Advanced Persistent Threat Golden_hands - Digital Bank Robbery of the Year 2020

The Digital Bank Robbery of the Year 2020 - APT "Golden_hands" (Government Emergency Aid)
In last 4-5 weeks our company Evolution Security GmbH and all around us were affected by the economy crisis that came cold from the back. This is a story about advanced persistent threats in Germany and the European Union during the crisis affecting the finance system and economy sector.
All began about in January when we still planned with different other security companies and institutions to start an awareness program cause we have noticed the upcoming wave of phishing, hacker attacks and malware. Shortly after we all took together several resources and build up a refreshing list of phishing / fraud and malware domains.
25.03.2020, the current Minister of Finance Olaf Scholz and the Chancellor ordered special aid for companies to save the economy. Thus, several billion euros in rescue money were made available for small and medium-sized companies. In a further step, banks have been urged to make transfer processes quick and uncomplicated in order to speed up any payments to citizens.
As we are confronted with different issues in the crisis team, we are very attentive to emerging problems in all different sectors. In a meeting with friends we decided to take up the trail at a certain point.
Two days before the first aid money was to be distributed in North Rhine Westphalia (NRW - Federal State) in Germany and the developers of the state commissioned agencies programmed the web applications, we became aware of an inquiry in several deep web forums in distant countries.
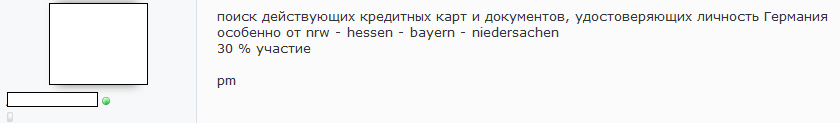
1) 20.03.2020
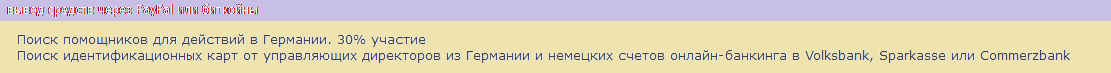
2) 22.03.2020
3) 27.03.2020
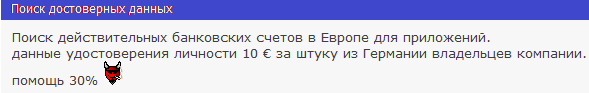
In the picture a request was made in Russian, asking specifically for credit card data (online banking access) and identity cards. Behind the message, they were then specifically formulated from which federal states these would be of advantage and a 30% participation for supporters. The writer of the news called himself "Golden_hands" and comes from a well-known Russian Blackhat group.
In the forum there were clear requests and a reference to private communication via the Tor network. In parallel, the same message appeared in slightly modified form in various private forums. The content of the message was worded a bit better each time. Another Turkish group with German roots, which otherwise specializes in grandchild tricks and financial fraud and has been surrounded by investigating authorities in the Middle East for a long time, also jumped on the bandwagon via European deep web forums.
Since we knew that everyone is currently in a state and economic crisis, we suspected a major action here. In the forums mentioned above, it is unfortunately the case that there are only a few inquiries of this kind from already very well-known accounts, which sell ID cards and online banking access rather than buying together.
Since we do not do business with criminals and a major operation was suspected here, we agreed in the team that a monitoring system for the regional council pages would be set up. With this, we wanted to wait for the exact moment when the first application forms and web applications were made available on the online services of the federal states. At the same time we reported our findings under an anonymous account and the investigating authorities in Hesse, North Rhine Westphalia, Bavaria & Lower Saxony.
In a preliminary meeting we discussed possible risks in the introduction of these application applications. There are over 1 million applications. The Federal Government promises immediate aid, but without prevention campaigns and without further security measures in the financial mechanism. In the crisis and will lead to more problems (financial fraud) in our economic system.
When the first forms and applications were online, we went to check in directly with legal variables for a friendly company in distress early in the morning and observed the entire process in detail. In the non-uniform applications, which were mostly entered on the pages of the regional council, a ready-made form was displayed. This was filled out by click and choice and the data was simply added later. Afterwards one got an identification and an access code.
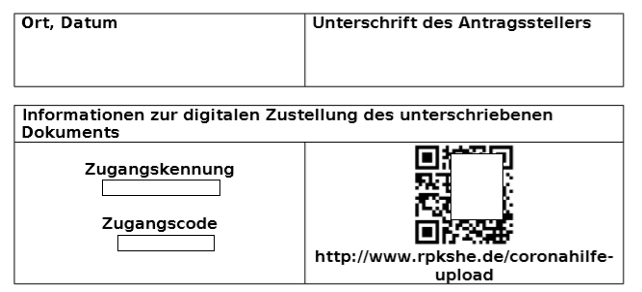
As you can quickly find out, the identifier is continuous per entry, so an identifier is no longer a secret. Then for each identifier a bad password is generated with a known algorithm under 8 characters with simple number sequences and small letter sequence outside any regular standard. A short test with a password file based on the strings has resulted in successful overcoming of the strings in 1 hour. In the end, this means that we can determine our own accesses in a very short time.
[+] bad password
[+] known identifiers (continuous)
[+] no bruteforce / IP blocking
[+] no security header
[+] meta-data in requests
Now we found out that the application uses crack-able passwords, the identifier is known because it is generated bound to the session, no brute-force protection mechanism and no security header checks are made in the upload.
But here we were far from being at the end of the road, of course we still had to check how the applications in the system are verified by the clerks as real applications. We looked at the processes of different applications that were submitted on the first day. After a consultation on the processes, the first ones got money transferred to their bank accounts without a call or another signature with verification.
This without identity verification or other further measures. When we realized this, it was obvious that this would be a scenario for fraudsters all over the world to get their hands on governments emergency aid measures. So we created a simple map that briefly illustrates the process of the fraud chain from the fraud scam mentioned above.
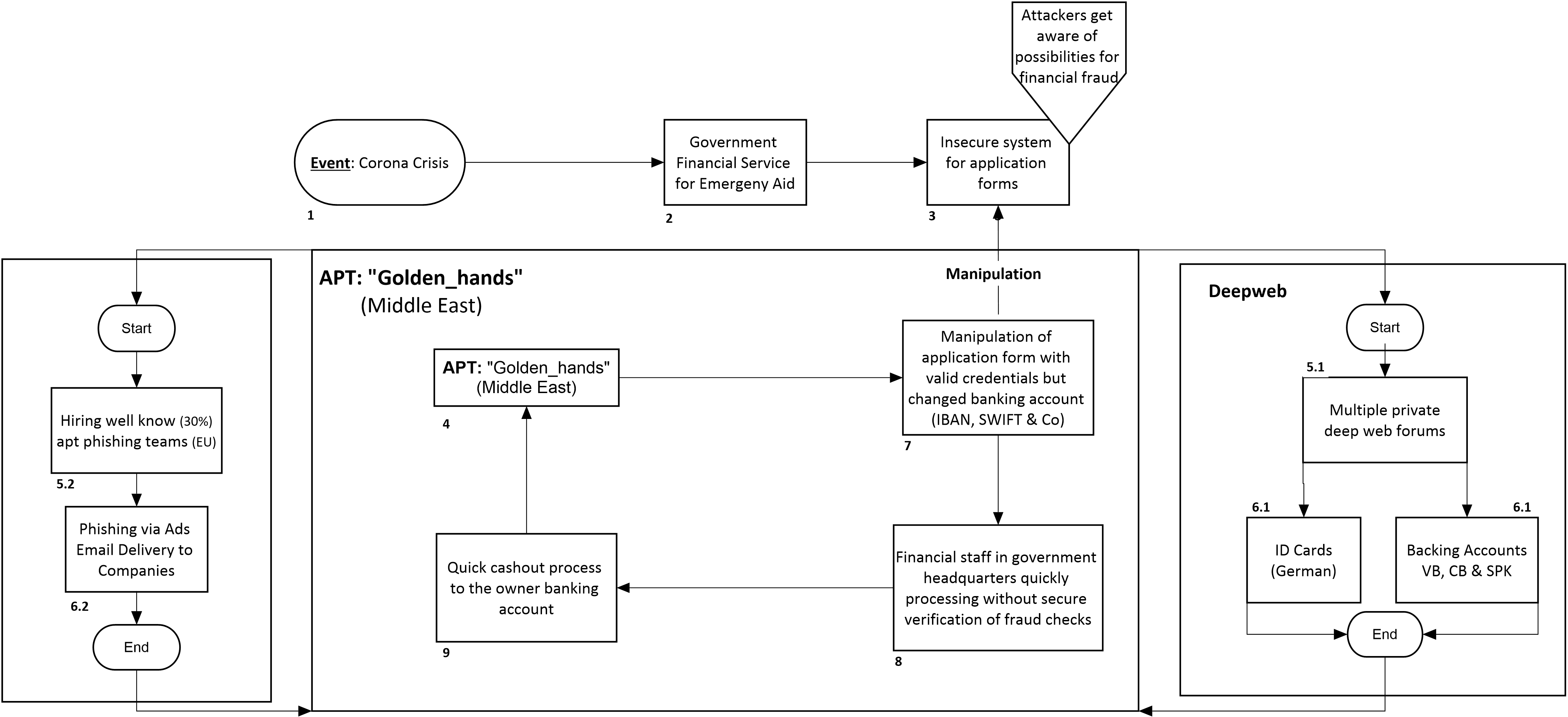
We then distinguished between two different scenarios.
1. It is directly tried with already existing data from Leaks (Deep-Web) which were bought e.g. the emergency aid application to places. Only the account number is adjusted, because the name of the account holder is not checked directly in the new banking system without anomalies. This has something to do with the new standards for transfers at e.g. the Sparkasse / Volksbank. For example, the name may be entered incorrectly in a transfer, but the transfer still arrives at the correct account, because only the IBAN is included in the first check.
2. Individual personal data is accessed via phishing sites with an additional campaign. Afterwards, the collected data is used directly to submit an application, where again only the bank account data is manipulated. The second way is just a simple way to further increase the hit rate. In some cases Google Ads were used, but also directly distributed via emails with phishing sites. The final way after receiving the data, however, is to use the aforementioned modus operandi via the offender groups around Golden_hands.
This was followed by further reports (1/2/3) to investigative journalists from TV and the news, as well as additional reports from individual investigative authorities. Of course, they immediately picked up the scent and informed everyone about the ministry. Shortly afterwards it was all over the press and the first fraudulent applications in the system were identified. At the end the investigateive journalist only got the german phishing gang that was getting 30% for the service.
Unfortunately, we were already a little late because communication in the crisis to individual instances was too slow and the first criminals with already made applications received individual payments.
At that time, in some federal states, individual payments of up to 3-4 billion euros were transferred without verification. About 10 days later, the same blackhat contacted us and confirmed that his scam worked perfectly. He would have cashed out well without doing much.
We currently assume that about 40% of your data has been lost to the criminals via phishing sites and about 60% has been made directly by already existing extensive data records.
After it became known that there are fraudulent applications and the first reports were made, the emergency relief measures were stopped. Since the same thing was done by the criminals in parallel in all federal states, all systems had to be informed and at the same time slowed down before a huge financial and economic damage could occur.
The Blackhats of Golden_hand have hit hard. How high the exact damage really is can only be determined after the crisis by investigations of the banks and the police. It is so expected that there will be imitators all over the world who try to get immediate help during the crisis. They will not only choose the first way (phishing / emails and identity theft), but also attack the vulnerable web applications so that application data can be accessed immediately.
In order that others can also benefit of this lesson in Germany, we have briefly reviewed the events surrounding the attacks here. It is clear that there will always be people who carry out phishing attacks, but it does not have to be made so easy for the fraudsters that they only submit blank applications which are immediately transferred without verification by the individual federal states.
1. Event: Corona Crisis
21. January: first situation report 1 from the WHO with content
On 31 December 2019, the WHO China Country Office was informed of cases of pneumonia unknown etiology (unknown cause) detected in Wuhan City, Hubei Province of China. From 31 December 2019 through 3 January 2020, a total of 44 case-patients with pneumonia of unknown etiology were reported to WHO by the national authorities in China. During this reported period, the causal agent was not identified
URL: https://www.who.int/emergencies/diseases/novel-coronavirus-2019/situatio...
Chinese authorities closed the Wuhan market on January 1.
On 13 January 2020, the first laboratory-confirmed infection with SARS-CoV-2 was reported from Thailand - and thus outside the People's Republic of China. On 23 January 2020 the first case of infection outside Asia was reported in the United States of America. URL: https://de.wikipedia.org/wiki/COVID-19-Pandemie
On 11 February 2020, the WHO announced "COVID-19" as the name for this new disease (https://www.who.int/emergencies/diseases/novel-coronavirus-2019/technica...(covid-2019)-and-the-virus-that-causes-it)
Supplement to the national pandemic plan 4.3 of the RKI: https://www.rki.de/DE/Content/InfAZ/N/Neuartiges_Coronavirus/Ergaenzung_...
COVID-19 was declared a pandemic by the WHO on 11.03.2020.
On 16 March 2020, the Federal Government and the heads of government of the federal states decided on the shutdown https://www.bundesregierung.de/breg-de/aktuelles/vereinbarung-zwischen-d...
2. Goverment Service for Emergeny aid
In the middle of March, all the authorities provide entrepreneurs with new prospects for emergency aid during the Corona crises months. Negotiations were held and the following concepts for the individual emergency aid measures were adopted.
Federal state: Hesse
On 30.03.2020, the state of Hesse made the web application available online from the respective service providers via the Ministry of Economics. There, the applications for emergency aid could be sent directly to the Ministry.
Total emergency aid:
up to 10.000 Euro for solo self-employed and companies with up to 5 employees
up to 20.000 Euro for companies with up to 10 employees
up to 30.000 Euro for companies with up to 50 employees
URL: https://rp-kassel.hessen.de/corona-soforthilfe
Federal state: North Rhine Westphalia
On 27.03.2020, the Federal State of NRW made the various web applications available online from the respective service providers via the Ministry of Economic Affairs. There, the applications for emergency aid could be sent directly to the Ministry.
Total emergency aid:
9,000 euros for 3 months for eligible applicants with up to 5 employees
15,000 euros for 3 months for eligible applicants with up to 10 employees
30,000 euros for 3 months for eligible applicants with up to 50 employees
URL: https://www.land.nrw/coron
Federal state: Bavaria
On 28.03.2020, the state of Bavaria made the various web applications available online from the respective service providers via the Ministry of Economic Affairs. There, the applications for emergency aid could be sent directly to the Ministry.
Total emergency aid:
up to 10 employees 7,500 euros,
up to 50 employees 15.000 Euro
up to 250 employees 30,000 euros
URL: https://www.stmwi.bayern.de/soforthilfe-corona/
Federal state: Lower Saxony
On 30.03.2020, the federal state of Lower Saxony made the various web applications available online from the respective service providers via the Ministry of Economics. There, the applications for emergency aid could be sent directly to the Ministry.
Total emergency aid:
3.000 Euro (up to 5 employees)
5.000 Euro (up to 10 employees)
10.000 Euro (up to 30 employees)
20,000 Euro (up to 49 employees)
URL: https://www.mw.niedersachsen.de/startseite/aktuelles/informationen-zu-de...
3. Insecure system for application forms
Due to the exceptional situation during the emerging crisis, individual different web applications were created for each federal state in a fast-track procedure with service providers of the Federal Ministry. An upload form application was connected to a login form which makes individual identifiers with links available to applicants. The following deficits became apparent ...
1. No valid used security header in web applications
2. Missing SPF Records
3. No protection against automated login attempts (Bruteforce)
4. No safety test or quality control
5. Fast application procedure with separate acceleration by processors
6. Weak passwords (Dictionary Attacks: self-experiment 25 minutes)
7. Weak active cipher suites
8. Meta data in query forms (known / unknown)
9. Generally unsafe application procedure
4. Advanced Persistent Threat: "Golden_hands" (Middle East)
Through incoming sensor technology we were informed about a specific request on 22.03.2020, 26.03.2020 & 28.03.2020. In several well-known but private forums in the Middle East a request for identity card information and online banking accounts of companies was made. At the same time, offers for a 30% participation for the active retrieval of company data were offered. This happened immediately before the emergency application forms were made available after the individual states had announced this. Thus, the attackers were well prepared for the launch of the web applications on the Ministry of Economics pages.
Process: Deepweb
5.1 Multiple private deep forums
22.03.2020, 26.03.2020 & 28.03.2020 Request for bank account data and identity card information from self-employed persons or companies
6.1 ID Cards (Are required to enter real personal information)
Banking Accounts (Are required to be different in the same banking system before cashout)
Process: Web
5.2 Hiring well know (30%), apt phishing teams (EU)
Since the spectrum of the attack was too small for the attacker, he offered others a 30% stake, which decreased to 20% around April 03.04.2020.
6.2 Phishing via Ads Email Devlivery to Companies
The attackers, who supported the attack for 30% participation, used their own phishing sites, which were then distributed by email or via Google Ads and other digital advertising media (banners/links) to entrepreneurs who are really affected by the Corona crisis.
7. Manipulation of application form with valid credentials but changed banking account (IBAN, SWIFT...)
After all data for an attack had been collected at "Golden_hands", the requests were transmitted in the system. Only the relevant account information and e-mails were changed and the application was entered into the system with valid data.
8. Financial staff in gov headquarters quickly processing without secure verification of fraud checks
Due to the accelerated procedure and the overcrowded application offices in the Ministry of Economy, applications were submitted without excessive examination. Neither the bank information nor the company information was subjected to an identity check. After the criminal attackers with their legal companies from NRW and Bavaria had submitted the applications themselves and everything worked, they began to place individual applications in the system with a time delay.
9. Quick cashout process to the owner banking account
After a few days, the first criminals had their sums credited to the bank accounts of Sparkasse and Volksbank as well as Commerzbank. Most of the time the sum of the fraudulent applications were for the small entrepreneurs of 5-10 employees (10.000€).
10. Quick cashout process to the owner banking account
We made anonymous contact with the criminal by getting into conversation via a Jabber Messenger . Shortly after we had established some trust, we planted compromised records on him. Why? So that when these records are entered into the system, even the most blind officer in the Ministry of Commerce will know what happened. This happened about 4 days after we handed over the first 3 records. Because the perpetrator had no possibility to check the record in the system, he made a double entry which resulted in the shutdown of the whole service in NRW.
What should we learn from this situation?
1. Never state disbursements without detailed examination mechanisms
2. Preventive preparation for emerging crises for companies
3. Unified and secure provision of web applications and forms (Federal Government)
4. IBAN check in the banking system for double IBAN when booking applications for federal states
Why are we writing this article here?
So that others can benefit from the experience in and from our country to prevent possible attacks on international public financial systems. In many countries, emergency aid has neither been adopted nor have individual processes to ensure its continuation begun. Therefore, there is an increased risk that the attackers, who are well connected internationally, will also attack other financial systems of our international economy during the corona crisis.
There is a very high probability that once the attack pattern has been identified, there is the possibility for attackers to use evasive functions to continue impersonating third parties such as tax advisors or notaries. It is very likely that these functional possibilities will also be abused by the attackers in the near future.
It is important for us to point out our own mistakes and learn from them. It is just as important to let others benefit from the situation by protecting your own country from this kind of attack. Vigilance and insisting on values even in a crisis is the first thing we have to learn in order not to reward the wrong ones in the end. In parallel, each country or district should not forget that there were definitely massive phishing waves, excessive scams or new and old adapted social engineering and malware attacks.
Fraud Correlation & the Finance Industry Mistakes
While the criminals were planning their big coup, all were just out of service and flooded with current requests. suspicious payments were no longer reliably reported due to remote workstations and fallback systems. Of course, the criminals, who are highly networked in the payment industry, knew this too. As soon as a gap opens up, these criminals try to exploit it. Before you realise at home what has actually happened, a million euros in damages arrive. Companies or organisations in need of help can no longer use this money and fall through the raster in the corona crisis. Normally we pay the industry to ensure that these fraud problems are detected at a high level and at an early stage. In this case, unfortunately, in the first moment of shock, everyone in the system itself was next. If everyone thinks only of themselves and throws all security aspects and moral ethics overboard, the costs will end up being paid by citizens like YOU and me, who already have nothing anyway. In the time others was in shock, we saw the threat upcoming and reacted to make them visible in the system of emergency aid applications.
This also affects other payment industry parts in the moment they do remove limits or allow like german banks during the crisis a payment of 50€ without pin verification. All thus will come soon back to us because there is a simple reason this mechanisms are established to secure all our finances. The insurances also do not pay for damages caused by negligence.
After all different investigative corners and endings were trying to break down the background of the attacks, everyone followed the wrong trail that led to the phishers involved for 30%, but never beyond.
Note: During and after our publication a lot of updates has been established and several mechanisms are securely implemented today. For sure the time was not enough to process such typ of application but this is emergency management at all.
We also send some sunny greetings to the deepweb gang of phishers and Golden_hands that we pwnd up during there big coup. Also big greets to the bka that as to late and received help of some anonymous fr13nd5. Sorry for crashing the process but since you all got aware of it, the moment to react is passed.



Comments
vraiment bon l'article
Tú eres el jefe y él es un
Sometimes I just can't handle
to me you are just the boss
ndr & frontal
хороший улов, но позор
Le tue caramelle stanno
uhhh, der Artikel ist echt
big ?
we dont understand you way of
we dont understand your way of thinking but enjoy to read as well further posts on our magazine. balance is everything :*
Add new comment