Nasa Mars Orion Program - Researcher reveals Vulnerability in Boarding Pass to demonstrate violation

NASA Mars Orion Program - Researcher reveals Vulnerability in Boarding Pass to demonstrate violation
The german computer security expert and evolution security gmbh ceo - benjamin kunz mejri discovered a vulnerability in the official nasa mars orion program. The program allows public people to register a boarding pass that flies with the 4th december air-craft lunch as first around the world.
Oftenly we hear about people that send signals with code or frequences to space. In case of this issue it was totally different. The researcher send through a module of a nasa web service test code that was saved as official boarding pass ticket and should be flashed to a nasa silicon microchip (hardware). During the save procedure the code bypasses the security controls and should be saved at the end to a microship that is oboard the orion air-craft.
The researcher and penetration tester informed the us-cert about the vulnerability to coordinate a responsible disclosure. The nasa prevented a part of the code in september after the agency reported the incident. As result benjamin`s first boarding pass ticket got restricted and set to the nasa digital no fly list.

During the verification and tests by the agency the issue has been patched to prevent manipulation of nasa hardware next to the launch. The registration of the nasa orion program for public people is already closed since november. A part of the code that has been send twice was not prevented by the security agency that handled the internal case. Since today we had a lot of nice issues listed in the vulnerability laboratory but this issue earns some free pioneer freestyle points.
The advisory of the ceo reads as follows ... VU#666988
The issue is located in the firstname and lastname input fields of the nasa mission orion boarding pass module. Remote attackers are able to inject own script codes as firstname and lastname to compromise the embed boarding pass module of the nasa website. The request method to inject is POST and the attack vector is on the application-side of the vulnerable online-service module. After saving the malicious context to a boarding pass service the attacker can use the embed module to stream malicious codes as embed code execution through the boarding pass application of the nasa mars program website.
In case of the scenario we would like to fly as first and inject a script code that gets stored in the nasa dbms. In a special case of a pentest ago the user limit in the list runs that long since an error occurs. In case of the vote the nasa boarding pass list runs since the execution occurs and this will be the last entry that counts. Result is that the user with the injected special crafted code could be able to become the first for a ticket.
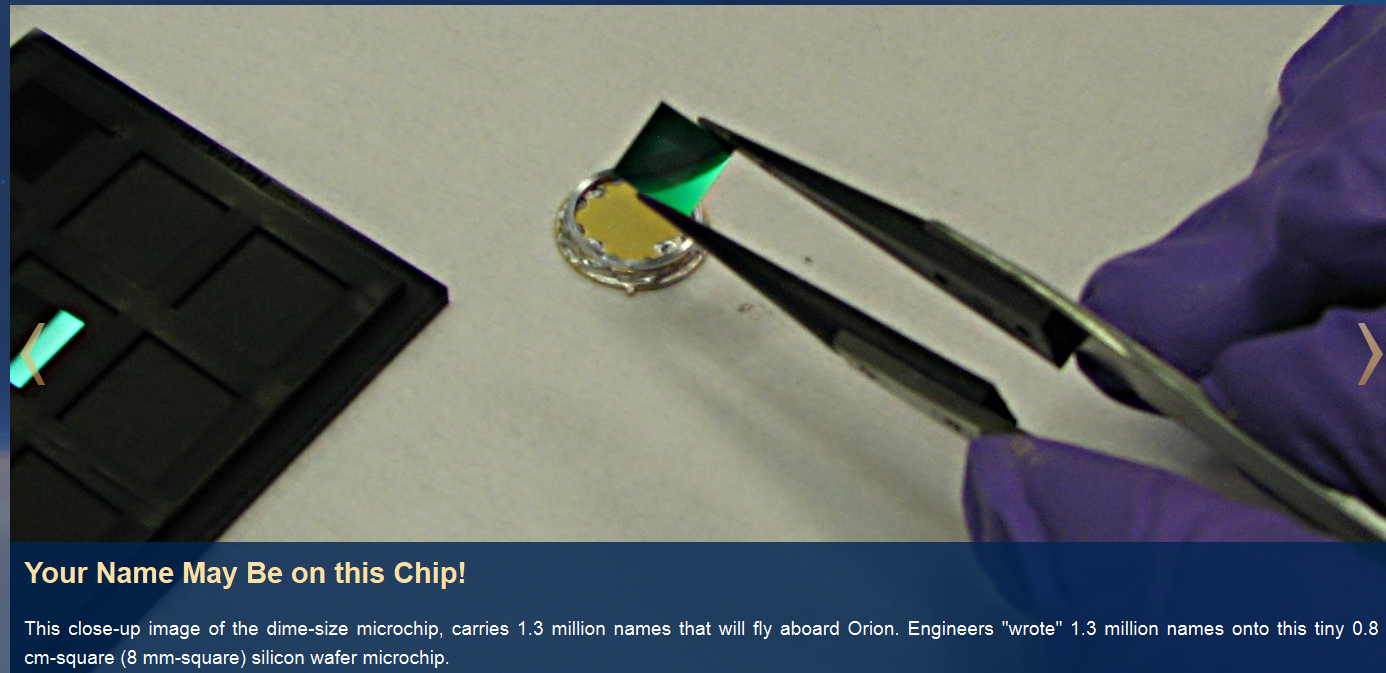
The web filter of the service encodes for example frames or script code tags. Img onloads can pass through the filter validation and the second instance filter of cloudflare to provoke an execution of script code in the embed nasa boarding pass module. The dime-size microship carries 1.3 million names that fly aboard Orion. Engeneers wrote 1.3 million names onto the tiny 0.8 cm sqare (8 mm square) silicon wafer microchip. To write the context to the chip the E-beam litography tool was used. After the input the payload gets flashed to a nasa chip that is configured to get send with mission orion to the space.
After the report to the US CERT Team informed the nasa about the issue and they closed the active ticket of the researcher. To ensure the ticket got closed the NASA included an image that shows the user in the official Nasa NO FLY List.

The researcher was that clever and injected 3 payloads.Two ids got observed by the nasa team and one passed through the procedure of verification and validation with id 344***.
In a statement the nasa wrote back that the chip itself is not at risk because there is no interaction or running code with it. In case of the research the code has been blocked since it got written to the silicon microchip. The context that gets written to the chip will be done manually for about 1.3 million users. In a later conversation to other security team they acknowledged that it would be impossible to check 1.3 million user accounts. By watching the last id of the researcher included as reference, everybody can see that the name value of an accepted ticket is not secure validated. He used the word Payload1 as firstname and Payload2 as second name to approve the validation.
The security risk of the embed code execution vulnerability in the boarding pass is estimated as medium with a cvss (common vulnerability scoring system) count of 6.0. Exploitation of the persistent remote web vulnerability requires no privileged application user account and only low user interaction. Successful exploitation of the security vulnerability results in session hijacking, persistent phishing, persistent external redirect through nasa domains and persistent manipulation of affected or connected module context.
Request Method(s):
[+] POST
Vulnerable Module(s):
[+] NASA Mars > Boarding Pass > Registration
Vulnerable Parameter(s):
[+] firstname
[+] lastname
Affected Module(s):
[+] NASA Mars - Boarding Pass (Embed Boarding Pass)
Proof of Concept
Embed Exploitcode (Mars BoardingCard)
<iframe src="http://mars.nasa.gov/participate/send-your-name/orion-first-flight/?acti... width="750" height="307" scrolling="no" frameborder="0"></iframe>
PoC: Boarding Pass J2M1000000158467 (send-your-name/orion-first-flight/?s=confirm&cn=334902)
<div class="boarding">
<img src="/images/general/layout/hexAccentImage.png" class="graphic-right">
<div class="certificate-id">J2M1000000158467</div>
<div class="name">
<div style="font-size:1.5em;">"><"<[PERSISTENT INJECTED SCRIPT CODE VIA FIRSTNAME VALUES!]"></div>
<div>"><"<[PERSISTENT INJECTED SCRIPT CODE VIA LASTNAME VALUES!]"></div></div>
<img src="/images/mep/send-name-to-mars/Boarding-Pass.png" class="image-boarding" alt="boarding pass">
<div style="bottom:0;left:0;position:absolute;z-index:100;background-color: rgba(85, 85, 85, 0.5);width:100%;">
<div style="position:relative;z-index:101;float:right;margin-right:0%;margin-top:2px;margin-bottom:2px;">
<a target="_blank" style="color:#eee;text-decoration:none;font-weight:normal !important;border:none;display:inline-block;padding-right:
8px;padding-right:10px;line-height:16px; font-family: 'Helvetica Neue',Arial,sans-
serif;font-size: 12px;" href="http://mars.nasa.gov/participate/send-your-name/orion-first-flight/"><div style="font-size:16px;margin-left:6px;float:
right;font-weight:bold;">+</div><div style="float:left;">Image Credit: mars.nasa.gov</div></a>
</div>
<br clear="all">
</div>
</div>
--- PoC Session Logs [POST] ---
Status: 200[OK]
POST http://mars.nasa.gov/participate/send-your-name/orion-first-flight/
Load Flags[LOAD_DOCUMENT_URI LOAD_INITIAL_DOCUMENT_URI ] Größe des Inhalts[144] Mime Type[text/html]
Request Header:
Host[mars.nasa.gov]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:32.0) Gecko/20100101 Firefox/32.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Accept-Language[de,en-US;q=0.7,en;q=0.3]
Accept-Encoding[gzip, deflate]
Referer[http://mars.nasa.gov/participate/send-your-name/orion-first-flight/]
Cookie[s_cc=true; s_vnum=1415451392569%26vn%3D3; s_sq=%5B%5BB%5D%5D; __utma=36124604.1688619800.1412859393.1412866915.1412869134.3;
__utmc=36124604; __utmz=36124604.1412859393.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); s_vi=[CS]v1|2A1B4302851D2BE0-40000107A00688CE[CE];
fsr.s=%7B%22v2%22%3A1%2C%22v1%22%3A1%2C%22rid%22%3A%22d036702-53567014-5eea-b60c-7e184%22%2C%22ru%22%3A%22http%3A%2F%2F
mars.nasa.gov%2Fparticipate%2Fsend-your-name%2Forion-first-flight%2F%3Fcn%3D161115%22%2C%22r%22%3A%22mars.nasa.gov%22%2C%22st%22%3A%22%22%2C%22cp%22%3A%7B%22
delivery_src%22%3A%22none%22%7D%2C%22to%22%3A3%2C%22mid%22%3A%22d036702-53567258-d212-8c96-20007%22%2C%22rt%22%3Afalse%2C%22rc%22%3Afalse%2C%22c%22%3A%22
http%3A%2F%2Fwww.nasa.gov%2F%22%2C%22pv%22%3A1%2C%22lc%22%3A%7B%22d3%22%3A%7B%22v%22%...
%22%3A%22a%22%2C%22rta%22%3A3%2C%22rts%22%3A3%7D%7D; __utma=259910805.435627752.1412859567.1412859567.1412859567.1; __utmc=259910805;
__utmz=259910805.1412859567.1.1.utmcsr=mars.nasa.gov|utmccn=(referral)|utmcmd=referral|utmcct=/participate/send-your-name/orion-first-flight/;
gpv_pe5=MEP%20-%20Send%20Your%20Name%20on%20NASA%27s%20Journey%20to%20Mars%2C%20Starting%20with%20Orion%27s%20First%20Flight;
s_invisit=true; __utmb=36124604.0.10.1412869134]
Connection[keep-alive]
POST-Daten:
action[submit]
pid[2]
FirstName[[PERSISTENT INJECTED SCRIPT CODE!]]
LastName[[PERSISTENT INJECTED SCRIPT CODE!]]
CountryCode[DE]
ZipCode[34128]
Email[research%40vulnerability-lab.com]
rp[]
recaptcha_challenge_field[03AHJ_VutiAgzfSZseCHPF92TfRrOZIIX-E6X078M8JwT-meq1bJthIybgz2TGRb_fl0QJdopcWTcJLSp2vy-DirSlgF370p4a4xnMI1D-
oypqwieb2Q5ckPquDsbrDV4Gp4u3B2jRORQn4KW4VEont0UfwogAMQgKBpqEjer1MrSEimu9LxVJRD3v-Jz40RRNTcR2FvsQqCL3hGPl27ca9RjTd7KrzM56-
xZRWdnXHfHmFNyLNSNzOrcCEvcv3ZW9oZVBoV0IQzL19g_zMXEOt61sAKOZbVDI0cT0DGUt2EGDlBJ81uj8dp0]
recaptcha_response_field[619]
Submit[SEND+MY+NAME]
Response Header:
Content-Type[text/html;charset=UTF-8]
Content-Length[144]
Connection[keep-alive]
Access-Control-Allow-Origin[http://marsdev.jpl.nasa.gov]
Cache-Control[max-age=600]
Date[Thu, 09 Oct 2014 15:46:04 GMT]
Location[./?s=confirm&cn=344616]
Server[nginx/1.1.19]
X-Cache[Miss from cloudfront]
Via[1.1 641720e73fe93af037f911457c12ae1e.cloudfront.net (CloudFront)]
X-Amz-Cf-Id[Ol1wi0YiljsLjsNOdJjXmYAjmvQgVMvLCh9WnjvbTFF0a4GKSVHifw==]
-
Status: 200[OK]
GET http://mars.nasa.gov/participate/send-your-name/orion-first-flight/?s=co...
Load Flags[LOAD_DOCUMENT_URI LOAD_REPLACE LOAD_INITIAL_DOCUMENT_URI ] Größe des Inhalts[7642] Mime Type[text/html]
Request Header:
Host[mars.nasa.gov]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:32.0) Gecko/20100101 Firefox/32.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Accept-Language[de,en-US;q=0.7,en;q=0.3]
Accept-Encoding[gzip, deflate]
Referer[http://mars.nasa.gov/participate/send-your-name/orion-first-flight/]
Cookie[s_cc=true; s_vnum=1415451392569%26vn%3D3; s_sq=%5B%5BB%5D%5D; __utma=36124604.1688619800.1412859393.1412866915.1412869134.3;
__utmc=36124604; __utmz=36124604.1412859393.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); s_vi=[CS]v1|2A1B4302851D2BE0-40000107A00688CE[CE];
fsr.s=%7B%22v2%22%3A1%2C%22v1%22%3A1%2C%22rid%22%3A%22d036702-53567014-5eea-b60c-7e184%22%2C%22ru%22%3A%22http%3A%2F%2Fmars.nasa.gov%2Fparticipate
%2Fsend-your-name%2Forion-first-flight%2F%3Fcn%3D161115%22%2C%22r%22%3A%22mars.nasa.gov%22%2C%22st%22%3A%22%22%2C%22cp%22%3A%7B%22delivery_src%22%3A
%22none%22%7D%2C%22to%22%3A3%2C%22mid%22%3A%22d036702-53567258-d212-8c96-20007%22%2C%22rt%22%3Afalse%2C%22rc%22%3Afalse%2C%22c%22%3A%22http%3A%2F%2F
www.nasa.gov%2F%22%2C%22pv%22%3A1%2C%22lc%22%3A%7B%22d3%22%3A%7B%22v%22%...
a%22%2C%22rta%22%3A3%2C%22rts%22%3A3%7D%7D; __utma=259910805.435627752.1412859567.1412859567.1412859567.1; __utmc=259910805;
__utmz=259910805.1412859567.1.1.utmcsr=mars.nasa.gov|utmccn=(referral)|utmcmd=referral|utmcct=/participate/send-your-name/orion-first-flight/;
gpv_pe5=MEP%20-%20Send%20Your%20Name%20on%20NASA%27s%20Journey%20to%20Mars%2C%20Starting%20with%20Orion%27s%20First%20Flight; s_invisit=true; __utmb=36124604.0.10.1412869134]
Connection[keep-alive]
Response Header:
Content-Type[text/html;charset=UTF-8]
Content-Length[7642]
Connection[keep-alive]
Access-Control-Allow-Origin[http://marsdev.jpl.nasa.gov]
Cache-Control[max-age=600]
Content-Encoding[gzip]
Date[Thu, 09 Oct 2014 15:46:05 GMT]
Server[nginx/1.1.19]
Vary[Accept-Encoding]
X-Cache[Miss from cloudfront]
Via[1.1 641720e73fe93af037f911457c12ae1e.cloudfront.net (CloudFront)]
X-Amz-Cf-Id[fcCNBQ3RNkRMQ_9nK-1v_ConkoOko6ttxX2F0IDcwKGyovh3SJSAZg==]
Reference(s):
http://mars.nasa.gov/
http://mars.nasa.gov/participate/
http://mars.nasa.gov/participate/send-your-name/
http://mars.nasa.gov/participate/send-your-name/orion-first-flight/
http://mars.nasa.gov/participate/send-your-name/orion-first-flight/?s=co...
http://mars.nasa.gov/participate/send-your-name/orion-first-flight/?s=co...
In a response letter to the securityweek.com team the nasa officials wrote back "Approved names were then converted into a form for putting on the chip through e-beam lithography - not only is there no issue of corrupting the chip, but there is no computer-based or other use of the chip so there is no risk in any case. All entries are exported and reviewed by a team of people so it's unlikely that unauthorized data made it through".
In a short interview in the morning benjamin said "The issue has no evil impact to the hardware itself because of being transported with a non connected chip were the payload name is saved even if it is the first unauthorized exploit code (payload) in space. The issue has been reported with responsible disclosure and cooperation of us cert to ensure there is no security risk at the end. Whether the nasa team approved the hack fully or not can never be a confirmed since the full chip table input becomes visible."
Mejri's exploitcode (payload) spent four hours and 24 minutes in two elliptical orbits of Earth, with an apogee of 5800 kilometres.
View: (other test payload that was confirmed) http://mars.nasa.gov/participate/send-your-name/orion-first-flight/?s=confirm&cn=344616
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1339
Magazine Article: http://magazine.vulnerability-db.com/?q=articles/2014/11/05/nasa-mars-orion-program-researcher-reveals-vulnerability-boarding-pass
Reference(s):
http://www.securityweek.com/exploit-payload-possibly-made-it-nasas-orion-spacecraft
http://www.theregister.co.uk/2014/12/08/orion_nasa_hack/
http://news.softpedia.com/news/Bogus-IDs-aboard-NASA-s-Orion-Spacecraft-466701.shtml



Comments
Add new comment | VULNERABILITY MAGAZINE - Bug Bounties,
Having read this I thought it was rather informative. I appreciate you finding the time and effort to put this article together. I once again find myself personally spending way too much time both reading and commenting. But so what, it was still worth it!
wowzers
very good ya.
Add new comment