Whitehat Hacker discovered details of an application-side Facebook Studio Dashboard Vulnerability
Whitehat Hacker discovered details of an application-side Facebook Studio Dashboard Vulnerability
The independent vulnerability laboratory researcher paulos yibelo discovered an application-side vulnerability in the official facebook studio online-service. The vulnerability has been tracked with ID "219162244" in the official bug bounty program.
The vulnerability is located in the dashboard module of the facebook studio service. Remote attackers are able to inject own script codes to the mobile client of facebook. After the inject of the payload the attacker can visit the dashboard service to execute the script codes. The vulnerability was disclosed during a pentest of the htmlentities on fb mobile client to the facebook studio service. The attack vector of the issue is persistent and the request method to inject is POST.
The security risk of the persistent vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 3.5. Exploitation of the persistent security vulnerability requires a low privileged web-application user account and medium user interaction. Successful exploitation of the vulnerability results in persistent phishing attacks, persistent session hijacking attacks, persistent external redirect to malicious sources and application-side manipulation of affected or connected module context.
Request Method(s):
POST
Vulnerable Module(s): Input
https://m.facebook.com/editprofile.php?type=contact&edit=website&refid=17
Affected Module(s): Output
https://www.facebook-studio.com/dashboard#_=_
Manual steps to reproduce the vulnerability
1. Open the following fb mobile webpage https://m.facebook.com/editprofile.php?type=contact&edit=website&refid=17 Note: (using Firefox)
2. Then remove all the URLs you have (if you have any)
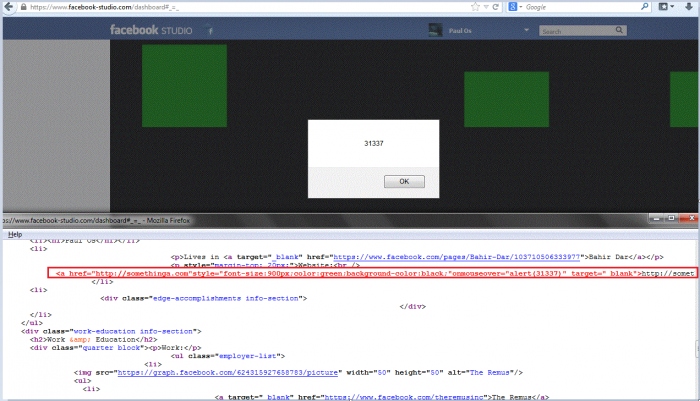
3. Add for example "https://somethinag.com/"onmouseover="alert(31337);." (without the quotes)
4. After that surf to https://www.facebook-studio.com/dashboard#_=_ and you will have your stored XSS. Note: Facebook didnt use htmlentity to the url when processing to add it in the database. When-ever being rendered, it wont be a second-order-injection.
5. Successful reproduce of the vulnerability! The full payload you need to add to your website is ... PoC: https://url-source.com/"style="font-size:900px;"onmouseover="alert(31337);.
Note: The full payload you need to add to your website is listed above.
Advisory: https://vulnerability-lab.com/get_content.php?id=1368



Comments
awesome
awesome
hAh
Important part of anybody life to be secured Sometimes really urgent to find or hire a hacker. We need to safe and protect our data and information from our cyber crime.
Metasploit
Лечение ВИЧ
WoWz
recension
Add new comment