ZTE ZXV10 W300 v3.1.0c_DR0 - Remote Session Delete Vulnerability
ZTE ZXV10 W300 v3.1.0c_DR0 - UI Session Delete Configuration Vulnerability
A session vulnerability has been discovered in the official ZTE Corporation ZXV10 W300 v3.1.0c_DR0 modem hardware. The security vulnerability allows remote attackers to block/shutedown or delete network settings and components.
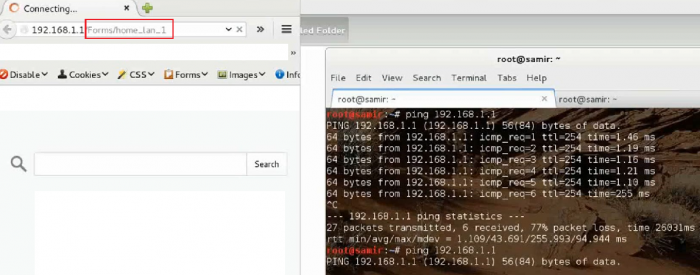
The LAN configuration post to /Forms/home_lan_1 and the page /home_lan_1 that stores the configuration of the router. Attackers can request via GET method the /Forms/home_lan_1 path and the modem will delete all the LAN configurations automatically. The problem is the GET method request with the /Forms/home_lan_1 path that deletes all the configurations. A hard reset is required after successful exploitation of the issue.
The video has been recorded by the vulnerability researcher hadji samir. The issue demonstrates a problem in the lan configuration settings of the firmware. The session allows anybody to delete with one url post request the full network settings and information. By usage of an automatic routine we was able to demonstrate the bug deleting the current network setup. The issue is a session vulnerability that is possible to exploit because of no limitation to the request itself.
ZTE ZXV10 W300 v3.1.0c_DR0 - UI Session Delete Configuration Vulnerability (Video Demonstration)
Video: http://www.vulnerability-lab.com/get_content.php?id=1523
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1522



Comments
awesome topic
Creative analysis , I loved the facts.
Add new comment