Telekom Cloud & Web SSO vulnerable to Bypass & Persistent XSS Attacks
Telekom Cloud - MyworkPlace Business Frontend & Backend Vulnerabilities
Researchers of the vulnerability laboratory core team discovered multiple persistent cross site scripting web vulnerabilities to the telekom cert team in mid december 2016. The security vulnerabilities was located in the new telekom cloud business service and myworkplace for paying customers.The "Deutsche Telekom" offers the "Open Telekom Cloud" a secure Infrastructure as-a-service offering based on "OpenStack". The hosting is located in highly secure data centers of the telekom in germany.
The security risk of the persistent input validation vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 4.3. Exploitation of the persistent input validation web vulnerability requires low user interaction and a low privilege web-application customer user account. Successful exploitation of the vulnerability results in session hijacking, persistent phishing attacks, persistent external redirects to malicious source and persistent manipulation of affected or connected application modules.
Request Method(s):
[+] POST
Vulnerable Service(s):
[+] Telekom Cloud (websso.t-systems.de)
Vulnerable Module(s):
[+] Cloud & Service Registration
Vulnerable Input(s):
[+] Vorname
[+] Nachname
Vulnerable Parameter(s):
[+] firstName
[+] lastName
Affected Module(s):
[+] Frontend (Profile)
[+] Backend (Preview Information)
[+] Serice Emais (Outgoing on Interaction)
Proof of Concept (PoC):
The vulnerability can be exploited by remote attackers with low privilege web-application user account and with low user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Open the telekom cloud webpage
2. Move to the registration
3. Include your values and an email that you administrate
4. Start a live session tamper for the http protocol
5. Submit the registration and change in the live http request via tamper the name parameters to test payloads
6. Continue the request to receive the server answer 200OK
7. Check the email were the first execution point occurs and then request for example a new password to see the effects
8. In the next step watch the user profile that displays the database credentials
9. Now, moe over as administrator in the backend and approve the information encode for the accounts to watch the execution point
10. Successful reproduce of the persistent remote vulnerability in the telekom cloud sso web service!
--- PoC Session Logs [POST] (Inject) ---
Status: 302[Found]
POST https://apps.telekomcloud.com/accountSetup/46bc12d7-5226-41d4-83e5-976d6...
Mime Type[text/plain]
Request Header:
Host[apps.telekomcloud.com]
User-Agent[Mozilla/5.0 (Windows NT 10.0; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Referer[https://apps.telekomcloud.com/accountSetup/46bc12d7-5226-41d4-83e5-976d6...
Cookie[rfat=0;JSESSIONID=10E4F0369D506A3952B1440093C7AE95-n1; keychain=92c06fef18bdf4b5d3eb9d2ab345b2768a365d761e04ce1cefc38fbe593ec93f7ba3a91b04d3a3c31dac0fcfb35a94c6c921b6ffbcf8469eb583bf4df1dd55f0]
POST-Daten:
id18_hf_0[]
titleTypeRadioGroup[radio21]
firstName[MALICIOUS INJECTED PAYLOAD!]
lastName[MALICIOUS INJECTED PAYLOAD!]
passwordBorder%3ApasswordBorder_body%3Apassword[chaos666]
confirmBorder%3AconfirmBorder_body%3AconfirmPassword[chaos666]
companySetupForm%3AcompanyNameBorder%3AcompanyNameBorder_body%3AcompanyName[KPI+SMU]
companySetupForm%3ArequiredPhoneNumber%3ArequiredPhoneNumber_body%3AphoneNumber[31337]
companySetupForm%3AsizeRadioGroup[SMALL]
companySetupForm%3AinputIndustry[1]
marketingPanelContainer%3AmarketingCheckbox[on]
privacyPanel%3AprivacyCheckboxBorder%3AprivacyCheckboxBorder_body%3AprivacyCheckbox[on]
noStepActivateButton[]
Response Header:
Date[Sun, 04 Dec 2016 14:13:05 GMT]
X-UA-Compatible[IE=Edge]
Expires[Thu, 01 Jan 1970 00:00:00 GMT]
X-Frame-Options[SAMEORIGIN]
Strict-Transport-Security[max-age=0 ; includeSubDomains]
Set-Cookie[JSESSIONID=8DF92319BF793069FE9A216084CFDE64-n1; Path=/; Secure; HttpOnly
userCompanyInfo=%7B%22userCompanyHash%22%3A%227bb1053b07687b619bcef44222ed892a%22%2C%22lastModified%22%3A1480860785925%7D;
Domain=.telekomcloud.com; Path=/; Secure; HttpOnly]
Location[https://apps.telekomcloud.com/home?src=activateAccount]
Content-Length[0]
Access-Control-Allow-Origin[https://cloud.telekom.de]
access-control-allow-credentials[true]
access-control-allow-methods[POST, OPTIONS]
access-control-allow-headers[Accept-Encoding, Origin, X-Requested-With, Content-Type, Accept]
Connection[Keep-Alive]
Content-Type[text/plain]
Vulnerable Source: Emails - Reset, Register & Co.
<img class="imgClass" style="margin: 0px; padding: 0px; border: medium none currentcolor;
display: block;" alt="Herzlich Willkommen in der TelekomCLOUD"
src="mailbox-message://%40evolution-sec%2Ecom@pop3.evolution-sec.com/Inbox#704264296?header=saveas&part=1.2.5"
width="580" height="275">
</td>
</tr>
</tbody>
</table>
<!-- Start Container -->
<div> <!-- Start Anschreiben -->
<table class="container" width="580" cellspacing="0" cellpadding="0" border="0">
<tbody>
<tr>
<td style="height: 20px; line-height: 0; font-size: 0px;" valign="top"> </td></tr>
<tr>
<td class="mobile" style="width: 580px;">
<p style="padding: 0px; text-align: left; color: #4b4b4b; line-height: 20px;
font-family: Arial, sans-serif; font-size: 14px; margin-top: 0px; margin-bottom: 0px;">
<strong>Sehr geehrte(r) Herr/Frau >"<[MALICIOUS INJECTED SCRIPT CODE PAYLOAD EXECUTION!]>,</strong><br /><br />
ab sofort ist Ihr Account im Service-Portal MyWorkplace aktiviert.
Auf MyWorkplace können Sie Ihre Cloud Lösung konfigurieren und verwalten.
Sobald Sie Ihren gebuchten Cloud-Service nutzen können, erhalten Sie eine Ready-for-Service-E-Mail.</p>
</td></tr></tbody>
</table>
<!-- Ende Anschreiben -->
</div>
<div> <!-- Start Fliesstext + opt. link -->
<table border="0" width="580" cellspacing="0" cellpadding="0" class="container">
<tbody><tr><td valign="top" style="height: 20px; line-height: 0; font-size: 0px;"> </td>
</tr><tr>
... ... ... ...
<td class="mobile" width="580"><img alt="Herzlich Willkommen in der TelekomCLOUD" class="imgClass" style="margin: 0; padding: 0;
border: none; display: block;" src="https://www.websso.t-systems.de/kulipa/public/optinmail/visual.jpg"
width="580" height="275" border="0"></td></tr>
</tbody></table> <!-- Start Container -->
<div>
<!-- Start Anschreiben -->
<table class="container" width="580" cellspacing="0" cellpadding="0" border="0">
<tbody>
<tr>
<td style="line-height: 0; font-size: 0" valign="top" height="20"> </td>
</tr>
<tr>
<td class="mobile" width="580">
<p style="font-family: Arial, sans-serif; font-size: 14px; line-height: 20px; color: #4b4b4b;
padding: 0; Margin-bottom: 0; Margin-top: 0; text-align: left;">
<strong>Sehr geehrter Herr >"<[MALICIOUS INJECTED SCRIPT CODE FIRSTNAME EXECUTION!]> <[MALICIOUS INJECTED SCRIPT CODE LASTNAME EXECUTION!]>,</strong>
<br> <br> vielen Dank für Ihre
Registrierung im <strong>Telekom</strong>CLOUD
Portal. <br> <br> Um Ihren Account zu
aktivieren, bitten wir Sie nun Ihr Passwort für Ihren
Zugang festzulegen. Bitte gehen Sie dafür auf die
Aktivierungsseite:
</p></td></tr>
</tbody>
</table>
URLs:
https://cloud.telekom.de/de/registrieren/
https://www.websso.t-systems.de/
Multiple solutions to resolve the vulnerabilities are mentioned in the advisory by the researchers as follows ...
Solution - Fix & Patch
The vulnerability in the cloud sso web service can be patched by a secure parse of the vulnerabel firstName and lastName input fields. Restrict via disallowing the usage of special chars and script codes within the submit POST method request outside the basic form input. Parse all output locations in the different layers were the execution takes place ... frontend, backend & outgoing emails. In the outgoing.
At the end the researchers has been acknowledged by the german telekom cert within january 2017. The issue has been resolved to protect the backend and frontend web-application of myworkplace. The patches has been improved by the vulnerability lab core team to ensure the issues has been resolved permanently.
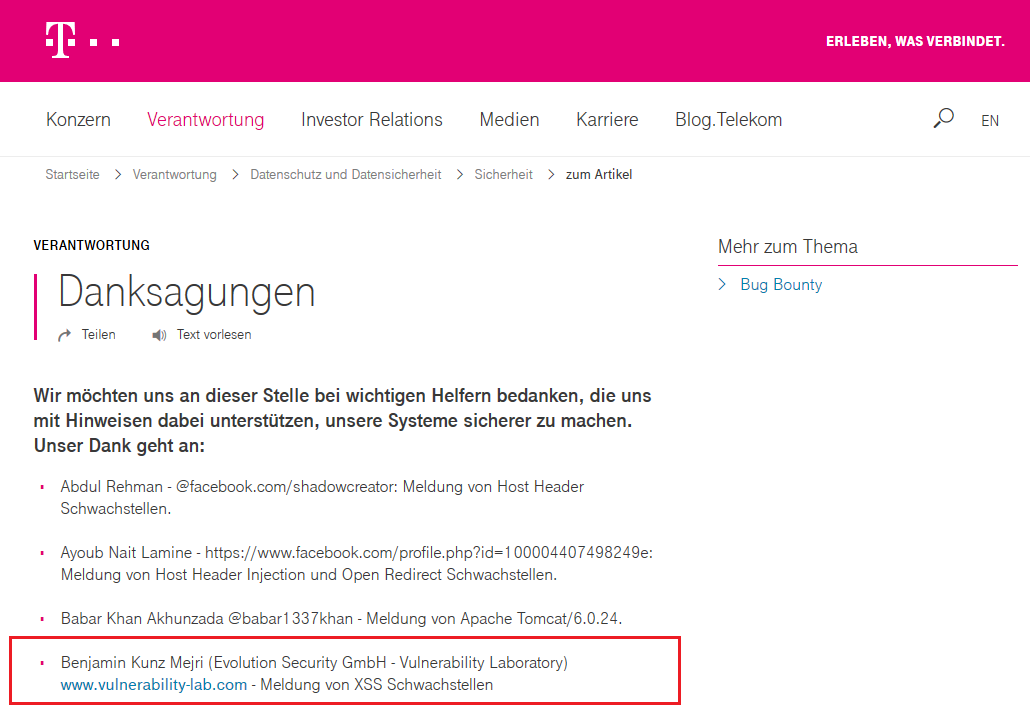
Thanks to the German Telekom CERT for cooperation and coordination to resolve the reported security vulnerabilities!
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2021
Reference(s):



Comments
zrnscspw888@gmail.com
Add new comment