Zero Day Vulnerability in Deutsche Bahn Ticket Machine Series System uncovered
Whitehat in action discovers Kiosk Escape & Escalation via Windows PasswordAgent
In the last few days some Whitehat hackers of the Vulnerability Lab have come together for an action at the station wilhelmshöhe in kassel (Germany) to deal with a new security hole of the Deutsche Bahn ticket machines. While the station woke up quietly at 05:00 in the early morning without security personnel, the action took place. In the first step of this article, we want to focus on the vulnerability and then explain our approach as a group.
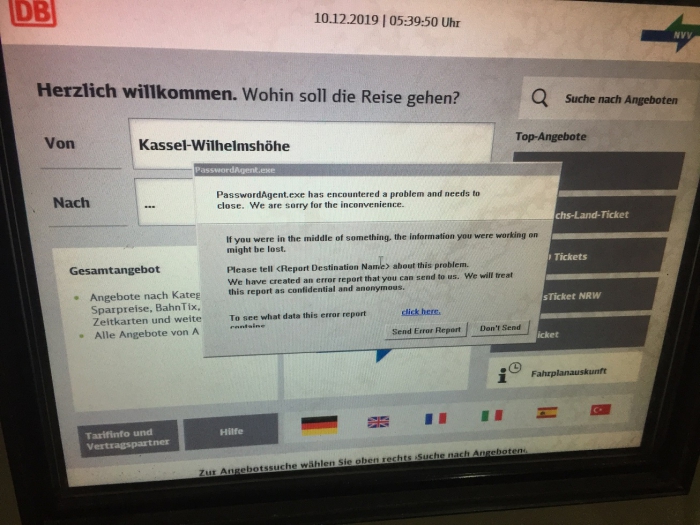
It is possible for local attackers to break out of the kiosk mode of the Deutsche Bahn vending machine application if the Password Agent (PasswordAgent.exe) of the system receives a timeout or has a runtime error in the program itself in the background. These errors can occur due to aborted sessions, unclean logout or common errors when using the application at system level.
In the event of a local error, attackers can bring the error message to the foreground by pressing the number field - Cancel during a transaction. After the error message becomes visible, the attacker can click on a link of the error message where you can normally see what the error report contains. The attacker will then be redirected to a form in the error message, where he can search for errors in a collection of Microsoft articles via "Submit / Dont' Submit" or another link on the online path. There the attacker clicks on it and receives the web browser. From the web browser, the attacker retrieves the local system directory and can compromise the end device in peace.

Screenshot 1: Shows the error message which occurred on 6 machines simultaneously at different points
Screenshot 2: Shows how we used the second link to get the web browser of the application
Screenshot 3: Shows how we are located in the local system of the deutsche bahn machine
So the way is simple to move inside the local machine. Based on that we have the following simple concept.
PoC: Sheet
PasswordAgent.exe := Unexpected Error (Background) - Runtime/Session/Timeout
=> Transaction Application => Cancel := Unexpected Error (Background) - Runtime/Session/Timeout (Front)
=> Click Error Report => Click Search Collection => Web Browser => Local File System => PWND!
What are attackers able to do when system is accessable thus way?
1. Inject of local malware to the ticket machine (editor / debugger / cmd / ps - exp. ransomware)
2. Local manipulation for skimming devices to assist (transmit prepares)
2. Phishing of local credentials from screen via system (db browser application)
3. Intercept or manipulation to access card information (local file system - sniff/extract)
4. Crash or freeze the computer system (exp. kill of process / loop script)
5. Scare or joké activities (exp. html to front screens with web browser or by a new window process)
There are now several problems related to system hardening:
1. It should not be possible for users with system user rights to use the web browsers
2. The error message menu can be deactivated or completely modified
3. Some functions in menus can be deactivated by hardening (browser, messages & Co.)
4. Check that all other tasks are always running in the background or are being moved there permanently
5. The DeutscheBahn vending machine application and user interface should be shut down in the event of persistent errors in the foreground
6. The activities of the testing has been logged but did not triggered any alert for defense purpose
The incident was reported to the staff on site at wilhelmshöhe station at around 06:00 o clock in the morning. In the second step, we secured about 10 end devices on site via error cancel in the desktop by simply removing the error messages from all displays. So nobody could break out of the kiosk mode of the application via the user interface in order to compromise the machine. Shortly after we notified the Deutsche Bahn security department about the incient to stay legal in the responsible disclosure process, an email reply came back to our official inbox. In the email the Deutsche Bahnv stated
Screenshot 4: DeutscheBahn
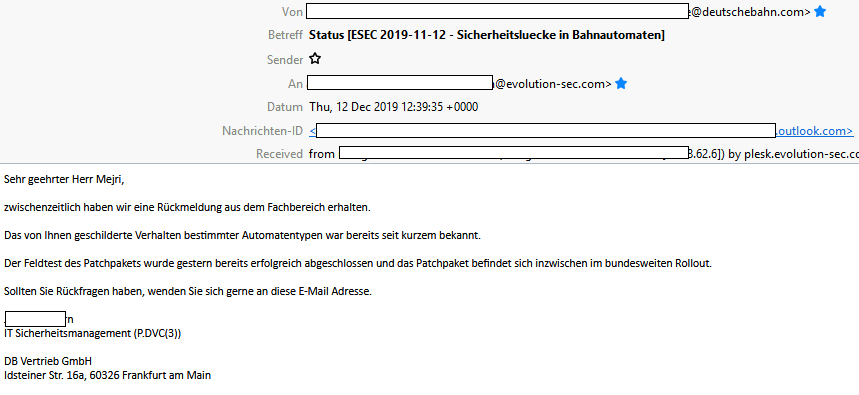
We will not comment on the email response, even if the response looks a bit little like ... "There's nothing to see here, please go on" ;) Please make your own judgement about it. In this particular case, the answer from the specialist department is only partially accurate and satisfactory. We had already dealed with the security department of the deutsche bahn some years ago and helped them to fix an issue within the db terminals panel.
We would like to take this opportunity to thank the it security department of Deutsche Bahn and the coordinators of itk management vertriebssysteme and remind you that there are some homework to be done so that incidents like this do not occur again in the future due to simple errors. especially around christmas time, the santa claus distributes the best gifts when nobody is at home or awake.
Update: 17.12.2019 by Deutsche Bahn
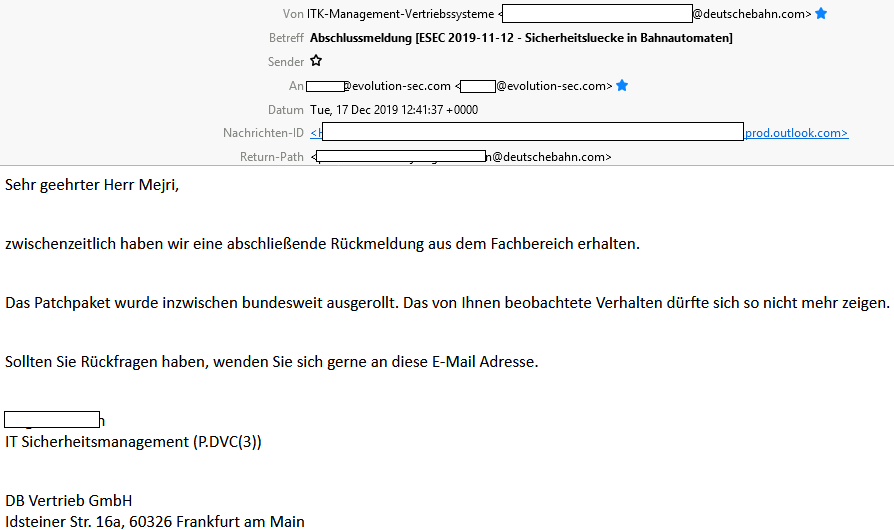
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2191



Comments
simple et bonne trouvaille
pretty lucky answer
Normalmente tendrían que
the fency thing is those atms
Add new comment