Kaspersky IS & AV 2011/2012 – Memory Corruption
Kaspersky IS & AV 2011/2012 – Memory Corruption
About 1 year ago i discovered a local vulnerability to a product vendor kaspersky. The vulnerability was a memory corruption bug in the antivirus and internet security product. The bug was located on the .cfg file import to load configuration files. I used a new software to identify a pointer corruption which allows to read or write. The vulnerability can be exploited by local low privileged user account or local system attackers. Successfull exploitation results in a critical software crash in combination with the bound modules like sidebar or the kis/kav browser addon.
In the last week we saw a nice discussion on the chip forum were people talking about Eugene Kasperskys reaction regarding to the security advisory of benjamin kunz mejri (Rem0ve). We upgraded our pictures with the newst version after we saw the discussions on chip.de, eugene's twitter account & other communities. It is not okey to say your customers the bug is fixed 1 year ago, when we show real session pictures of all versions in 2011a-d till 2012 a.b.c.d.f.g. We will now show some real pictures of the test from the 2011 a.b version over the 2012 a.b.c version till the last 2012 a.b.c.d.e.f.g of Internet Security & AntiVirus. Choon my neutral analyst and friend from malaysia is a well known person on different security and hacking events. He should check again the newst version of Kaspersky 2012 Internet Security to make sure this is really the truth.

The last version of Kaspersky Internet Security 2012 a.b.c.d.e.f.g.

Software Kaspersky 2012 Internet Security - Successful Exploited by Choon via PoC

Kaspersky Internet Security 2012 a.b.c.d.e.f.g. - Software Crash AV 2012

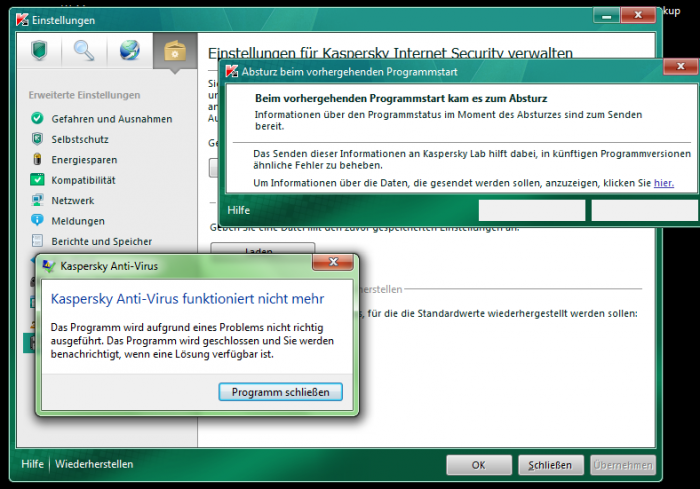
Kaspersky Internet Security 2012 a.b.c. also vulnerable

Kaspersky Internet Security 2012 a.b.c.d.e.f.g. verified as vulnerable


Kaspersky Internet Security 2011 a.b.c.d.


Kaspersky Bug Reporter alias Absturzmelder


2011 Windows 7 x64 - Software Crash

Debugging - Catching the Issue

Crash Report in KIS 2011 -11.0.1.400 (July 2011)

Crash Report in KIS 2011 -11.0.1.400 (July 2011)

Bug Report in KIS 2012 - a.b.c. (November 2011)

Bug Report in KIS 2011 - 11.0.0.232 (MAY 2011)

Shows the exception-handling when you go the wrong way :)

Allows to load a .cfg image without password

At least we can say ... the bug is not 100% fixed. Till now the Proof of Concept is not publicly available. We do not want to get any troubles with kaspersky but this is something we should show to everybody. It is not okey to say the issue is fixed 1 year ago because we provided best quality pictures of March2011, July2011, September2011 & now January 2012. If we publish an advisory as issue it will be ever the truth.
Comment by Kaspersky Developer: You can also use a removal tool to delete the software on a local system.
Comment by Rem0ve: A removal tool is no memory corruption in the software process which allows to crash all instances on a legal way of use. I do not understand this comment because of the fact it sounds completly wrong to a hacker, coder or researcher. using a removal software is a big difference then to exploit a pointer vulnerability on a security software.
;)



Add new comment