Citrix Gateway & Cloud MFA - Insufficient Session Validation Vulnerability
Citrix Gateway & Cloud MFA - Insufficient Session Validation Vulnerability
The vulnerability lab research team was able to discover a simple but effective insufficient session validation vulnerability that can be exploited to bypass the mfa login authentication process on Citrix ADC/NetScaler v13.0 & v13.1, Citrix Gateway/NetScaler Gateway v13.0 & v13.1 and the Citrix Cloud Services Website. The security vulnerability allows remote attackers to bypass the mfa function by hijacking the session data of an active user (non expired session) to followup with further compromising attacks.
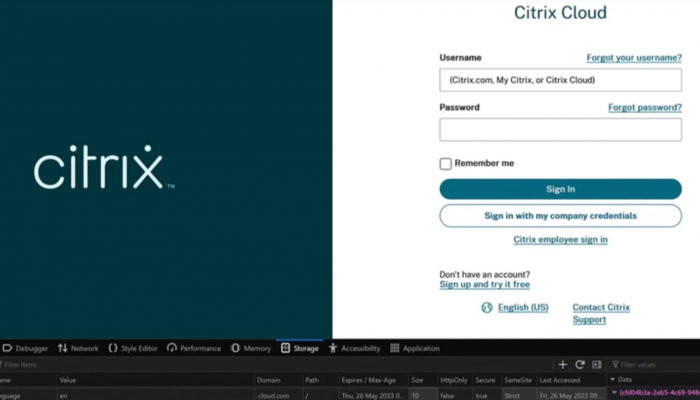
The insufficient session validation vulnerability is located in the Citrix Gateway login without web-application firewall (waf) and the Citrix Gateway login with web-application firewall (waf). Attackers can access the applications behind the Citrix Gateway without authentication after compromising a client by extract of a specific generated access cookie. In the onprem version of Citrix ADC and Citrix Gateway it is only required to hijack the NSC_AAAC cookie for unauthorized access through the Citrix Gateway. To gain access to a AAA protected webservices it is required to hijack the NSC_TMAS cookie.
The security issue is not only exploitable in the onprem version of Citrix ADC and Citrix Gateway, but as well in the Citrix Cloud Services Website. For Citrix Cloud Services Website its required to hijack as well the regionSessionId, customer and sessionId to exploit the vulnerability. Any kind of authentication (Single and Multifactor) does not prevent the exploitation of this vulnerability.
Citrix does recomment that customers should use the web-application firewall to protect the session data but finally the protection mechanism does not secure against thus type of insufficient session validation attacks.
Successful exploitation of the vulnerability leads to session hijacking, unauthorized access to applications content and compromise of the accessable infrastructure behind, through the Citrix Gateway and AAA.
Vulnerable Function(s):
[+] NSC_AAAC (Cookie)
[+] NSC_TMAS (Cookie)
Affected Module(s):
[+] Citrix Gateway
[+] AAA
The insufficent session validation web vulnerability can be exploited by remote attackers without user interaction with remote device access (exp. client compromise) or cookie hijacking. For security demonstration or to reproduce the web vulnerability follow the provided information and steps below to continue.
For example there is a simple way on how to exploit the issue manually ...
1. Open the url for the Citrix Gateway
2. Open the browser internal web developer tools
3. Login to the Citrix Gateway and enter the login data
4. Successful login and it can be observed that an additional cookie is written (NSC_AAAC)
5. On a second unknown test computer system the citrix gateway is opened (browser)
6. Open the browser internal web developer tools
7. Creation of a new cookie for the page with the name, value and path of the cookie of the other session
8. Reload of the login page or login to the login screen with random values (Input of content is important to use the logon)
9. Successful login by the second device and take over the active non expired session
10. Successful reproduce of the vulnerability!
To reproduce the same issue on the Citrix Cloud Services Website you have to add 3 cookies:
- sessionId
- regionSessionId
- customer
Security Video: (Cloud)
https://www.youtube.com/watch?v=vObgOpGpCSM
Security Video: (OnPrem)
https://www.youtube.com/watch?v=RFjRgiW2OWE
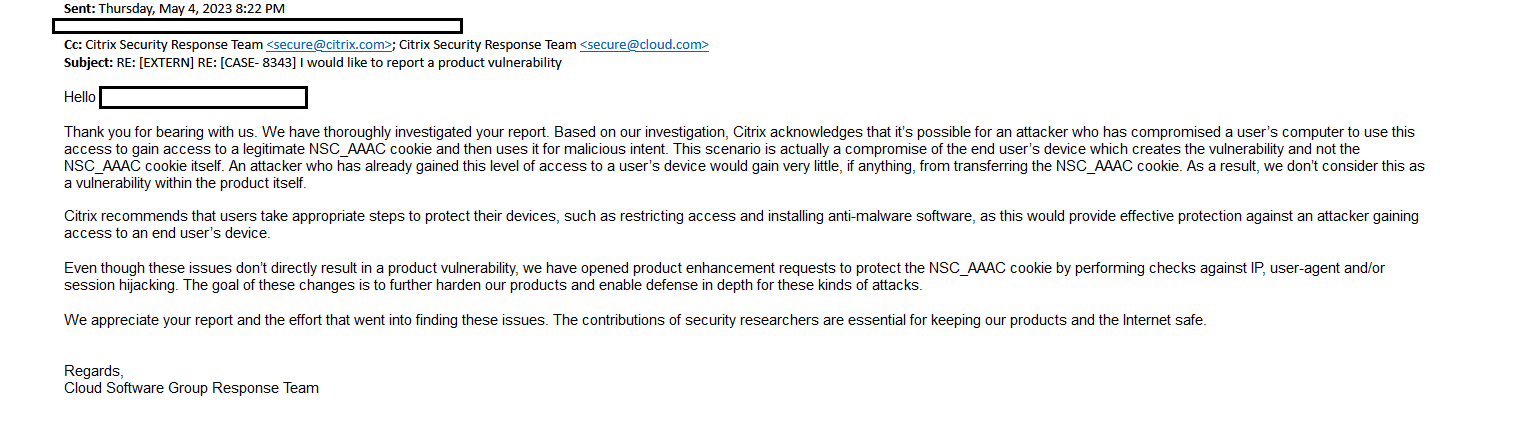
The vulnerability in the authentication has been reported by vulnerability researcher of the vulnerability lab teams several times since end of april to the Citrix security program. The content was checked beforehand and the vulnerability was marked as valid. However, the service provider cognitive did not manage to accept it as avulnerabilty. The last response was the following:
"Thank you for bearing with us. We have thoroughly investigated your report. Based on our investigation, Citrix acknowledges that it’s possible for an attacker who has compromised a user’s computer to use this access to gain access to a legitimate NSC_AAAC cookie and then uses it for malicious intent. This scenario is actually a compromise of the end user’s device which creates the vulnerability and not the NSC_AAAC cookie itself. An attacker who has already gained this level of access to a user’s device would gain very little, if anything, from transferring the NSC_AAAC cookie. As a result, we don’t consider this as a vulnerability within the product itself. Citrix recommends that users take appropriate steps to protect their devices, such as restricting access and installing anti-malware software, as this would provide effective protection against an attacker gaining access to an end user’s device. Even though these issues don’t directly result in a product vulnerability, we have opened product enhancement requests to protect the NSC_AAAC cookie by performing checks against IP, user-agent and/or session hijacking. The goal of these changes is to further harden our products and enable defense in depth for these kinds of attacks."
At this point we would like to thank citrix for the answer and the vulnerability still remains exploitable.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2324



Comments
citrix mfa failed by design
using your bug in connection
Add new comment