0Day Vulnerabilities in Microsofts Skype Account System
0Day Vulnerabilities in Microsofts Skype Account System
Today we want to talk about the last microsoft 0day vulnerabilities in the core of the skype account system. Last days we published two amazing remote vulnerabilities in microsofts official skype account service application affecting 670+ million user accounts. Both vulnerabilities has been discovered to the microsoft security response center (MSRC ID: 13050[bc] & 13175).
The first vulnerability was an account reset vulnerability in the account login system of skype.
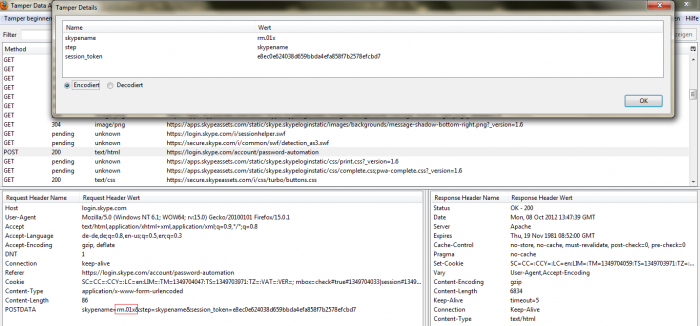
The critical application vulnerability was located in the recovery account function of the skype account service application. In the recovery function is an auth request bound to the account session using the json form with jquery and the value of the intercape. The request itself is not sanitized. The value only check if exist and if empty but not validate the context again. The attacker can bypass the token protection via live session tamper to reset any account by exchanging the values local to his own. Exploitation requires `processing to request` via jquery implement JSon form request.
Vulnerable Section(s):
[+] Account Application Service - https://login.skype.com/account
Vulnerable Module(s):
[+] Recovery Function - https://login.skype.com/account/password-automation
Vulnerable Module(s):
[+] JSon & jquery Since yet it is only manually possible to exploit the remote vulnerability by using a session tamper tools like tamper data.
A remote attacker can, for example bypass the token protection with values like “*/+[New Account Details] or [New Account Details]+/*“ to reset random skype application accounts or infiltrate specific choosen account by changing usernames or passwords.
A laboratory researcher produced a security video to record the vulnerable session parameters and requests ...



Exploitation Techique(s):
[+] Bypass the Skype Recovery Page (request tamper) to New Pass or Reset [+] Bypass token protection via not empty value with positiv value(s) to match
[+] Hold the request via tamper include own values to setup the new password The vulnerability can be exploited by remote attacker without required user inter action. Successful exploitation of the critical remote vulnerability result in skype account compromise, skype account infiltration, mail information disclosure or lead to skype user account manipulation.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=720 The secound vulnerability was bound to the password reset submission and tracked by MSRC (MSRC ID: 13175). The high severity application vulnerability was located in the recovery account function of the skype account service application. In the recovery notification mail function is a GET request as link which expires after 6hours. The bug is located in the reset function when processing to load the token_expire parameter with value 1 (invalid). Attackers can change the stable url by using a zero (0+ / +0) to bypass the checked token_expire value (parameter) to get a valid link with the expired session.
Vulnerable Module(s):
[+] Recovery/Reset Function - https://login.skype.com/intl/de/account/password-reset-request
Vulnerable Parameter(s):
[+] token_expired Standard: account/password-reset-request?token=621d8b0e773cc298a149a1b916118114&mode=&token_expired=1
Manipulated: account/password-reset-request?token=621d8b0e773cc298a149a1b916118114&mode=&token_expired=(+)0




The vulnerability can be exploited by remote attackers without required user inter action and without privileged user account.
The secound issue has also been recorded in a live-hacking session video to demonstrate the skype company and dev team the exploitation method.
The skype password reset function has been disabled when skype was processing to patch the issue. The resets has been disabled to prevent the problem because we informed them very early about the security vulnerabilities. The issues has been addressed within some hours and the reset function is back available. The disclosure process of the vulnerabilities has been coordinated by Brandon & Nate (MSRC|Manager). The reproduce and patch has been observed by Jüri S. (Skype|Manager) in cooperation with Benjamin Kunz Mejri (Vulnerability-Lab) and Chokri Ben Achour (Vulnerability-Lab).
MSRC ID: 13050[bc]
2012-10-01: Researcher Notification & Coordination (VL - Benjamin Kunz Mejri) 2012-10-11: Vendor Notification (Skype Security) 2012-10-11: Vendor Notification (MSRC) 2012-10-23: Vendor Response/Feedback (MSRC) 2012-11-12: Vendor Fix/Patch *Hotfix & temporary disabled Password Recovery (Skype) 2012-11-16: Public Disclosure (Vulnerability Laboratory)
MSRC ID: 13175
2012-10-31: Researcher Notification & Coordination (VL - Benjamin Kunz Mejri) 2012-11-01: Vendor Notification (MSRC) 2012-11-01: Vendor Response/Feedback (MSRC) 2012-11-12: Vendor Fix/Patch (Skype) 2012-11-15: Public Disclosure (Vulnerability Laboratory)
Note: The core auth system bugs of chokri and benjamin is not bound to the 2nd mail auth bug issue of the russian researcher dimitry.
The following picture shows the patched token expire function and parameter with a new exception-handling (2012-11-16)

Press/News: http://news.softpedia.com/news/Skype-0Day-Vulnerability-Allowed-Hackers-to-Change-the-Password-of-Any-Account-Video-307672.shtml http://www.scmagazine.com.au/Tools/Print.aspx?CIID=323271



Add new comment