Microsoft Windows 2012 R2 (x64) - (MMC) Local DoS Vulnerability
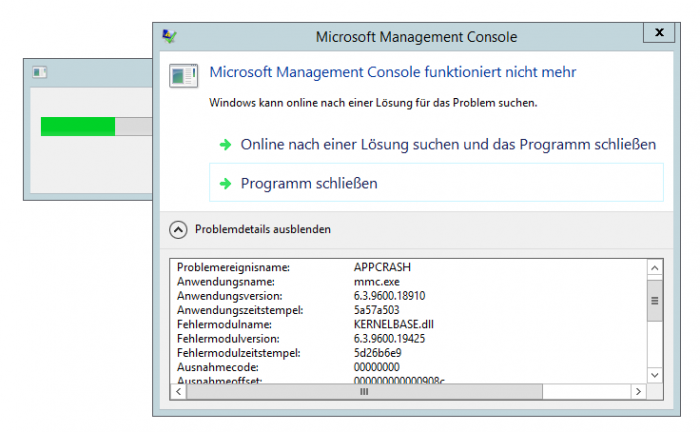
Pointer Issue crashs local mmc.exe process on Microsoft Windows 2012 R2 x64
Due to a test in a staging-system that was fresh setup with a windows 2012 r2 release the researcher of the vulnerability lab identified a serious local denial of service vulnerability affecting different other microsoft processes or security mechanisms.
The windows 2012 r2 has a basic firewall were it is possible to setup specific rule set. Defining a block policy for ips (above 200) can result in a corruption of the windows mmc.exe (Microsoft Management Console). The result is that the actual snapshot of the session corrupts due to the error with a corruption, which results in a simple but stable application crash. The issue occurs in the kernelbase dynamic link library because of the counted ip items in the list that returns with a null pointer.
The problemtic comes up through the Incoming rules - New Rule (Add) function. The issue can be exploited by local low privileged system user accounts without user interaction. The issue only affects only the x64 architecture operating systems with windows 2012 r2. Local attackers are able to crash the mmc.exe which results in several local misfunctioning security measures. Triggering the issue results two times in an application hang and in the third attempt in a final uncaught exception that crashs the full process. Due to the crash the windows firewall popup with the advanced security settings to protect but clicking ok still corrupts the process, then to recover the snapshot.
Error Event Logs
AppHang_mmc.exe_6c7d7829f119e25deeb0542e2dd2875f4f4dfb9_bc31d4b6_02344e1d
AppHang_mmc.exe_6c7d7829f119e25deeb0542e2dd2875f4f4dfb9_bc31d4b6_1aa23175
... at least followed by the final ending appcrash that smashs down the mmc.exe
AppCrash_mmc.exe_e5d766ef5828c8e313b57ac65bf2e70a6d6688a_00000000_029dd268
After some short time of research around the crash and serval reproduces in different fresh images we uncovered manual steps to reproduce the unexpected behavior
Manual steps to reproduce the local issue ...
1. Open the local firewall
2. Setup a new rule
3. Setup to deny all
4. Include some ips above the mentioned limit (200)
5. Save and reply internal by creating afterward a local snapshot (automated)
6. An apphangs occurs 2 times to the process and finally on third time crashs with uncaught null pointer exception
Note: At that point several messages in windows popup to recover the snapshot which results in another error
7. Press ok and the mmc.exe process crashs permanently
8. Successful reproduce of the local vulnerability!
--- Application Error Logs ---
EventType=AppHangTransient
EventTime=132277138943110905
ReportType=3
Consent=1
ReportIdentifier=a43305c3-5d4e-11ea-813c-0025904667c6
IntegratorReportIdentifier=a43305c4-5d4e-11ea-813c-0025904667c6
NsAppName=mmc.exe
Response.type=4
Sig[0].Name=Problemsignatur 01
Sig[0].Value=mmc.exe
Sig[1].Name=Problemsignatur 02
Sig[1].Value=6.3.9600.18910
Sig[2].Name=Problemsignatur 03
Sig[2].Value=5a57a503
Sig[3].Name=Problemsignatur 04
Sig[3].Value=unknown
Sig[4].Name=Problemsignatur 05
Sig[4].Value=unknown
Sig[5].Name=Problemsignatur 06
Sig[5].Value=unknown
Sig[6].Name=Problemsignatur 07
Sig[6].Value=unknown
DynamicSig[1].Name=Betriebsystemversion
DynamicSig[1].Value=6.3.9600.2.0.0.272.7
DynamicSig[2].Name=Gebietsschema-ID
DynamicSig[2].Value=1031
DynamicSig[22].Name=Zusätzliche Absturzsignatur 1
DynamicSig[22].Value=a170a78f269a790e02a336f2ab0610cd
DynamicSig[23].Name=Zusätzliche Absturzsignatur 2
DynamicSig[23].Value=0e01
DynamicSig[24].Name=Zusätzliche Absturzsignatur 3
DynamicSig[24].Value=0e01d9273132497b58cc3792f8af657a
DynamicSig[25].Name=Zusätzliche Absturzsignatur 4
DynamicSig[25].Value=4eb3
DynamicSig[26].Name=Zusätzliche Absturzsignatur 5
DynamicSig[26].Value=4eb3372730c134255f47918244aa9d46
DynamicSig[27].Name=Zusätzliche Absturzsignatur 6
DynamicSig[27].Value=a3b5
DynamicSig[28].Name=Zusätzliche Absturzsignatur 7
DynamicSig[28].Value=a3b5abeb685bc26ab46653aa60185a6e
... 3 time
EventType=APPCRASH
EventTime=132277153626144152
ReportType=2
Consent=1
ReportIdentifier=0f6ea181-5d52-11ea-813c-0025904667c6
IntegratorReportIdentifier=0f6ea180-5d52-11ea-813c-0025904667c6
Response.type=4
Sig[0].Name=Anwendungsname
Sig[0].Value=mmc.exe
Sig[1].Name=Anwendungsversion
Sig[1].Value=6.3.9600.18910
Sig[2].Name=Anwendungszeitstempel
Sig[2].Value=5a57a503
Sig[3].Name=Fehlermodulname
Sig[3].Value=KERNELBASE.dll
Sig[4].Name=Fehlermodulversion
Sig[4].Value=6.3.9600.19425
Sig[5].Name=Fehlermodulzeitstempel
Sig[5].Value=5d26b6e9
Sig[6].Name=Ausnahmecode
Sig[6].Value=00000000
Sig[7].Name=Ausnahmeoffset
Sig[7].Value=000000000000908c
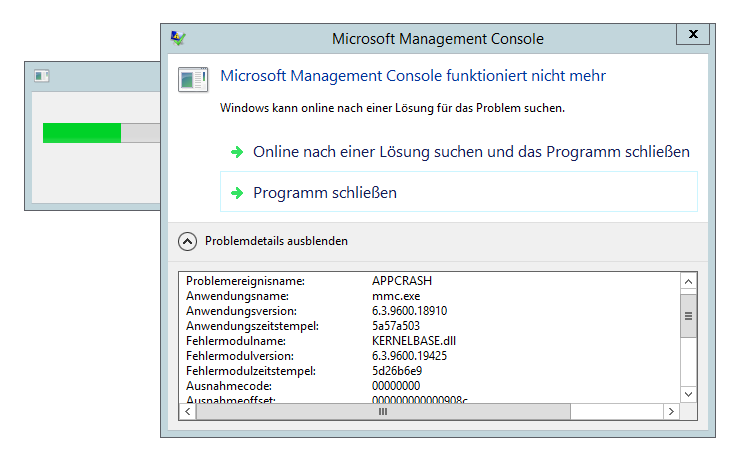
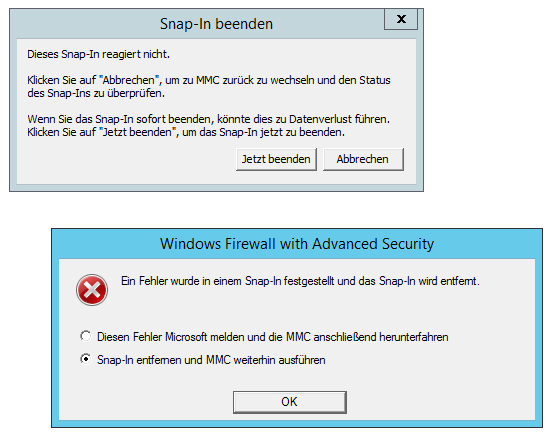
As far as we figured out at the end, the issue is only locally exploitable for x64 architectures and has nothing to deal with the local memory but the kernelbase dynamic link library of windows 2012 R2. The same issue can be provoked in case a third software is using the data of the firewall rules to sync like parallels plesk for example. The internal firewall uses the setup rules to move the data through with the regular windows libraries and the snapshot functions compromises. In the moment the mmc.exe crashs, the system is widely open for further manipulation because the security center and other mechanisms are not anymore correctly running. To exploit the issue it is required to use a system user account without administrative privileges.
Due to the support and product the manufacturer (msrc team) decided to not process a security update but recognized the issue for the further.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2235



Comments
i just had a look at it and
Add new comment