PayPal Bug Bounty - Ethernet Portal Backend Vulnerability in User Profile Values
PayPal Inc Bug Bounty Program Rewards Researcher for Ethernet Portal Backend Vulnerability in User Profile Values
In 2013 the founder of the vulnerability laboratory "benjamin kunz mejri" discovered a vulnerability inside of the backend service of the paypal inc. The issue was tricky to exploit and located on the application-side of the paypal web-server account system.
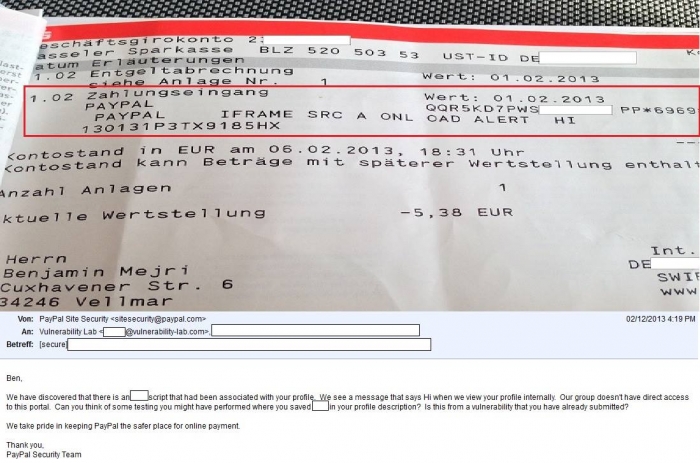
In the morning of the 2013-12-02 the security researcher got notified by a secure mail service of an official paypal security manager. The mail reveals the details of an incident and the vulnerability laboratory started investigation in the reverse analysis because of the late response.
In a reverse analysis after several legal testings against the paypal inc infrastructure, we came to decision to test a new kind of scenario against the service api. Our team tried to blind evade and bypass the online service filter validation of the backend listings with main values of the profile. Means whenever a moderator or admin is watching the profile of the paypal inc db listed user in the ethernet, the persistent injected code executes. In the attack scenario we injected malicious test codes with scripts in the most attractive values of the paypal user profile database -> `bank account owner/holder (cardholder)`, `name/surname`, `companyname` and of course the `account owner`. In the morning (2013-02-12) paypal responded with the following mail to us (review poc).
The security risk of the application-side validation vulnerability in the security card system module is estimated as critical with a cvss (common vulnerability scoring system) count of 8.9. Exploitation of the application-side remote web validation vulnerability requires a low privileged paypal account with restricted access and no user interaction. Successful exploitation of the vulnerability results in session hijacking, account database compromise, dev/admin account compromise, external redirects and persistent manipulation of affected or connected module context.
The following steps shows how the issue was reproduceable for the developer team of paypal inc.
1. I included script code to main values which are saved and could be displayed in the admin or moderator section
Note: A moderator or admin only view important main customer details like compaynames, owners and co.
2. I came to the decision to use the (lucky choosen) values account owner, address, companyname and bank account owner.
3. A mathematic analysis showed me that it must be possible in any way for you guys to watch this values when updating or editing data
Note: A reserve tip came up to me 5 days ago when the women at the support phone was helping me to reset my account and can't read my data. Now i understand :)
4. Then i implemented the vulnerable values saved them in the main profile and after some month i changed them with the new business account
Note: Some of the context is stable saved even if not visible for the user because after the update the context must normally be updated or deleted
5. I was still waiting since one of paypal moderators or admins confirm the issue by watching the blind injected context in the backend application
6. Result was the following mail today after my seperate tests >

7. Successful reproduce of the remote vulnerability!
The vulnerability has been patched after several deep analysis of the paypal inc security team during the year to protect the internal portal service. It is not a blame for paypal to ask the researcher whats going on when a major ticket pops-up. The mail helped to detect the blind coordinated pentests against the filters and the manufacturer patched the major remote vulnerability.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=1278
PayPal Inc Security UID: cDc49dT
Press|News Article: (Eduard K.) http://www.securityweek.com/researchers-find-vulnerability-internal-paypal-portal



Add new comment