PayPal Inc - 2FA & Security Approval Restriction Auth Bypass Session Vulnerability
PayPal Inc - 2FA & Security Approval Restriction Auth Bypass Session Vulnerability
The Vulnerability Laboratory CEO Benjamin Kunz Mejri discovered a restriction filter bypass vulnerability in the official PayPal Inc mobile API for Apple iOS. By processing multiple login Mejri discovered a vulnerability in the mobile API for Apple iOS and Android OS. Normally an user tries to login and if the account is restricted by several requests, an input form popup opens to call PayPal or write a support ticket mail. By requesting the form multiple times with an existing account, Mejri was able to bypass the authentication verification check and approve the account owner with compromised cookies.
The vulnerable mobile app API loads the website context and the user is able to include his own user account inside of the identity check with a browser engine. Even if the account is restricted the user can access via the mobile API by using the existing cookies. The security identity is used to verify that no user logs in to unauthorized- or restricted accounts. By using the vulnerable mobile API Mejri demonstrates in a proof of concept video how he bypasses the validation and how it should look normally with a final request.
Since today the multiple times acknowledged researcher did not received a bug bounty reward for the obviously valid security issue because PayPal was not able to recreate the bug finaly. The researcher send pictures, videos, and logs but nothing helped at the end. Later the issue was untrustworthy resolved by requesting a duplicate (4 month later). The same happened to the German researcher the second time after his last valid report in the mobile app API. The last issue was fixed and accepted after the open disclosure.
Severity Level: The security risk of the remote mobile API identity approval check bypass is estimated as high. (CVSS 6.1)
Affected Product: Mobile Web Application (API) 2015 Q2
Proof of Concept (PoC)
The security vulnerability can be exploited by remote attackers with low privileged application user account and without user interaction. For security demonstration or to reproduce the security vulnerability follow the provided information and steps below to continue. The video demonstrates a flaw inside of the mobile app API that redirects an user account with restricted credentials inside of the app to the original website source. The cookies authorize the account to login even if the regular portal denies it because of the identity approval. The issue reveals a significant risk to user accounts because of fraud and account theft.
The video demonstrates a security bug in the official PayPal mobile iOS API. The bug allows an attacker to bypass the account restriction by usage of a validation flaw inside of the service API. The identity check approves restricted user accounts, Mejri demonstrates how to bypass the authentication. An attacker can bypass the validation by multiple requests and dumps the real website for login inside the App with cookies and header informations.
Note: We have already verified that the issue is also exploitable in the mobile Android App API of PayPal Inc.
Pictures Description: PoC
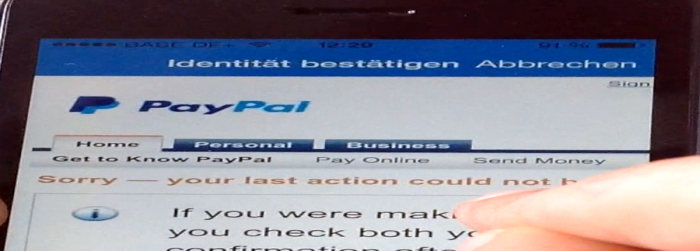
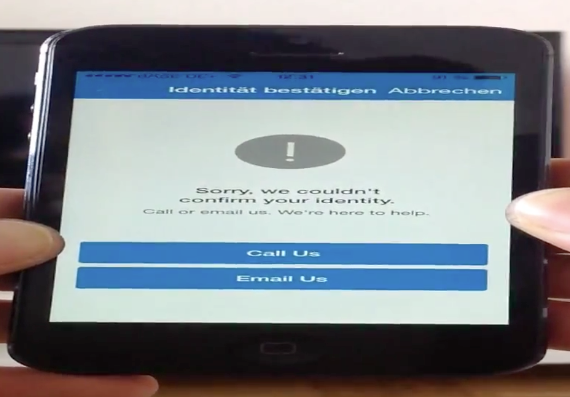
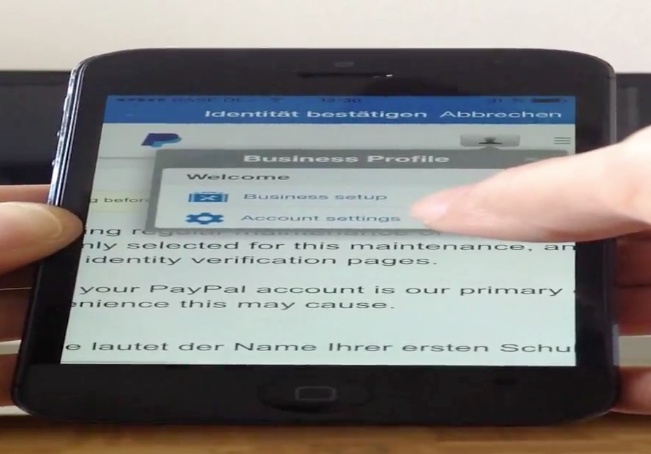
The first image shows how it looks like when the account is being blocked. The user is not anymore able to do anything then to call or write a email to solve the problem. The first image shows how it looks like when the account is being blocked. The user is not anymore able to do anything then to call or write a email to solve the problem.
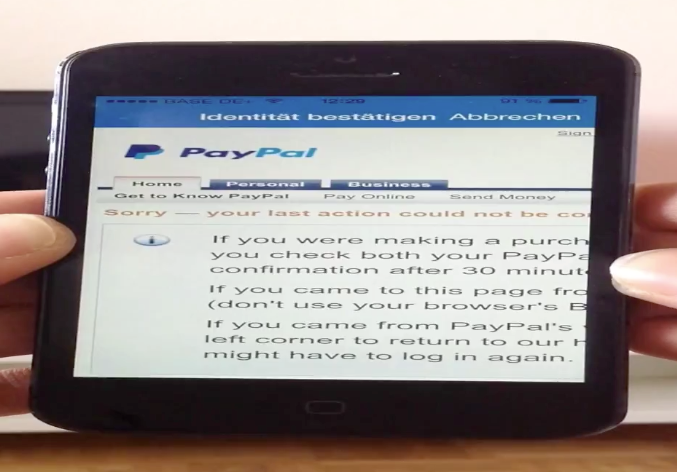
After usage of a valid cookie that is not expired by storing in the device we was able to include it
twice. So the results was that inside the identity check the website was loaded by a redirect.
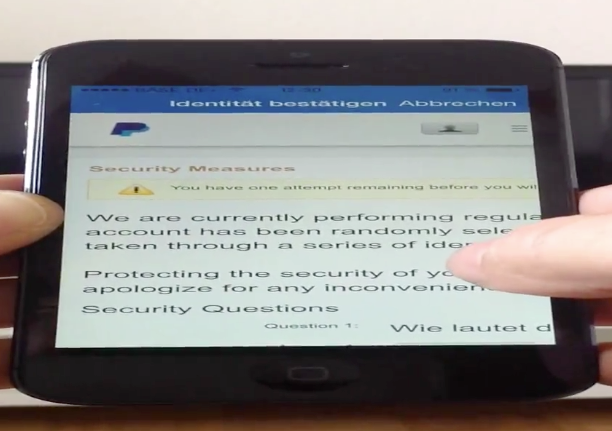
After the load to the website in the inner app context we tried to login to the paypal online-service.

With the cookies in the app and the inner context load of the website we was able to successful login to the paypal website with the blocked credentials.
We approved what functions are available and can be changed in that status and decided to use the currency. We changed the currency of € in candian dollar and saved it with the compromised cookie via mobile app api.

In a live video demonstration the researcher shows the developers on how to recreate and exploit the issue ...
Video: PayPal Inc Bug Bounty 2015 - Stored Cookies Remote (2FA) Auth Bypass Vulnerability (API)
Vulnerability Disclosure Timeline
2015-04-30: Researcher Notification & Coordination (Benjamin Kunz Mejri - Evolution Security GmbH)
2015-05-02: Vendor Notification (PayPal Inc - Security & Bug Bounty Team)
2015-09-01: Vendor Response/Feedback (PayPal Inc - Security & Bug Bounty Team)
2015-**-**: Vendor Fix/Patch (PayPal Inc - Developer Team)
2015-09-02: Public Disclosure (Vulnerability Laboratory)
Reference(s):
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1486
Video: https://www.youtube.com/watch?v=Gzq8TD2Co9Y
Full Advisory (PDF): http://www.vulnerability-lab.com/resources/documents/pp115.pdf
https://threatpost.com/researchers-outline-vulnerabilities-in-yahoo-paypal-magento-apps/114644/
http://www.theregister.co.uk/2015/09/04/paypal_bug_brace_xss_2fa_bypass/
http://www.securityweek.com/paypal-mobile-apps-plagued-authentication-flaw-researcher
http://securityaffairs.co/wordpress/39951/hacking/authentication-paypal-mobile-app.html
http://news.hitb.org/content/paypal-mobile-apps-plagued-authentication-flaw-benjamin-kunz



Comments
Similar to Verizon.net
Reminds me of the Verizon.net exploit I discovered. Same issue, different method of attack, equally high security threat.
you are the king of bug
Add new comment