FlashFXP Software Client – Buffer Overflow Vulnerability
FlashFXP Software Client – Buffer Overflow Vulnerability
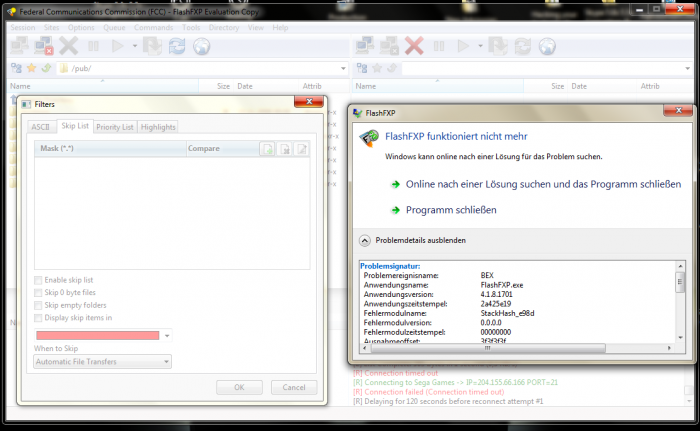
The vulnerability laboratory researcher Benjamin Kunz Mejri discovered a new issue on the famous FLashFXP Software Client by OpenSight Software. The vulnerability is located when processing to force a ListIndex Out of Bound(s) exception which allows to overwrite ecx & eip of the affected software process. Successful exploitation can result in process compromise, execution of arbitrary code, system compromise or escaltions with privileges of affected vulnerable software process.
The flaw is a direct result of a fixed length buffer being used in the TListBox control and the lack of range checking. The code assumes that the string returned by the listbox control will be less than 4097 characters.

It uses a fixed size buffer of 4096 bytes and any text longer than this will overflow and overwrite the memory beyond it.

The TComboBox control also suffers a similar flaw.

We recorded a live video session to explain how to exploit the vulnerability on the local way.
FlashFXP - Filters Exception Buffer Overflow Vulnerability
Advisory: http://www.vulnerability-lab.com/get_content.php?id=462



Add new comment