Apple Product Security Acknowledgements - Multiple Vulnerabilities
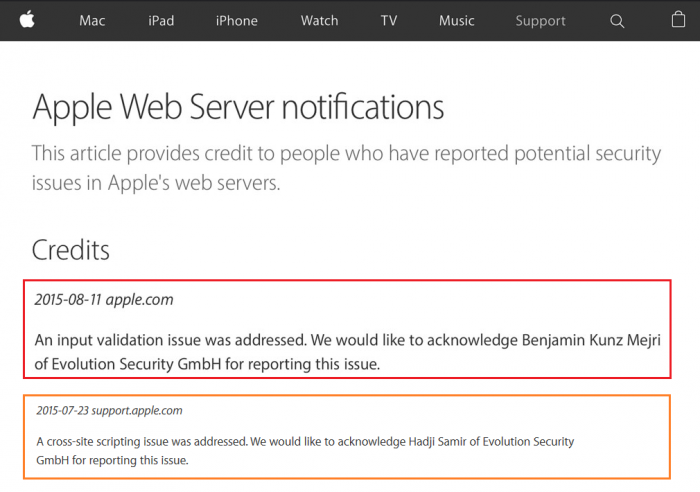
Multiple Security Acknowledgements in 2015 Q4 by Apple Cupertino
In the last qarter of the year 2015 the core research team of the vulnerability laboratory received multiple acknowledgements by apple for early reported zeroday vulnerabilities. One of the issue affected the main apple.com domain of cupertino and the second issue affected the support.apple.com community. The first vulnerability was a filter bypass issue disclosed about 2 month ago. The second vulnerability report was disclosed begin of december 2015 by apple. The both researcher Hadji Samir and Benjamin Kunz Mejri discovered both bugs together after there separate analysis.
#1: Apple iTunes & AppStore - Persistent Invoice Vulnerability
The apple itunes and appstore is taking the device cell name of the buying users. Remote attackers can manipulate the name value by an exchange with script code (special chars). After that the attacker buys any article in the appstore or itunes-store. During that procedure the internal appstore service takes the device value and does encode it with wrong conditions. The seller account context runs since the error with the injected script code occurs and gets this way re-implemented to the invoice. Thus results in an application-side script code execution in the invoice of apple. Remote attackers can manipulate the bug by interaction via persistent manipulated context to other apple store user accounts. The vulnerability can be exploited by remote attackers and the malicious receiver/sender email is *@email.apple.com. The invoice is present to both parties (buyer & seller) which demonstrates a significant risk to buyers, sellers or apple website managers/developers. The issue impact also the risk that a buyer can be the seller by usage of the same name to compromise the store online service integrity.
The security risk of the persistent input validation and mail encoding web vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 5.8. Exploitation of the persistent input validation and mail encoding web vulnerability requires a low privilege apple (appstore/icloud) account and low or medium user interaction. Successful exploitation of the vulnerability results in session hijacking, persistent phishing attacks, persistent redirect to external sources and persistent manipulation of affected or connected service module context.
Vulnerable Module(s):
[+] Apple Invoice
Vulnerable Parameter(s):
[+] device-cell
[+] type cell
Affected Service(s):
[+] Appstore & iTunes
Sender(s)/Receiver(s):
[+] @email.apple.com
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1512
#2: Apple Support - Permission Exception Web Vulnerability
The second vulnerability is located in the `specs` and `downloads` module of the apple support online-service website. Remote attackers are able to inject malicious script codes to client-side application requests. Remote attackers are able to prepare special crafted weblinks to execute client-side script code that compromises the apple user/admin session data. The execution of the script code occurs in the permission denied exception handling of the support website. The injection point of the issue is the specs and downloads module. The attack vector of the vulnerability is located on the client-side of the online-service and the request method to inject or execute the code is GET.
The online-service of the apple support site impact a basic validation that will become visible after the first payload of the poc is executed. This filter parses the input of basic injected frames and script tags but img src and the new html5 tags bypass the mechanism to compromise.
The security risk of the non-persistent cross site vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.3.Exploitation of the non-persistent cross site scripting web vulnerability requires no privilege web application user account and low user interaction. Successful exploitation of the vulnerability results in session hijacking, non-persistent phishing, non-persistent external redirects, non-persistent load of malicious script codes or non-persistent web module context manipulation.
Request Method(s):
[+] GET
Vulnerable Service(s):
[+] Apple Support (support.apple.com)
Vulnerable Module(s):
[+] downloads
[+] specs
Affected Module(s):
[+] Exception Handling - Permission Denied
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1531
Other Apple Product Vulnerabilities ...
http://www.vulnerability-lab.com/search.php?search=apple&submit=Search




Add new comment