Remote Code Execution Vulnerability discovered in Yahoo, Microsoft MSN & Orange - Bug Bounty Ebrahim Hegazy
Ebrahim Hegazy (Bug Bounty) - Remote Code Execution in Yahoo, Microsoft MSN & Orange
Today I will be talking about a “Unauthorized Admin Access” that led to “Remote Code Injection” on many domains of “Yahoo“, “Microsoft MSN“ and “Orange“.
Excited? Good, now let’s dive into the details.
During my researches in #Yahoo Bug Bounty Program, I found myself in a Yahoo.net domain:
http://mx.horoscopo.yahoo.net/ymx/
I tried to find the admin panel for that domain name, so I found myself in below page:
http://mx.horoscopo.yahoo.net/ymx/editor/
The thing is, it dosent ask me for any login credentials!
Yes I just found myself in the admin panel without asking for a login credentials, this what is called “Unauthorized Admin Access AKA Indirect Object Reference“.
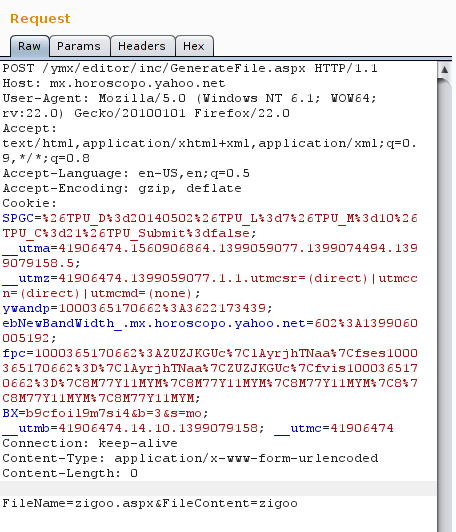
So, You see that list of files on the left side? I had an option to create a new “ASPX” file. I tried to intercept the POST request sent when trying to create a new file, So, here is what I got.

As you see, it’s a POST request to the below URL with below POST data:
http://mx.horoscopo.yahoo.net/ymx/editor/inc/GenerateFile.aspx
POST: FileName=zigoo.aspx&FileContent=zigoo
Yes, You’ve only to provide the new created file name and whatever content you want to add!!

So, I did create a file named “zigoo.aspx” with my name as a content “zigoo”:
 Ofcourse I could have created that file with a code to give me Remote Command Execution Privilege, but I saw it was a good/enough POC.
Ofcourse I could have created that file with a code to give me Remote Command Execution Privilege, but I saw it was a good/enough POC.
Now what?
I tried to check if there is any other Yahoo domains that were affcted by the same vulnerability?
I searched for the same sites hosted on the same server and I found below sites on the same server:
#Yahoo:
http://pe.horoscopo.yahoo.net
http://mx.horoscopo.yahoo.net
http://ar.horoscopo.yahoo.net
http://co.horoscopo.yahoo.net
http://cl.horoscopo.yahoo.net
http://espanol.horoscopo.yahoo.net
#Microsoft MSN:
http://astrocentro.latino.msn.com/
http://astrologia.latino.msn.com/
http://horoscopo.es.msn.com/
http://horoscopos.prodigy.msn.com
#Orange:
http://astrocentro.mujer.orange.es
So, what was the shocking issue here?
The shocking thing here is that I don’t have to upload/create my page on every domain to make a good POC!
Because once I created that page on one of the Yahoo domains mentioned above, I found that my page has been created on ALL SITES hosted on the same server, Yahoo, MSN, Orange and others!
Imagine a Black-Hat with this vulnerability, creating his “Iframed” aspx page with it’s malicious content on such highly ranked/trusted domains of Yahoo.net MSN.com Orange.es and more!!
How did it happen?
I tried to contact Microsoft regarding this question, they said “We will investigate it”
Till they investigate it, below is my expectation:
It’s A CDN(Content Delivery Network) Service for astrology that cashes the same content to render it for the sub domains of that mentioned vulnerable domains, So all files on one domain will be shown on all other domains on the server.
Below video shows the POC file that was created on all the above mentioned domains.
What happened after the report?
#Yahoo_Case, Thanks to R.Martinz for speeding up the fix release,
Yahoo does not pay bounties for vulnerabilities found in Yahoo.net, but they decided to reward me for this vulnerability since it’s a Critical Vulnerability that Affects 6 Yahoo domains.

#MSN_Case, I tried to get any reward from Microsoft for reporting such Critical Vulnerability that affects 4 MSN domains, but as you all know how Microsoft Acts like!! Ofcourse you all could expect what happened here :D
#Orange_Case, It was hard as hell to get in touch with Orange! till I gave up!, But fortunately, the fix that was released by Microsoft has fixed the issue on all the server domains including Orange.
@Zigoo
Author: https://www.vulnerability-lab.com/show.php?user=Ebrahim%20Hegazy




Add new comment