepoint, office 365 services, yammer (api) and microsoftonline. As result of the successful tests the yammer, office and other apps has been included for web service pentests to the public.
Reference(s): Online Services Bug Bounty Terms



Comments
"really it.
http://google.com
Add new comment