Wickr Inc - App Clock & Message Deletion Glitch
Independent Researcher scores in Wickr Inc Bug Bounty Program
The security researcher Hanno Horrmeyer uncovered a vulnerability in the wickr inc ios and android application in 2017 Q1-2. He began to research for other program participants and teams after his disclosure to the bug bounty program was not correctly acknowledged. After a short conversation we decided to cover the hannos research as independent vulnerability laboratory researcher to assist him without any charges. If you believed until today that wickr really securly deletes your messeges, you will in a minute think different about that topic. The vulnerability details read as follows and was acknowledged finally with a bug bounty in 2017 Q4.
The unique selling points (USP’s) of Wickr are the End-to-End Encryption combined with the self destructing Messages. The bug about to be presented is demonstrating that the entire self destructing part can effectively be corrupted and additionally supposedly deleted messages from the past can be fully recovered. This includes any type of message attachment as well.
The affected Wickr Product is the Wickr Me Messaging App Version 2.6.4.1 on Android & iOS.
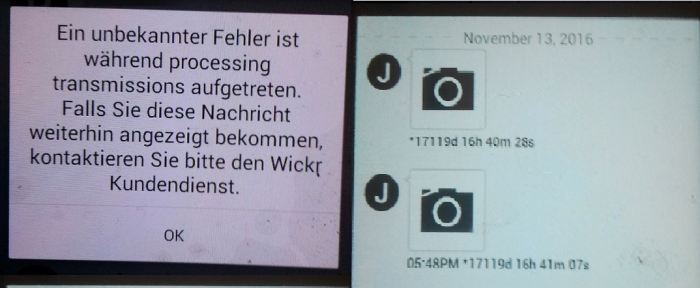
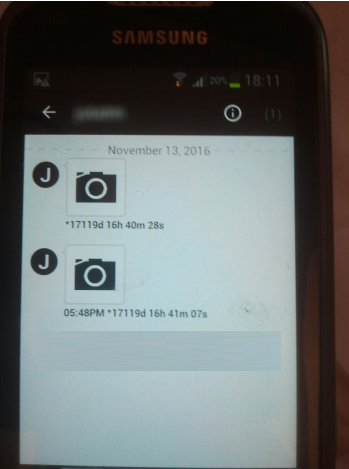
By causing a connection loss during the login process of Wickr, the App will let the User view chat history that was expired / self destructed and therefore previously no longer visible. After a successful corruption of the login process, most of the times you will be presented with the error message, shown on the right.
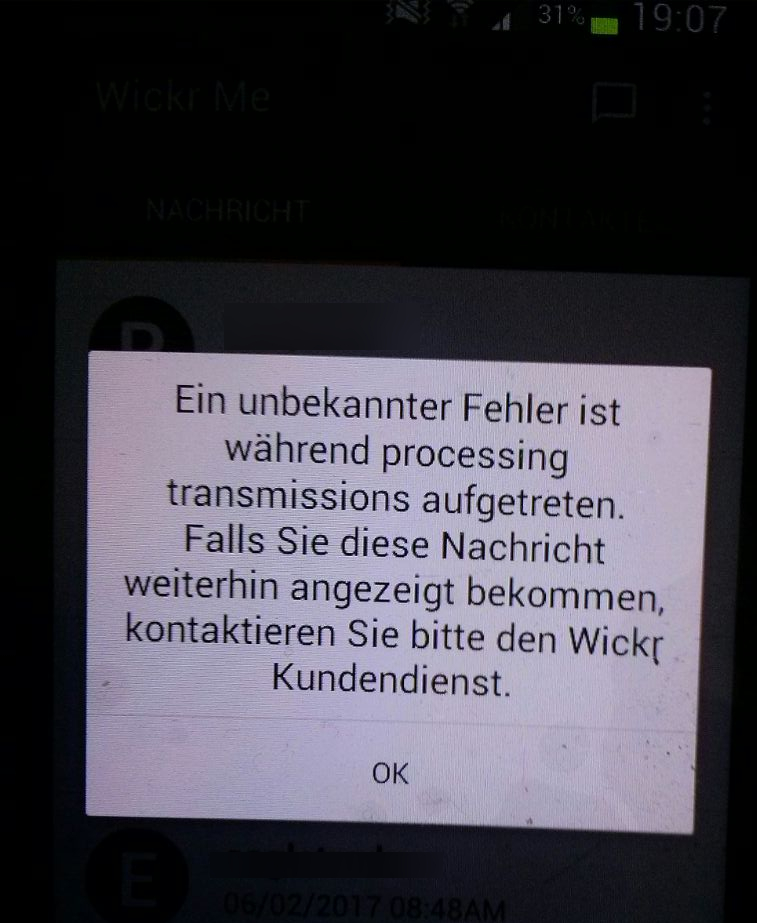
Now some of the opened chats contain messages, which were not visible before. Messages are shown rather randomly and can be reproduced at another corrupted session, however not each in particular.
The messages destruction timer is either set to a high number (~1777 days) or not shown at all. Pictures, Recordings, Videos and all types of messages can be restored.
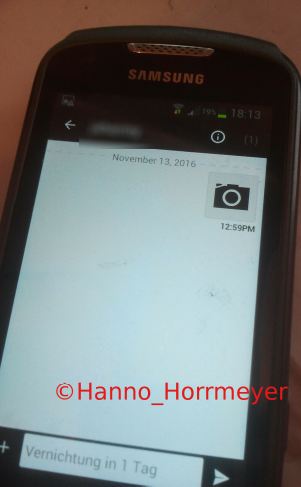

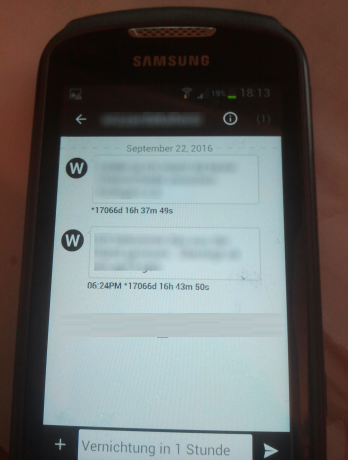
Manual steps to reproduce the vulnerability:
Wickr Me starts, asking me for my password
-
Logged out state of the wickr app. Do not store the password for auto login.
-
Type in the password
-
Press the login button
-
Right after button has been pressed -> Connection loss due to tunnels e.g. (must be quick before wickr gets logged in properly)
-
Logged in with no connection -> Alert Dialog states something similar to: "Something was not right with your login and you might see messages that were supposed to be deleted"
-
Open the active chats, which should not contain any messages but instead randomly they do.
-
The deleted messages are shown without any timer or with the destruction timer set to a outstandingly high number around 1777 days.
-
Voilla, Thats how you restore supposedly deleted messages, pictures, anything in your Wickr Me App.
These vulnerabilities were officially confirmed by Wickr in qarter 3 of 2017 and eventually fixed in the latest Updates up to 2018. The security researcher received a commercial reward for reporting the valid vulnerabilities in scope of the official bug bounty program.
Reference(s):
https://www.vulnerability-lab.com/get_content.php?id=2107
https://www.vulnerability-lab.com/show.php?user=HannoH



Add new comment