Microsoft Bulletin MS2013-067 – SharePoint 2013 Online
Microsoft Bulletin MS2013-067 – SharePoint 2013 Online
This week microsoft published the new security bulletins of 2013 september. In February the issue has been reported to the microsoft security response centers responsible - public disclosure program. The issue was for fail publish 2 month ago without full details, references and ids. After a little patch of our internal disclosure procedure system, microsoft accepted the issue for the bulletin program acknowledgment. The vulnerability was created to confirm the exist of the possibility to inject script code to elevate the sharepoint online 2013 software user privileges. The inject comes up from the online service and gets executed persistent in the software core.
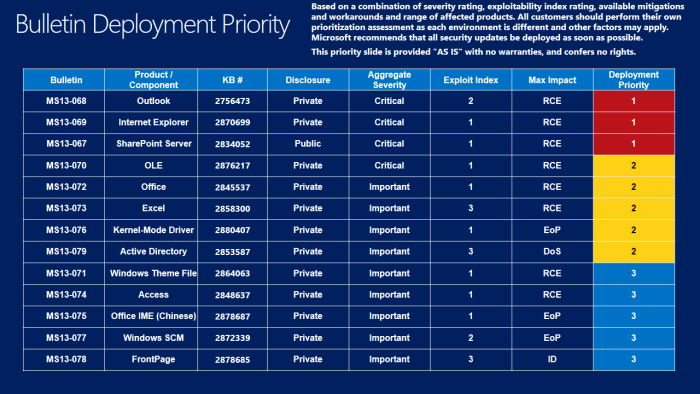
Lets review first the full update listing of the september #1 security bulletins with id and severity.

[caption id="" align="alignnone" width="630"]

Sharepoint Online Software 2013 (Cloud)[/caption]
The vulnerability is located in the `Sharepoint Online Cloud 2013 Service` section when processing to request the `Berechtigungen für den Metadatenspeicher festlegen` module with manipulated ms-descriptionText > ctl00_PlaceHolderDialogBodySection_ PlaceHolderDialogBodyMainSection_ValSummary parameters. The persistent injected script code execution occurs in the main `invalid BDC Übereinstimmung` web application exception-handling.
Vulnerable Service(s): Microsoft - Sharepoint Online 2013 Software (Cloud) Vulnerable Module(s): Berechtigungen für den Metadatenspeicher festlegen - BDC Metadatenspeicher zuweisen Vulnerable Parameter(s): ms-descriptionText ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_ValSummary TA_ManageBDCPermissions_data Affected Module(s): BDC Übereinstimmung > Exception Handling
The vulnerability can be exploited with a low (restricted) privileged application user account and low or medium required user interaction. Successful exploitation of the vulnerability result in persistent session hijacking, persistent phishing, stable external redirect, stable external malware loads and persistent vulnerable module context manipulation.
The persistent input validation web vulnerability can be exploited by remote attackers with low required user interaction and low privileged sharepoint cloud application user account. For demonstration or reproduce ...
Review: Berechtigungen für den Metadatenspeicher festlegen - Summery> BDC Übereinstimmung > Exception (TA_ManageBDCPermissions_data) <table border="0" cellpadding="0" cellspacing="0" width="100%"> <tbody><tr> <td> <span id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_LabelMessage"></span> </td> </tr> <tr> <td><span id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_LabelErrorMessage"> Fehler beim Versuch, 'IMetadataCatalog' eine Zugriffssteuerungsliste mit dem Namen 'ApplicationRegistry' zuzuweisen. Mindestens ein Benutzer oder eine Gruppe in der Zugriffssteuerungsliste muss über das Recht 'SetPermissions' verfügen, um das Erstellen eines nicht verwaltbaren Objekts zu verhindern.</span></td> </tr> <tr> <td> <div id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_ValSummary" style="color:Red;">Mindestens ein Fehler auf der Seite. Beheben Sie Folgendes, bevor Sie fortfahren:<ul><li>Es wurde keine exakte Übereinstimmung für <iframe src="TA_ManageBDCPermissions_data/vlab.js">%20%20%20 %20"><[PERSISTENT INJECTED SCRIPT CODE!]") <%20%20%20%20"><[PERSISTENT INJECTED SCRIPT CODE!]") < gefunden.</li></ul> </div> </td> </tr> </table> <table border="0" cellspacing="0" cellpadding="0" width="100%" class="ms-authoringcontrols"> <tr> <td> ---------- <table border="0" cellpadding="0" cellspacing="0" width="100%"> <tbody><tr> <td> <span id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_LabelMessage"></span> </td> </tr> <tr> <td><span id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_LabelErrorMessage"> Fehler beim Versuch, 'IMetadataCatalog' eine Zugriffssteuerungsliste mit dem Namen 'ApplicationRegistry' zuzuweisen. Mindestens ein Benutzer oder eine Gruppe in der Zugriffssteuerungsliste muss über das Recht 'SetPermissions' verfügen, um das Erstellen eines nicht verwaltbaren Objekts zu verhindern.</span></td> </tr> <tr> <td> <div id="ctl00_PlaceHolderDialogBodySection_PlaceHolderDialogBodyMainSection_ValSummary" style="color:Red;">Mindestens ein Fehler auf der Seite. Beheben Sie Folgendes, bevor Sie fortfahren:<ul><li>Es wurde keine exakte Übereinstimmung für <iframe src="TA_ManageBDCPermissions_data/a.txt">%20%20%20%20"><[PERSISTENT INJECTED SCRIPT CODE!]) <<%20[PERSISTENT INJECTED SCRIPT CODE!]) < gefunden.</li></ul> </div> </td> </tr> </table> <table border="0" cellspacing="0" cellpadding="0" width="100%" class="ms-authoringcontrols"> <tr> <td>
--- Exception Handling (DE) --- Sie können Administratoren des BDC-Metadatenspeichers zuweisen, indem Sie unten Berechtigungen festlegen. Fehler beim Versuch, 'IMetadataCatalog' eine Zugriffssteuerungsliste mit dem Namen 'ApplicationRegistry' zuzuweisen. Mindestens ein Benutzer oder eine Gruppe in der Zugriffssteuerungsliste muss über das Recht 'SetPermissions' verfügen, um das Erstellen eines nicht verwaltbaren Objekts zu verhindern. Mindestens ein Fehler auf der Seite. Beheben Sie Folgendes, bevor Sie fortfahren: Es wurde keine exakte Übereinstimmung für ... [Injected Context] ... gefunden/festgestellt. Sie können Administratoren des BDC-Metadatenspeichers zuweisen, indem Sie unten Berechtigungen festlegen.
[caption id="" align="alignnone" width="630"]

Persistent Script Code Inject - Exception Handling 1[/caption] [caption id="" align="alignnone" width="630"]

Persistent Script Code Inject - Exception Handling 2[/caption] [caption id="" align="alignnone" width="630"]

Persistent Script Code Inject - Exception Handling 3 # Verified![/caption]
Note: (US) After you’ve added your domain name to Office 365 to use with SharePoint Online and Lync Online, you can create email addresses, Lync Online accounts, and distribution groups that use your custom domain name. You can also use your domain name for a public website hosted on SharePoint Online but there are Use SharePoint Online on a custom domain together with other services.
Reference(s): https://benjamin23-admin.sharepoint.com/default.aspx https://benjamin23-admin.sharepoint.com/_layouts/bdc/TA_ViewBDCApplication.aspx
The vulnerability has been patched by the coordination of the microsoft security response center. The case manager of the issue was Brandon a well known ms security consultant. The vulnerability report matched 100% with the public responsible disclosure policy of microsoft security program.
2013-02-01: Researcher Notification & Coordination (Benjamin Kunz Mejri) 2013-02-06: Vendor Notification (Microsoft Security Response Center - MSRC) 2013-02-07: Vendor Response/Feedback (Microsoft Security Response Center - MSRC) 2013-09-11: Vendor Fix/Patch (Microsoft Security Bulletin) 2013-09-11: Public Disclosure (Vulnerability Laboratory)
The result of the successful coordination and cooperation was the public disclosure of the sharepoint online 2013 security bulletin.
Security Bulletin: MS13-067 http://technet.microsoft.com/de-de/security/bulletin/MS13-067
Microsoft Security Response Center (MSRC) ID: 14096 Advisory: https://www.vulnerability-lab.com/get_content.php?id=812
Press/News Reference(s): softpedia.com/news/POC-and-Details-Published-for-Microsoft-SharePoint-Sever-2013-Flaw-MS13-067-382088.shtml symantec.com/security_response/vulnerability.jsp?bid=62227&om_rssid=sr-advisories threatpost.com/critical-sharepoint-bulletin-top-priority-on-patch-tuesday heise.de/security/meldung/Microsoft-Patchday-Gefaehrliche-Mail-Vorschau-in-Outlook-1953906.html
We will soon come up with more security bulletin disclosure with msrc cooperation because of the already reported advisories in the last year.




Add new comment