Apple iOS 12.0 - 12.1.1 - PassCode Bypass Vulnerability
Yes, we did it again!
Due to the last few years we have discovered several problems that bypass the password protection mechanism of ios. In recent weeks we have discovered a new problem affecting the latest ios versions 12.1 and 12.1.1.1.
The vulnerability allows password protection to be bypassed with the pin to allow unauthorized access to sensitive data such as contacts, image libraries and other standard setup applications. The problem affects all Apple iPhone and iPad devices with the ability to call (sim).
The access permission vulnerability is located in the Message menu to answer custom messages in combination with the standard app features available on the ios device. The problem allows you to combine different methods used to access and edit photos in restricted mode.
Using a hidden menu in combination with a glitch allows local attackers to access sensitive data from identification devices such as contacts, the image library, or standard applications.
The problem is processing to edit and write images while using Siri and custom SMS responses. The idevice does not need to be prepared in a special way. The default setup allows already to exploit the local vulnerability to gain unauthorized idevice access.
The basic requirements to exploit the issue are as follows ...
To exploit the vulnerability, the first step is to call Idevice with another random mobile phone. After the call arrives at the local identification device, the attacker responds with a custom SMS or Imessage. Once on the screen, the attacker takes a simple screenshot. After the screenshot is taken, the image is clickable and displayed on the left side of the screen. The attacker moves the duplicate image and the edit Image function opens.
The attacker rescales the picture to a small size. Then the attacker adds a signature and switches on the right buttom multiple times to the right side. The invisible menu is being marked with the siri highlight box. In that moment the attacker pushs the contact or add function and pushs as well a button next to the keyboard.
A manual description to trigger the issue is publicly available by now.
Manual Description:
1. Call the the iphone by another phone
Note: In case you do not know the number ask for it by siri (who i am)
2. Answer with a custom message on call
3. Write a short text inside the message box
4. Activate voiceover by siri
5. Make a screenshot
Note: When the screenshot is done it will be displayed for a short time on the left buttom
6. Twice push on the screenshot and hold with the last push the position on the touch screen
7. Then click on the plus on the right buttom and open to signature
8. Now push on the right buttom above the plus and switch with the finger all time to the right side of the display
Note: The message menu will be accessed by now in the background and there will be several functions available
9. Scale the picture to a small size
10. Move by switching with the finger to the name or the + / plus button
11. Now push the home button to activate siri and save the screenshot with the signature / edit mode
12. Now the contacts page is available without pin authentication by pushing twice the screenshot
Note: From there the attacker can move to different other functions mail, contacts, pictures and other functions
13. From outside the attacker can then access the contacts list by a screenshot and then double push on the image at left screen buttom
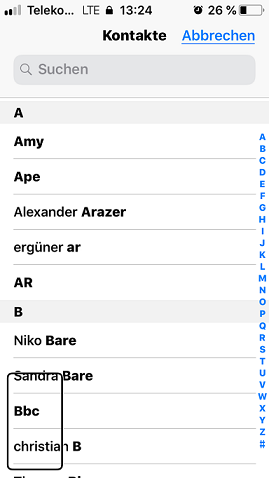
The following picture shows the locked screen with access to the contacts list of the targeted ios 12.1 iphone device. By pushing the contacts in the list the attacker can move through several functions like the pictures library or default installed applications like email, phone app, imessage or sms.




2. Disable in the lock settings the custom sms answer on calls
3. Deactivate the voiceover function
4. Deactivate the favorite keywords above the keyboard menu, which can reveal your last written words, contacts or other text information
Finally the apple product security team was not able to acknowledge us for the new finding because they was unable to replicate the issue in 12.0, 12.1 and 12.1.1. After sending several videos, pictures and information the state of the tracked issue was still unchanged, so we uncovered the problematic publicly on xmas 2018 to ensure people can stay safe.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2162
Video: https://www.vulnerability-lab.com/get_content.php?id=2169



Add new comment