PayPal Inc Bug Bounty Submission #9 – Analysis & Review
PayPal Inc Bug Bounty Submission #9 – Analysis & Review
In the last month our Team participated multiple times in the official paypal bug bounty program. Karim H.B., Benjamin Kunz Mejri, Ibrahim El-Sayed and a lot of international friends joined large hacking session and discovered bugs to paypal inc. Today we want to talk about the first complete fixed and released issue in the paypal core application. The vulnerabilities has been discovered by Benjamin Kunz Mejri the founder of the vulnerability-labs 2 days ago.
Multiple persistent input validation vulnerabilities are detected in the official Paypal ecommerce website content management system (Customer/Pro/Seller). The bugs allow remote attackers to implement/inject malicious script code on the application side (persistent) of the paypal web service.
The vulnerability was located in the company profile input fields with the bound vulnerable address_id, details (mail) & companyname parameters. The bug affects the important user profile listing, the address listings & security notification (mail). The secound persistent vulnerability is also located in the mail security notification (delete address) module with the bound vulnerable companyname parameters.
Vulnerable Type(s):
[+] Customer/Pro/Seller Accounts
Vulnerable Section(s):
[+] Mein Konto (My Account) > Mein Profil > Addresse hinzufügen oder Bearbeiten
[+] Register > Account > Details
Vulnerable Module(s):
[+] Companyname (Geschäftsinhaber)
Vulnerable Parameter(s):
[+] detailsAffected Section(s): [+] User Profile - Geschäftsinhaber - User Profil (Mein Konto) Listing

The vulnerability can be exploited by remote attackers with low required user inter action and privileged Customer/Pro/Seller account. Successful exploitation of the vulnerability can lead to session hijacking (customers), account steal via persistent web attack, persistent phishing or stable (persistent) context manipulation in all sections/module were the vulnerable companyname get displayed.
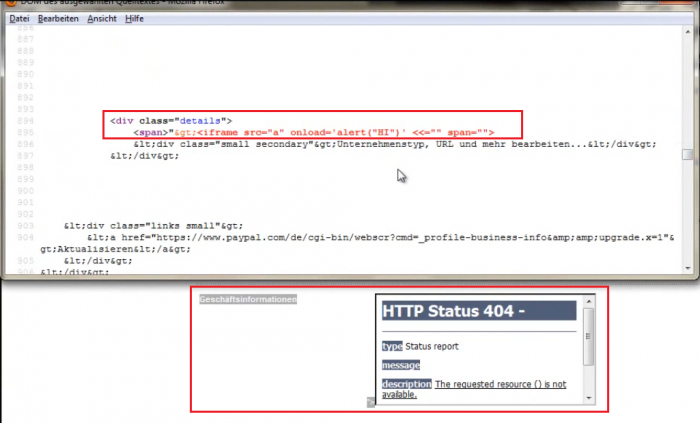
Review: User Profile - Geschäftsinhaber - User Profil (Mein Konto) Listing (Script Code Execution)
<div class="details"> <span>"><[>INJECTED PERSISTENT SCRIPT CODE AS COMPANY NAME!<])' <<="" span=""> <div>Unternehmenstyp, URL und mehr bearbeiten...</div> </div>
The next step was to use the vulnerable module to identify other vulnerabilities in other sections. After Benjamin injected script code and identified the first vulnerability another issue came up. He tried to delete the malicious persistent companyname which results in a paypal mail. When he was processing to check the mail the persistent script code of the companyname got unsanitized executed out of the mail body.
Vulnerable Parameter(s):
[+] companynameAffected Section(s): [+] Security Notification Mail
Sie haben Ihre Adresse geändert </span></h2></td></tr></tbody></table>
<p>Guten Tag, >"<[>INJECTED PERSISTENT SCRIPT CODE AS COMPANY NAME!<]>!</p>
Wir möchten nur kurz bestätigen, dass Sie eine Adresse in Ihrem PayPal-Konto geändert haben.
<h3>Hier die Details:</h3> <!--[if gte mso 9]><style>.simpleSummaryTable {cell-spacing:5px !important;
font:0.75em Verdana, Arial, Helvetica, sans-serif !important;}</style><![endif]-->
Next to the identification process of the secound bug (mail encoding vulnerability) he tried to review the address in a main bar of the status section. The result was the next persistent script code execution out of the paypal main core context.
Vulnerable Parameter(s):
[+] address_idAffected Section(s): [+] Adresse Profil - Listing
Review: Adresse Profil - Listing (Script Code Execution)
<div id="messageBox"></div><div id="main"><div><div><table id="viewtable" summary="street addresses" cellspacing="0"><colgroup><col width="35%"><col width="25%"><col width="*"></colgroup><thead><tr> <th>Adresse</th><th>Zugehörige Kreditkarten </th><th>Status</th></tr></thead><tbody><form method="post" action="https://www.paypal.com/de/cgi-bin/webscr?cmd=_profile-address-submit& dispatch=5885d80a13c0db1f8e263663d3faee8d8494db9703d295b4a2116480ee01a05c" class=""></form> <tr><td><input name="return" value="" type="hidden"> <input name="address_id" value="Qf3ntYQLgs25E1DBKd3un5JfZvip1l3kwgj2iBMne1UpaAD8yEcic32OZN0" type="hidden"><input name="card_count" value="0" type="hidden"><span>"><[>INJECTED PERSISTENT SCRIPT CODE AS COMPANY NAME!<])' <<br="">
Paypal Inc fixed the vulnerabilities as part of the official bug bounty program. It took a bit longer to patch them because of a lot different locations and tests around.
2012-07-06: Researcher Notification & Coordination 2012-07-06: Vendor Notification 2012-07-07: Vendor Response/Feedback 2012-09-20: Vendor Fix/Patch 2012-10-02: Public Disclosure
The security risk of the persistent script code inject vulnerabilities was estimated as high(+). Successful exploitation of the vulnerability can lead to session hijacking (customers), account steal via persistent web attack, persistent phishing or stable (persistent) context manipulation in all sections/module were the vulnerable companyname get displayed (frontend & backend). Since yet the vulnerability-lab team reported over 30 vulnerabilities to the paypal inc security team.
Advisory:
https://www.vulnerability-lab.com/get_content.php?id=646
PRESS/NEWS Reference(s):



Add new comment