German Telekom Bug Bounty – 3x Remote Vulnerabilities
German Telekom Bug Bounty – 3x Remote Vulnerabilities
The laboratory researcher Ibrahim Mosaad H. El-Sayed (the_storm) participated from december since february in the official German Telekom Bug Bounty Programme. Between his exploitation and documentation phase the scope has been restricted by the telekom (critical only!). As direct reaction ibrahim focused to report only high/critical severity remote vulnerabilities.
The first remote vulnerability is a code execution bug, the second vulnerability is a pre-auth remote sql injection issue and the third security problem was an arbitrary file upload bug. The severity of all 3 issue was high to critical and the reward amount per issue was set to 1000€ (3x 1000€).
1. Remote Code Execution
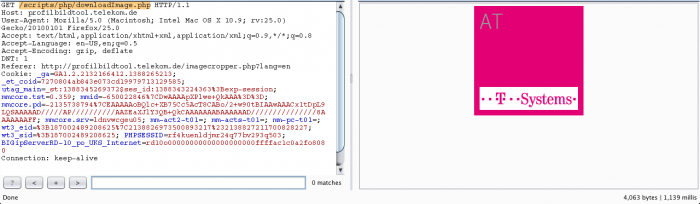
The Remote Code Execution vulnerability is located in the `downloadImage.php` and `process.php` file. The vulnerable parameter value is the `locCode`. Remote attackers can manipulate the POST method request with the ImgType values to inject/execute own php commands.
Vulnerable Module(s): [+] telekom.de (profilbildtool)
Vulnerable File(s): [+] downloadImage.php [+] process.php
Vulnerable Parameter(s): [+] locCode > AT




2. Remote Pre-Auth SQL Injection Vulnerability
A remote SQL Injection web vulnerability has been discovered in the official Telekom (English) website web application. The vulnerability allows remote attackers to inject unauthorized own sql statements to compromise the affected web-application or dbms. The sql injection vulnerability is located in `englishtest2004/test.asp` file of the englishtest2004 module (path). After executing the query through the test.asp page, the query`s result can be seen from a `500 error` returned by the `test.asp` page. The connected vulnerable parameter in the `test.aspx` file is `mailbody` that is passed through the POST method request.
The SQL injection bug is in the INSERT statement. Other paramaters like VORNAME, Email, PLZ, TELEFON can be accessed by usage of a malicious insert statement. The security risk of the sql injection vulnerability is estimated as critical with a cvss (common vulnerability scoring system) count of 8.3(+).
Exploitation of the remote sql injection web vulnerability requires NO user interaction or a privileged web-application user account. Successful exploitation of the remote pre-auth sql injection results in dbms, web-server and web-application (context) compromise.
Vulnerable Module(s): [+] /englishtest2004/
Vulnerable File(s): [+] /englishtest2004/test.asp
Vulnerable Parameter(s): [+] mailbody



3. Arbitrary File Upload Vulnerability
An arbitrary file upload web vulnerability has been discovered in the official German Telecom Profile Picture tool website web application. The web vulnerability allows remote attackers to upload an arbitrary (malicious) file to compromise the dbms, website or web-server system.
The arbitrary file upload vulnerability is located in `/scripts/php/process.php` file. After executing the query through the process.php page, the query result can be seen from `/scripts/php/downloadImage.php`. Remote attackers are able to manipulate the POST method request with of the process.php file to upload unauhorized own malicious files.
Exploitation of the remote web vulnerability requires no user interaction and also no privileged web application user account. Successful exploitation of the arbitrary file upload vulnerability results in web-server, web module, website or dbms compromise.
Vulnerable Module(s): [+] profilbildtool
Vulnerable File(s): [+] /scripts/php/process.php






End of january the first 3 remote vulnerabilities was patched. The coordination has been navigated by markus a advanced telekom security team manager from germany. The disclosure was coordinated and in cooperation with the german telekom & the connected official security team.
2013-12-30: Researcher Notification & Coordination (Ibrahim Mosaad El-Sayed) 2013-12-30: Vendor Notification (Telekom CERT Security Team) 2014-01-02: Vendor Response/Feedback (Telekom CERT Security Team) 2014-01-24: Vendor Fix/Patch (Telekom Developer Team - Reward 3 x 1000€uro)
Statement Ibrahim Mosaad h. El-Sayed (VL Core Team) to Softpedia:
Telekom is one of the best bug bounty programs I have been working with. What makes them outstanding from other bug bounty programs is their communication with the researchers. They are fast in fixing the bugs and fast in paying the bounty which keeps us, hackers, always interested to find more and more. Also whenever we need clarification about something we get the answer in max 24 to 48 hours. I think they know what they are doing. I just wish if they can some how expand the program to include other critical bugs like persistent input validation and file inclusion bugs. SQL and RCE are not always and only the crticial bugs in a website to make damage. A system can be owned with some filter bypass and persistent cross site issue the same way like with a sql injection or arbitrary file upload. As far as our lab core team successful participate in the program, we will continue the cooperative & coordinated disclosure with the german telekom. Thanks@Telekom

Remote Code Execution: https://www.vulnerability-lab.com/get_content.php?id=1174
Remote SQL Injection: https://www.vulnerability-lab.com/get_content.php?id=1177
Remote Arbitrary File Upload: https://www.vulnerability-lab.com/get_content.php?id=1176
Softpedia: softpedia.com/Expert-Finds-SQL-Injection-and-RCE-Vulnerabilities-in-Deutsche-Telekom-Systems



Add new comment